HP Bromium Says One Out of Three Threats Are Previously Unknown
- HP warns that 29% of all threats detected aren’t caught by most antivirus engines for nine days.
- Q4 2020 saw a steep rise in the deployment of banking trojans that stole millions of credentials.
- Adversaries are still relying mostly on abusing decades-old Excel macros via email attachments.
Researchers of the Bromium team at HP have shared its Q4 2020 threat insights report with TechNadu, and we’re seeing some interesting things that characterize the landscape and the direction things are taking. First, about 29% of all cyber threats captured by the HP researchers are previously unknown, indicating that the actors are constantly developing new malware strains, upping their packing obfuscation game, and finding ways to sign their software and evade AV detection.
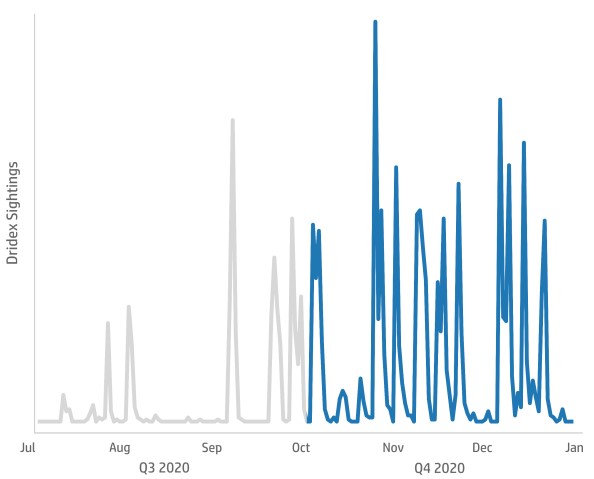
Due to the special “shopping spree” habits that underline every end of the year, Bromium also recorded a huge rise in Dridex malware deployment, a threat that specializes in the stealing of bank credentials, and which went up by 239% compared to Q3. Moreover, Trojan campaigns involving Dridex and Emotet accounted for 66% of all malware samples analyzed in Q4 2020, used in various voluminous spam campaigns.
Almost all malware (88%) was delivered to internet users via email, hiding inside fake invoice attachments that relied on technologies such as Excel 4.0 macros. This is a very old form of macros that is still used by several threat actors because it goes largely undetected. The remaining 12% of malware distribution happens via direct web downloads, and some of it is still triggered by URLs and buttons that are embedded on email bodies.
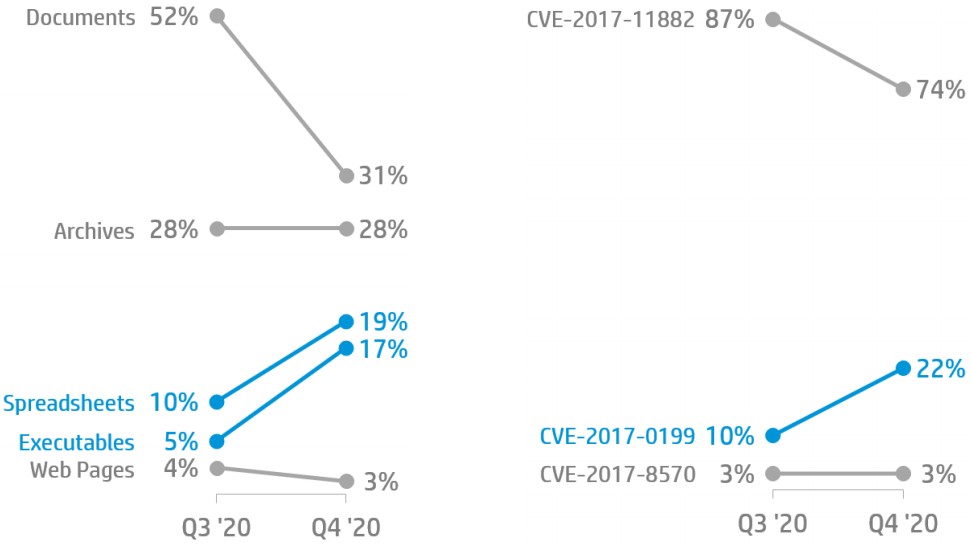
And as for the types of malicious files that arrive via email, most of them are Word documents (31%), then we have archives (28%), then spreadsheets (19%), and finally, executables (17%). The reason why executable files are the least used is that they are more likely to raise suspicion than the other forms. You shouldn’t rely on that, though, as any attachment that arrives via unsolicited communications should be treated with extreme caution.
HP warns that, on average, it took antivirus engines 8.8 days to identify the 29% of the previously unknown threats, so keep that in mind. One out of three times you scan an attachment before you download and execute it, you will get a false negative.
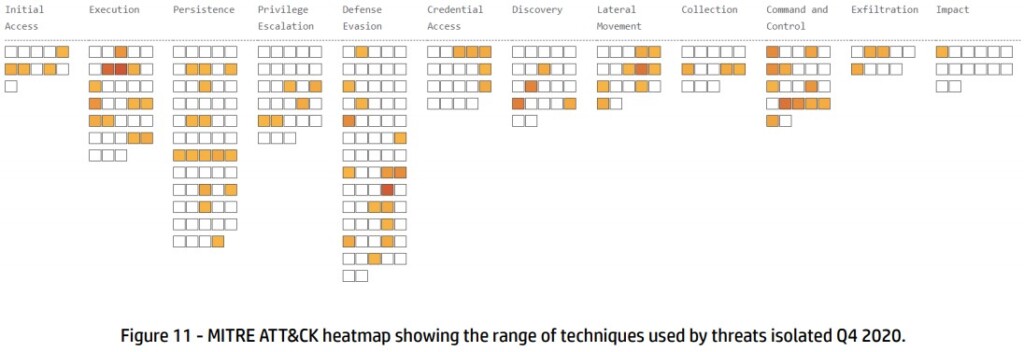
Finally, the most popular adversary techniques documented by the HP Bromium researchers were Execution through Module Load (T1129), Obfuscated Files or Information (T1027), and Execution through API (T1106).