The Identity of Hacktivist “VandaTheGod” Was Brought to Light
- “VandaTheGod” was burned by his own need to brag about hacks on social media.
- The hacktivist left numerous traces behind, and security researchers were able to figure out who he is.
- The Brazilian police may have arrested the man already, as all activity stopped at the end of 2019.
Hacktivist "VandaTheGod" is one of those actors who likes to draw attention with website defacements, leaking private documents, and even stealing and then selling credentials and credit card details. He has been active since at least 2013, causing headaches to entities based in Brazil, the Dominican Republic, Trinidad and Tobago, Argentina, Thailand, Vietnam, and New Zealand. But it seems that after about seven years, the veil of anonymity that shrouded the hacker has been lifted, as Check Point researchers managed to connect the pieces that they had gathered by monitoring the person for an extended period.
First, the researchers dug deeper into the social media profiles connected with each attack, primarily that one on Twitter. The tweets that were published there were in Portuguese, and oftentimes they contained mentions about the "Brazilian Cyber Army."
https://twitter.com/VandaTheGod/status/1166423361372807168
https://twitter.com/VandaTheGod/status/1192851268924067840
In total, "VandaTheGod" managed to compromise about 4,820 websites, exploiting known vulnerabilities in obsolete tools. He wasn't limited only to "good cause" attacks, though, as he often engaged in cyber-criminal activities as well. The fact that the hacker liked to boast on Tweeter about both types of attacks, sharing Bitcoin wallet IDs, and offering card dumps for sale left crumbs of trace behind him. Check Point gathered things like email addresses that the actor used in various forums and websites, and then they tried to find overlaps with the WHOIS information that concerns the hacker's website, "vandathegod[.]com."
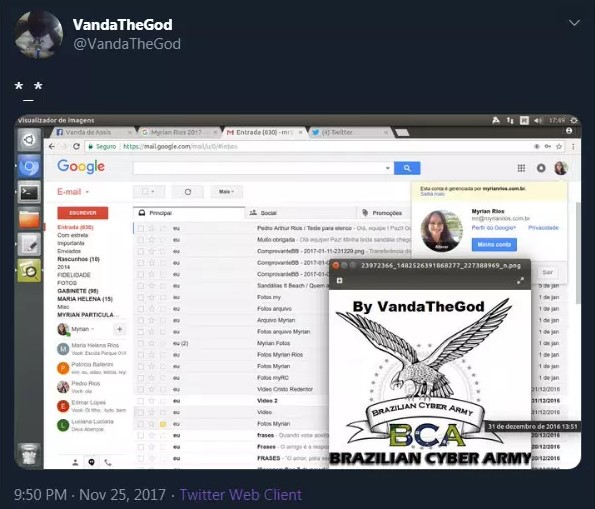
They've found that the domain registrant's email address was the same as the one that VandaTheGod used for his "UGNazi" portal and the braziliancyberarmy[.]com. Moreover, the registrant's location was declared to be "Uberlândia" - a municipality in the Brazilian state of Minas Gerais. The actor was generally quite careless in more than one instance. In the following screenshot, taken and published by himself, he is inadvertently revealing his Facebook username.
Source: Check Point Research
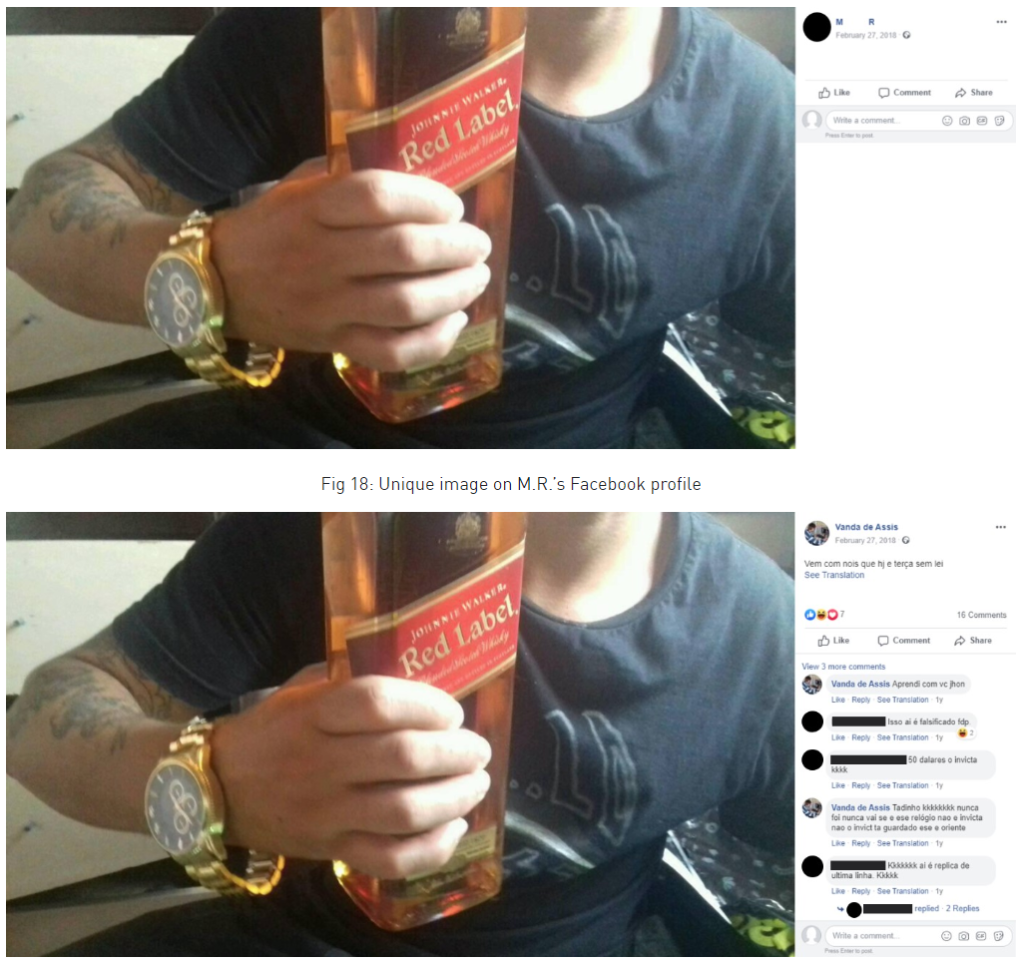
From there, the researchers found the initials "M. R.," so they narrowed down their investigation to Facebook users from Uberlandia having these initials. Although that was a long shot, they eventually located a single account that contained a post with the "Brazilian Cyber Army" crest. This account had more cross-posted images, so the match was definitely valid.
Source: Check Point Research
Check Point shared their findings with law enforcement in Brazil, and the hacker's activity on social media seems to have stalled since the end of 2019. This could be the time of his arrest, although no relevant reports have surfaced to confirm this yet.