‘iLnkP2P’ Vulnerabilities Affect Two Million IoT Devices
- iLnkP2P plagued by remote device ID guessing and cleartext data traffic interception.
- The number of IoT devices that are affected reach up to two million cameras and other smart products.
- The chances of having the vendors fix the problem are slim to none, so not using these devices is the best way to go.
From IP security webcams to baby monitors, and from smart doorbells to DVR solutions, there are millions of IoT devices that have one thing in common and that is the “iLnkP2P” software. This is a software that enables users of such IoT products to easily connect with them wherever they may be, using a smartphone app and an internet connection. The authentication is done once by scanning the device’s barcode, or by using a six-digit ID code that is usually on a tag placed on the device’s bottom or side, and from then on the communication takes place through P2P.
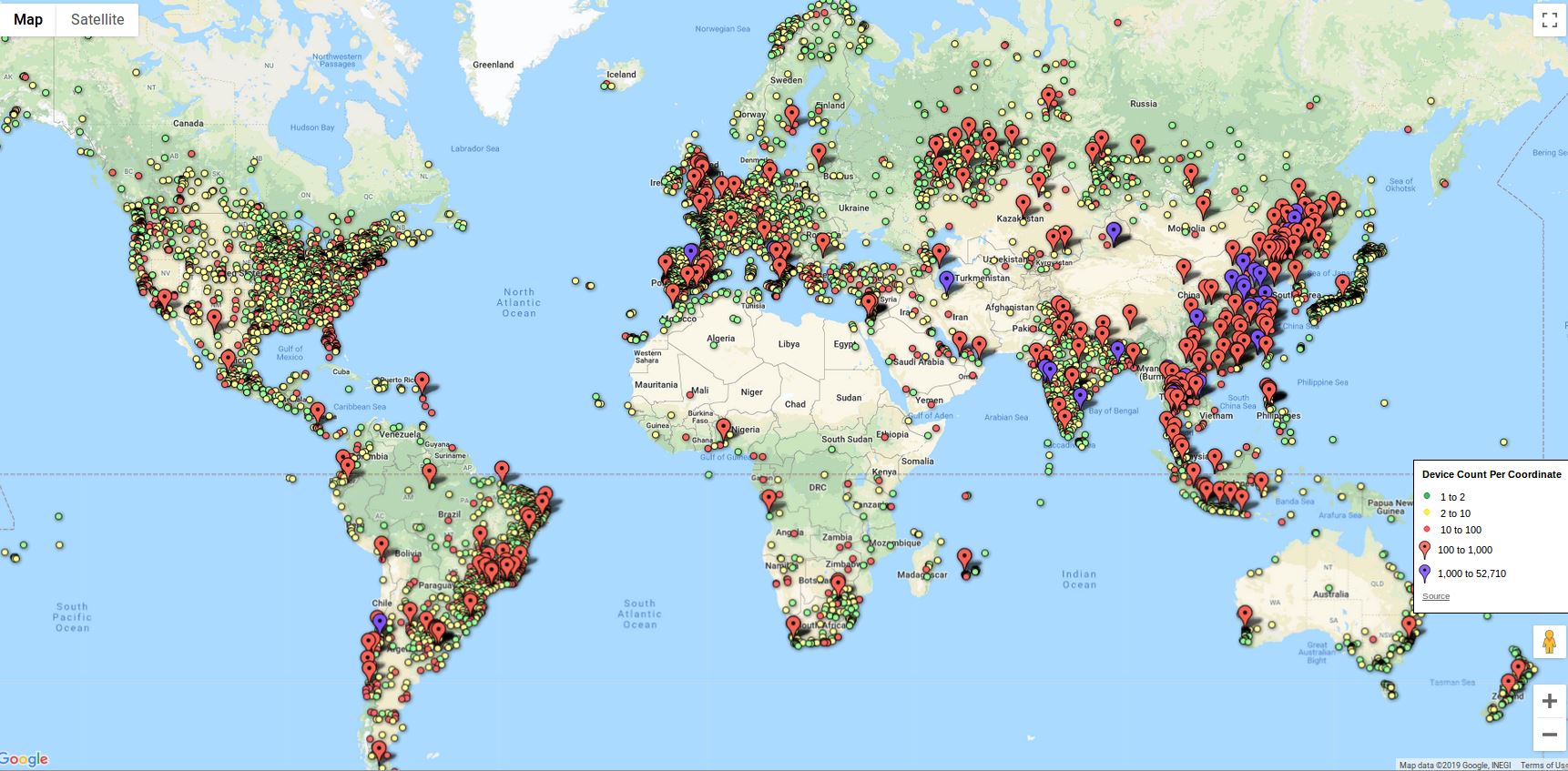
According to the findings of security researcher Paul Marrapese however, iLnkP2P is no safe at all, as entering a six-digit ID code and communicating via an unencrypted channel is grist for the mill of malicious actors who take aim at these devices. In fact, Marrapese created a proof-of-concept script and identified more than two million IoT devices that can be hacked, with the majority of them lying in China (39%), another 19% located in various European countries, and the US accounting for a significant 7%. The researcher’s script can exploit a built-in “heartbeat” functionality that IoT devices use to declare their presence in the network to exfiltrate the associated passwords.
image source: krebsonsecurity.com
For an attacker who has figured out what the device UID is, it would be possible to send spoofed heartbeat messages to the network and render those sent by the real IoT device useless. But guessing the passwords is not always a requirement, as too many users out there stay with the default “admin/admin” credentials, and the communication apps don’t compel them to change it upon the first connection with the device. That’s just bad practice that makes matters even worse for the users’ safety. The worst-case scenario implications of the hacking of these IP cameras concern video stream interception.
Getting a fix rolled out is highly unlikely, so not buying and not using Chinese IoT devices that advertise P2P communication capabilities would be your best bet. The vendors who are affected by this flaw are quite a few, and most of them are Chinese manufacturers who don’t respond to this type of reports. Moreover, the very website of iLnk is currently non-functional and compromised by a malicious HTML script that redirects visitors to a Chinese gaming website. Now, this says something about the developers of iLnk2P2 and how much they care about safety and security.
image source: hacked.camera
If you have purchased too many of those devices and don’t want to see your investment getting thrown out of the window, Marrapese suggests that you could set up a firewall that blocks traffic on the UDP port 32100, and that would prevent P2P communication.
The IoT devices that are vulnerable include but are not limited to the following models: CamHi, P2PWifiCam, iMega Cam, Webvision, P2PPIPCamHi, IPCAM P, Eye4, EyeCloud, VSCAM, PnPCam, E View7, P2PPIPCAM, CoolCamOp, APCamera, and P2PCam_HD.
Would you use P2P camera from a Chinese manufacturer? Let us know in the comments down below, and help us spread the word by sharing this post through our socials, on Facebook and Twitter.