“Icebucket” Is the Largest CTV Ad Fraud Operation Ever to Have Been Recorded
- Researchers discovered a massive CTV ad fraud operation and published the threat identifiers.
- At its peak, the operation impersonated over two million people by using bots and spoofed SSAIs.
- More than 300 advertisers were counterfeited, being requested up to 1.9 billion ads per day.
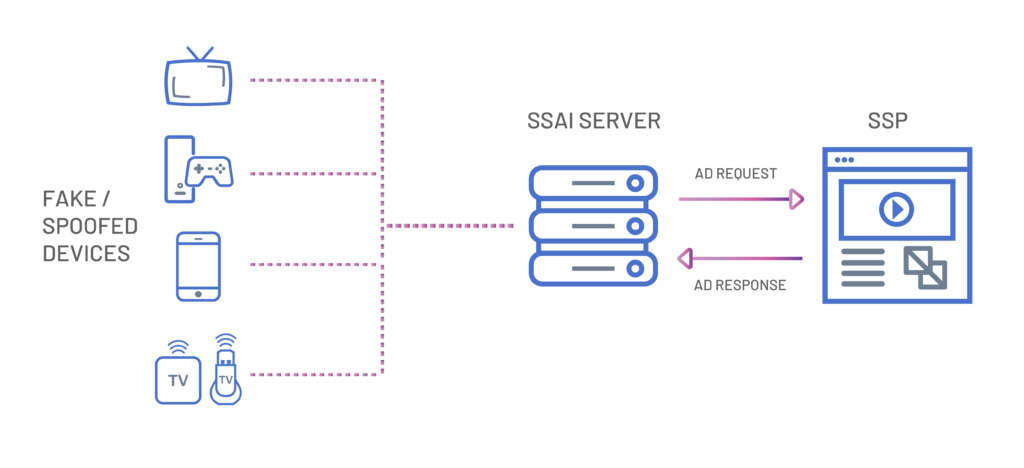
A team of threat researchers from White Ops has uncovered a CTV (connected television) ad fraud operation named “Icebucket,” which is the largest of this kind to this date. In numbers, Icebucket impersonated over two million people in thirty countries and counterfeited over three hundred publishers. As for the type of spoofed devices, 46% were various models/versions of Roku, 26.8% were Samsung smart TVs, 20.7 were Google TVs, and 6.1% were Android (mobile). All of these devices were fake, and the bots that pretended to be people watching the TV ads were hiding in the SSAI server.
Source: White Ops
Engaging in SSAI-level spoofing was key for the fraudulent operation, as advertisers are merely checking the device user agent and the IP address. It means that sending made-up data to the advertisers is fairly easy. However, doing it in the numbers that Icebucket did would involve some level of sophistication, without a doubt. The actors developed a custom SSAI spoofing code to assemble ad requests for virtual, non-existent devices, and they even bothered to generate a subset of fake network traffic that is irrelevant to the ad-serving but helps mask the real nature of the operation.
