Instagram Denies Data Breach After Password Reset Emails, 6.2M Accounts Added to HIBP
- Platform Denial: Instagram said no data breach occurred, attributing a recent influx of emails to a now-fixed bug that allowed an external party to trigger reset requests.
- Conflicting Intelligence: Security firm Malwarebytes alleges that PII belonging to 17.5 million accounts was exfiltrated and is currently available on the dark web.
- Separate observation: Meanwhile, the data breach notification service Have I Been Pwned added 6.2 million addresses to its database.
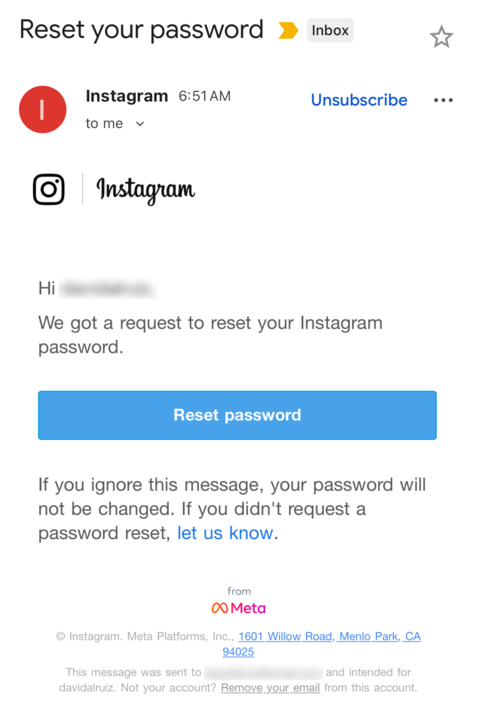
A significant volume of unsolicited Instagram password reset emails has caused confusion among the user base and prompted Meta-owned Instagram to issue a formal response, attributing the notifications to a bug and stating that its systems remain secure.
Yet, third-party security analysts such as Malwarebytes and Have I Been Pwned (HIBP) have presented conflicting data suggesting a potential large-scale compromise.
Official Response: Remediation of External Triggers
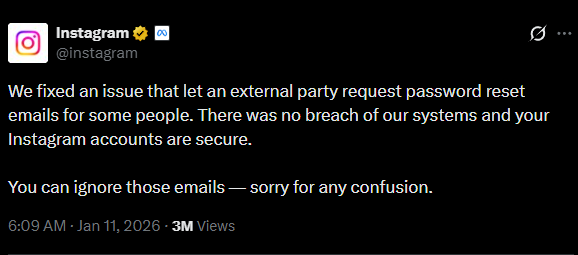
In a statement posted on the social media platform X, the company addressed the surge in suspicious activity. Instagram acknowledged that a technical issue had permitted an "external party" to request password reset emails for some app users.
The company confirmed that this vulnerability has been remediated and advised users to ignore the unsolicited communications. Crucially, the statement asserted there was no data breach, implying that while the reset mechanism was abused, internal databases were not accessed or exfiltrated.
The company did not disclose the identity of the external party or the specific mechanics of the vulnerability.
Alleged Large-Scale Data Exfiltration
Contrary to Instagram's assessment, antivirus provider Malwarebytes issued an alert via Bluesky claiming that cybercriminals had successfully stolen sensitive information associated with 17.5 million accounts.
Meanwhile, HIBP added 6.2 million email addresses to its breach database on January 11, which were allegedly scraped via an Instagram API and posted to a popular hacking forum.
Malwarebytes reported that this dataset is currently being monetized on dark web marketplaces and allegedly includes:
- usernames,
- physical addresses,
- phone numbers,
- email addresses.
This report raises serious cybersecurity concerns about whether the password reset activity was merely a symptom of a larger credential-scraping operation or a distinct event. Changing your password and ensuring Two-factor authentication is enabled are the best steps to protect your account.
As of now, the platform has not directly addressed the specific allegations regarding the millions of users allegedly exposed.
Google data breach reports saying 183 million user account credentials leaked circulated online in October, which the tech giant debunked.