Hy-Vee’s Atlassian Accounts Allegedly Compromised, Stormous Group Claims
- Stormous claims to have breached Hy-Vee's Atlassian accounts, including Confluence and Jira.
- This alleged infiltration exposed infrastructure diagrams and technical data related to operational systems
- The group alleges the exposure of 53GB of data; however, Hy-Vee has not commented on this specific breach.
Hy-Vee, the prominent grocery and retail chain, recently had its name mentioned on the dark web after the Stormous hacking group claimed to have stolen its data. The group, known for ransomware attacks, allegedly breached Hy-Vee’s Atlassian accounts, which reportedly allowed the exfiltration of internal data.
The information exposed over 50,000 individuals, according to the hacking group’s post on its data leak site. Compromising Atlassian tools like Confluence and Jira is significant as these are widely used for collaboration and project management.
Access to them can provide deep insights into a company's inner workings, intellectual property, and vulnerabilities. While some sources, like the ransomware monitoring site Ransomware.live, list Hy-Vee as a victim of Stormous, there is no official confirmation from the supermarket chain.
Thomas Richards, Infrastructure Security Practice Director at Black Duck, expressed concern over the nature of such compromises:
“Corporate team workspaces and tracking systems, such as Confluence and Jira, by nature, will store sensitive information. With very little details shared about the (alleged) compromise, it is concerning that the attackers were able to do so much. At this time, we don’t know if the accounts were compromised through phishing or credential stuffing attacks. If it is not enabled already, I highly recommend that Hy-Vee implement multi-factor authentication (MFA) on all publicly accessible systems to prevent a compromise from just a username and password.”
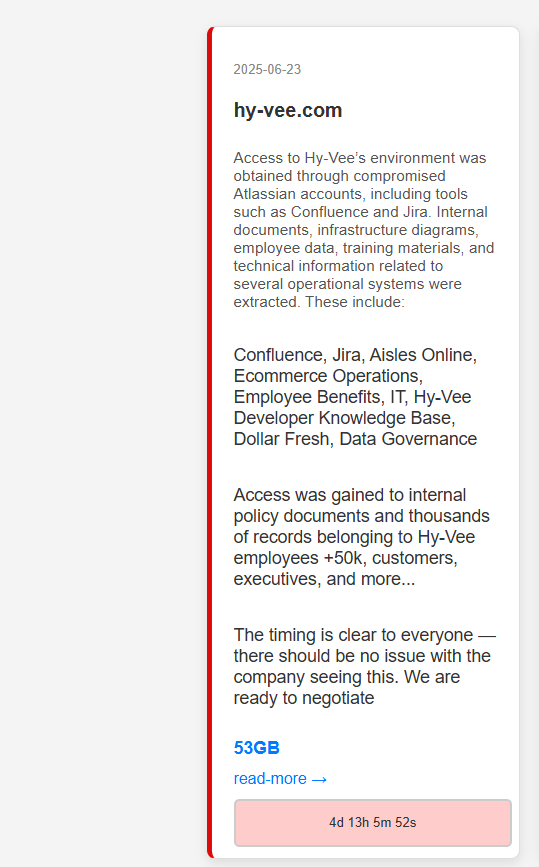
The screenshot shared by the cybersecurity intelligence account Hackmanac on X read that hackers stole 53GB of data. The estimated attack date was June 23, 2025, with a four-day ransom payment deadline.
The following details were noted on the ransomware.live tracking platform:
- The breach is speculated to have exposed 99 Hy-Vee employees
- It compromised a total of 3,297 individuals
- Four third-party employee credentials were detected by researchers
- The stolen information included internal documents, infrastructure diagrams, training materials, and technical information about operational systems
“Access was gained to internal policy documents and thousands of records belonging to Hy-Vee employees +50k, customers, executives, and more,” the screenshot text stated.
It further noted that data related to Aisles Online, ecommerce operations, employee benefits, IT, Hy-Vee developer knowledge base, Dollar Fresh, data governance, among others, were also exfiltrated by Stormous.
J Stephen Kowski, Field CTO at SlashNext Email Security+ emphasized the increasing targeting of collaboration platforms:
“(If proven) Atlassian breaches like this one show how attackers are increasingly targeting collaboration platforms because they contain a treasure trove of sensitive business data and often have deep integrations with other critical systems. The real problem isn’t just the initial account compromise - it’s that once attackers get into tools like Jira and Confluence, they can move laterally across the entire organization’s ecosystem, accessing everything from customer data to infrastructure diagrams.”
He also highlighted that stolen session cookies can maintain access for up to 30 days even after passwords are changed and two-factor authentication is enabled, and reiterated the need for organizations to implement real-time monitoring and threat detection to spot suspicious behavior.
A past Hy-Vee data breach from 2019 involved point-of-sale systems, which Hy-Vee confirmed at the time. A data breach report noted that Hy-Vee Inc. detected unauthorized activity on some of its payment processing systems on July 29, 2019.
The incident occurred on December 14, 2018, and lasted until July 29, 2019, when it was remediated. Payment card details, including expiration date and internal verification code, among other data, were accessed by cybercriminals.
We contacted Hy-Vee for a response on Stormous’ claims. We will update this report upon receiving a reply.