Source: White Ops
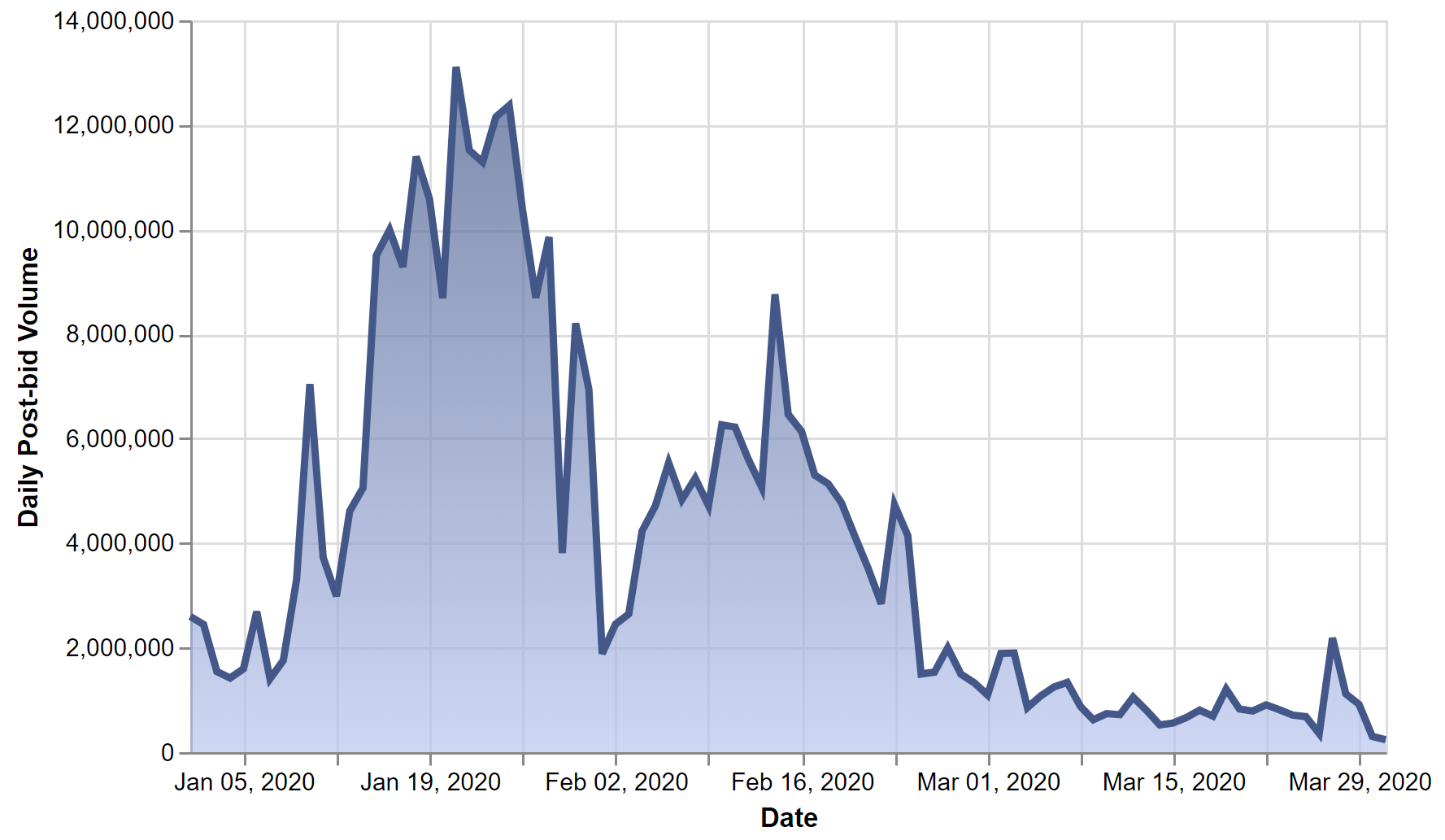
The peak of the fraudulent activity was in mid-January 2020, and although the botnet has somewhat subsided, it remains operational. White Ops have incorporated the threat signatures onto its mitigation platform, so its partners can now detect Icebucket traffic. The threat identification map includes 1,700 SSAI server IPs, 300 appIDs from various publishers, 1,000 user agents, and 2,000,000 IP addresses, mostly originating from the United States. It doesn’t mean that the actors are based in the US, though, as they are using VPN software for the spoofed IP addresses.
As long as the fundamental security problems of the SSAI remain, we are bound to see more operations like the Icebucket popping up. The ad-serving industry should ramp up their efforts in user and device ID verification, as well as develop standards that increase the transparency of the CTV inventory. White Ops gives the example of device authenticity verification based on cryptographic signatures, full supply chain visibility, and better training around SSAI spoofing. The more revenue is cut from the actors, the more significant the chances to see them turn elsewhere to make an easy profit.