IBM X-Force Warns of Privilege Escalation Risks in Microsoft Azure Arc Deployments
- IBM researchers have identified weaknesses in deployment scripts for Microsoft Azure Arc.
- Attackers could exploit misconfigured properties and hardcoded Service Principal secrets.
- They could gain unauthorized access and execute malicious code within highly privileged contexts.
Critical security risks associated with Microsoft Azure Arc were discovered, a service designed to unify management across hybrid environments, including on-premises systems and cloud platforms.
While Azure Arc facilitates seamless management and monitoring, its capabilities can also be exploited by attackers to elevate privileges and establish persistence across hybrid infrastructures.
Azure Arc enables administrators to manage systems as if they were native to Azure, employing features such as update management, policy enforcement, and remote command execution.
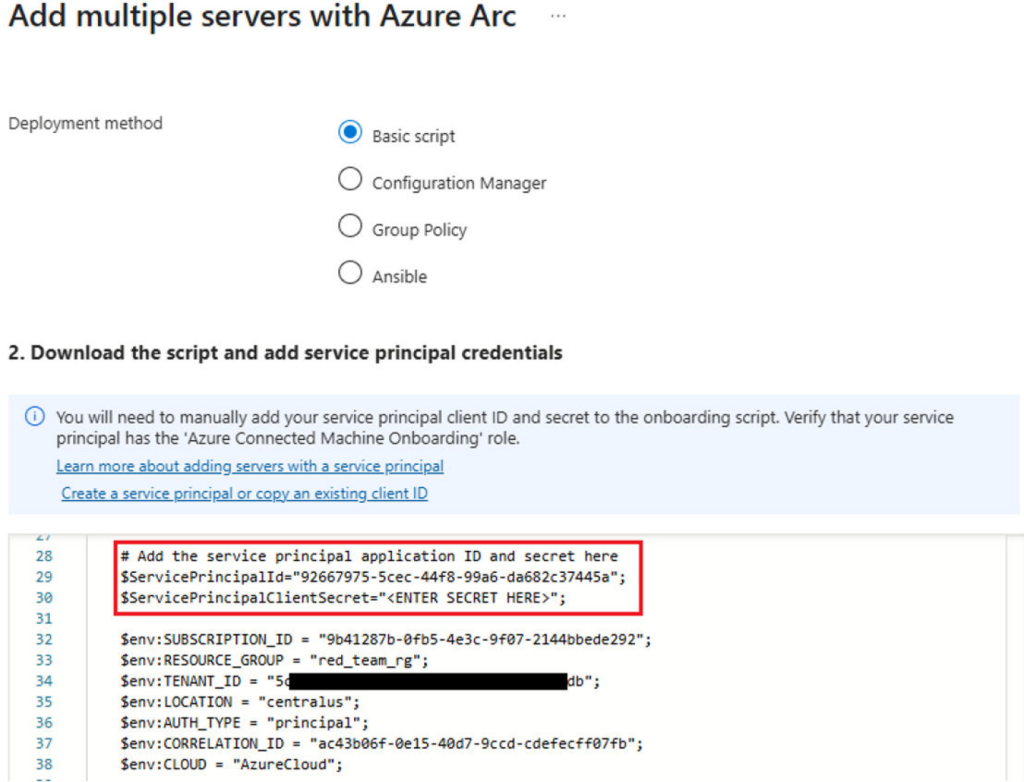
However, its powerful functionalities come with vulnerabilities that can be abused. IBM’s X-Force team has identified several attack vectors, including the exploitation of misconfigured properties and hardcoded Service Principal secrets, which are often found in deployment scripts.
These weaknesses could allow attackers to gain unauthorized access, execute malicious code within highly privileged contexts, and pivot between on-premises and cloud systems.
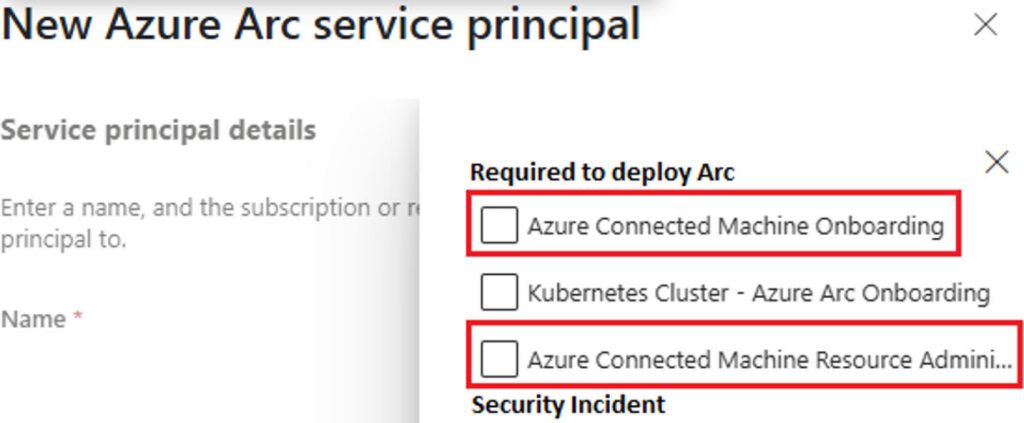
A key concern raised by IBM involves the inappropriate assignment of overprivileged roles, such as the Azure Connected Machine Resource Administrator, which grants attackers extensive control over Arc-managed resources.
Service Principal, which likely has its secret accessible on the on-premises network, could allow privilege escalation via Arc and on-premises environment takeover.
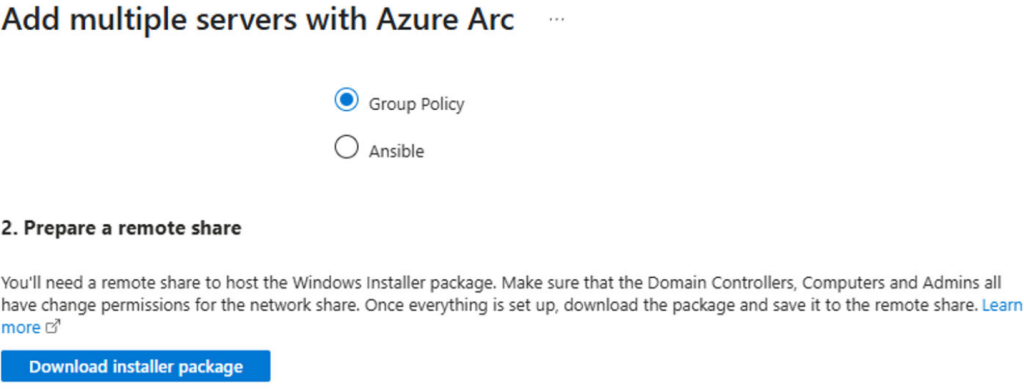
Combined with insufficient controls around deployment mechanisms, such as Group Policy or Configuration Manager, these weaknesses increase the risk of introducing malicious actors into enterprise systems.
Proactive countermeasures to secure Azure Arc deployments include restricting Service Principals to minimum-required roles, performing regular access reviews for sensitive permissions, and implementing allowlists or blocklists for extensions used with Arc-managed systems.
Monitoring for anomalies in deployment scripts and enforcing strong governance over access credentials are further essential steps.