Identity Attacks and USB Malware Are Rising in 2025, New Report Highlights
- Identity under siege: Attackers are increasingly targeting identity systems, with intrusions involving layered persistence methods.
- Phishing evolves: Over 70% of malicious attachments that bypassed secure email gateways used non-traditional file formats.
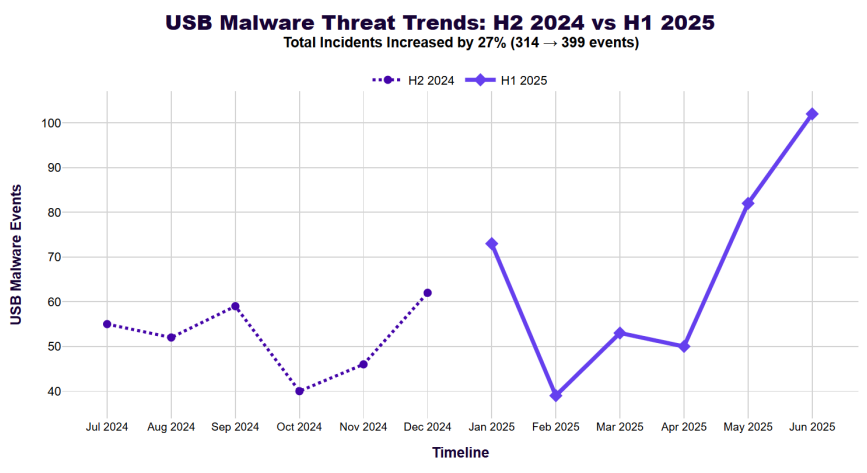
- USB malware returns: USB-delivered malware saw an increase compared to the second half of 2024, signaling a resurgence of old-school tactics.
Adversaries are blending sophisticated identity-based attacks with traditional malware delivery methods to compromise organizations, as identity attacks in 2025 have grown more complex, a new report from cybersecurity firm Ontinue reveals. Attackers combine token replay with cloud persistence, phishing with overlooked file types, and ransomware with weak vendor controls.
A Significant Shift in the Threat Landscape
The Ontinue 1H 2025 Threat Intelligence report indicates that nearly 40% of investigated Azure intrusions used layered persistence techniques, while approximately one in five incidents leveraged refresh token replay to bypass multi-factor authentication (MFA).
These tactics allow attackers to maintain access for extended periods, with average dwell times in cloud intrusions now exceeding three weeks.
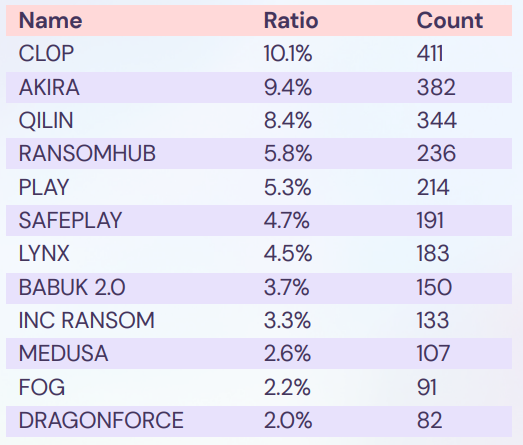
The report documents 4,071 claimed breaches across 109 countries, driven by 90 distinct ransomware groups, led by Akira, Qilin, and CL0P Ransomware, with the latter identified as a top threat in Kela’s 2025 Midyear Threat Report.
The services, manufacturing, and IT sectors were the most frequently targeted. This continued activity underscores that ransomware remains a primary threat, leveraging affiliate models to scale operations and impact organizations of all sizes.
Emerging Phishing Trends for 2025
The report also says attackers are moving away from traditional Office macros. Over 70% of malicious attachments that evaded secure email gateways were non-traditional file types, such as SVG and IMG files, used to embed scripts and redirect victims to credential-harvesting sites.
Phishing-as-a-Service (PhaaS) platforms like Tycoon 2FA have also matured, enabling adversaries to execute Adversary-in-the-Middle (AiTM) attacks that capture credentials and bypass MFA to compromise Microsoft 365 and Gmail accounts. This evolution requires a reassessment of email security protocols to detect and block these newer lure formats.
Perhaps the most surprising finding is the USB malware resurgence. Ontinue observed a 27% increase in malware delivered via USB drives compared to late 2024. This trend underscores how attackers exploit basic security gaps and human behavior to bypass network defenses entirely.
The findings emphasize the need for organizations to reinforce foundational security controls, such as restricting removable media and monitoring endpoints, alongside investing in advanced threat detection for cloud and identity systems.
Rhys Downing, Threat Researcher at Ontinue, notes that the primary gap is having advanced endpoint protection but permitting unrestricted use of removable media without proper device control policies in place.
“Insufficient user awareness training means employees don't recognize the risks of connecting unknown or personal devices, creating an easy entry point that bypasses perimeter defenses,” Downing told TechNadu. “These attacks succeed because they exploit predictable human behaviors and policy oversights rather than sophisticated technical vulnerabilities.”
Cybersecurity Experts Advise
“Introduce small steps to clean up a particular area, build the relationship with the business and with the buy-in, add the technical control ruthlessly”, said Balazs Greksza, Director, Threat Response at Ontinue for TechNadu. “Communicate your vision of having a growing part of your environment immaculate.”
James Maude, Field CTO at BeyondTrust, says that silos or gaps between teams or technologies mean a blind spot that attackers can exploit. “Security teams need to focus on closing the gap between security and Identity Access Management (IAM) tools as well as eliminating identity silos within their organizations,” he said. “A key part of this is having the right tools for visibility of the entire identity landscape rather than multiple siloed data points.”
“The complexity of modern application development, which involves entire supply chains, has expanded the attack surface,” added Nivedita Murthy, Senior Staff Consultant at Black Duck. “Consequently, threat modeling must now consider not only application design but also all associated touchpoints.”