Investigation Into Egregor Ransomware Reveals Unknown Aspects About its Operation
- Egregor has bitten the bait and carried out an attack on one of Morphisec’s testing environments.
- The researchers discovered more about how the group moves and what tools it deploys.
- Moreover, they have found a link between the Russian ransomware group and Revil and GandCrab.
The ‘Egregor’ ransomware group is one of the most active, successful, and intimidating out there, rising in notoriety quickly thanks to its uncompromising extortion mechanism, solid infection methods, and strong encryption scheme. Morphisec has decided to take a deeper look into how the group operates, its techniques for initial access, persistence, and exfiltration, and whether there’s any evidence linking them with other groups that had similar success in the past.
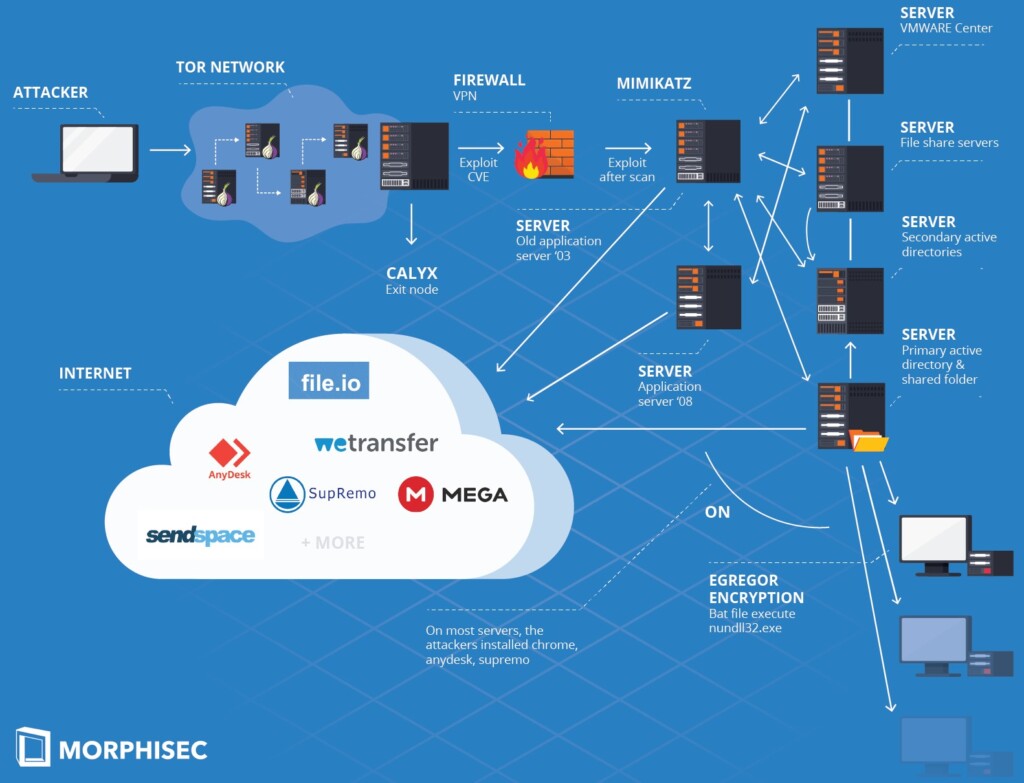
Starting with the infection process, the investigation shows that the Egregor group is exploiting a VPN vulnerability to access the target’s internal network through a Tor exit node, remaining well hidden. From there, the actors scan the network to find any vulnerable servers.
If they do, they use it as an entry point and then move laterally through file sharing, apps, virtualization, and fake updates. The exfiltration of the stolen data, which occurs before the encryption step, is done through legit services like WeTransfer, MEGA, SendSpace, etc.
A notable aspect of Egregor’s operation is the level of diligence they maintain during all stages. For example, when it comes to maintaining persistence, they use “AnyDesk” as a primary backdoor and also “SupRemo” as a backup. Also, the actors are careful with the planting of software and don’t just drop everything they got on every system they break into. For example, the “Mimikatz” credential collector is dropped only on the first vulnerable server they infect (patient zero).
To evade detection from powerful enterprise-grade AV solutions, the actors use the ‘AES.ONE’ file sharing platform. Through it, they drop the ransomware components, but not the other tools. These are fetched in 7zip archive form through the ‘File.io’ service, using a one-time download link.
Finally, there’s evidence that the actors are Russian-speaking people, which is consistent with previous findings. Morphisec has also found a link to the Revil and GandCrab groups through the username “Lalartu,” which has been used by those groups in the past. Of course, the actors use multiple “new users” to roam in the infected systems, and the researchers were able to restore wiped logs that indicated the simultaneous activity of three infiltrators.
Ransomware actors like Egregor are highly sophisticated, no doubt, and defending against them needs a holistic approach. Every network configuration opening, unpatched server, lack of MFA, absence of runtime zero trust preventive tech, and availability of admin privileges is serving as an entry point for these actors.
All they need is a single vulnerability, and they’re in. In any case, take regular backups, keep them isolated from your network, and make sure to test their integrity now and then.