How To Use a Live Boot Operating System for Internet Privacy
There are many components to privacy when it comes to using a computer. While using something like a VPN will provide you with one layer of protection from certain types of attacks or privacy leaks, it's just one part of a larger defense plan.
OS of Trust
One of the biggest tattle-tails when it comes to online privacy is your operating system. If you're running Windows or MacOS you have no idea what sort of information on your personal identity is being stored or transmitted back home. Apart from this cloak-and-dagger fingerprinting, there's a whole bunch of data on your computer that can be traced back to you. Browsers can ask the OS for information, malware can look at things like your user name, metadata appended to PDF and other documents can give you away too.
The bottom line is that using your daily operating system for tasks that require maximum privacy (such as whistle blowing) is a bad idea.
We've already described one strategy to help combat this issue. By combining virtual machine technology with Tor and VPNs you can prevent hardware fingerprinting and the OS giving away information about you, since it doesn't have any.
There is an alternative however and this has the added advantage of turning any computer into a secure point for you. Whether your own or someone else's. It's called a live boot operating system and it's a powerful internet privacy tool.
What's a Live OS?
When you boot up your computer the operating system loads from the main hard drive into memory and gets all the hardware up and working so that you can get on with browsing, gaming or whatever else people do on their PCs. It's a custom install tailored to your hardware, registered to your name and hosting all the software that you've bought.
A Live OS does the same thing as any other operating system, but it loads from a removable storage medium such as a DVD or thumb drive. Every time it loads, it's exactly the same as a clean install. It doesn't retain any information generated during previous sessions and it also leaves no trace on the computer it is used on. When you're done, you switch it off and walk away.
Going Deeper With Privacy Live OS Solutions
While using a live OS is a great start to hiding your identity, it's even better to use a live OS that has specifically been created to protect your privacy.
Here are some of the most popular choices:
There are also non-live privacy OS options such as Qubes, but in this article we're only going to focus on live OS options that don't get loaded to the hard drive. For this guide we'll be using Tails, since it's so popular.
What's Tails?
"Tails" is short for The Amnesiac Incognito Live System. The name pretty much tells you what you need to know about it. It was first released in 2009 and is currently sitting on version 3.5.
Tor partly sponsors Tails. The OS also natively routes network traffic through Tor for anonymity. They have pre-loaded Tails with a whole bunch of essential privacy tools. Such as OpenPGP, strong password generators and much more.
Getting Tails
The first thing you need to do is head over to the Tails home page and download a copy of the OS.
Just click the big "install Tails" button on the right hand side of the page and you'll get a online wizard to help you configure things correctly. Alternatively you can just click "download only" if you don't want your hand held.
Your Host OS Matters
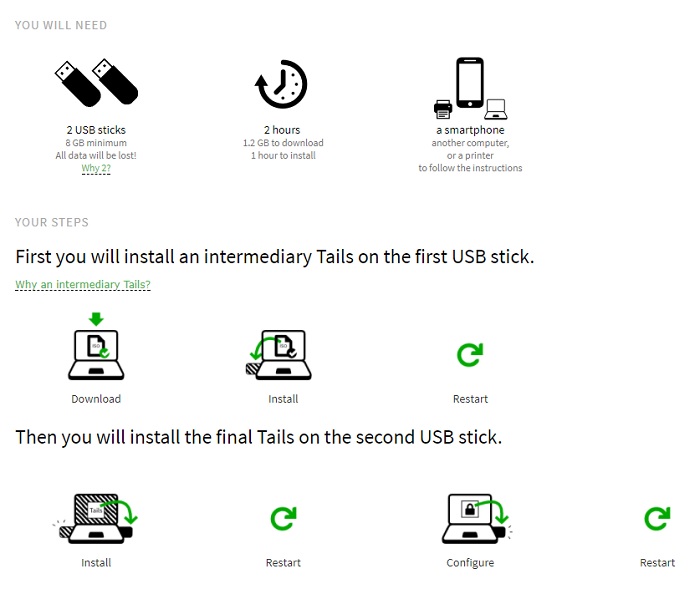
Most of you reading this are probably running a version of Windows. The bad news is that there is no way to securely install Tails directly from Windows at the moment.
The only method that works well involves two 8GB flash drives and an older obsolete version of Tails. Install the old version of Tails to the first flash drive. Then boot from that drive and use the older tails to create a flash drive with the newest Tails.
Tails themselves have diagrammed the process like this:
You'll find USB install instructions for just about every OS. Be aware that Macs seem to be hit and miss no matter what. If you don't want to go through the schlep of getting Tails working on a flash drive, you can simply burn it to a DVD or if you just want to try it out you can load it into a virtual machine by using the ISO file.
Booting Up with Tails
Regardless of whether you've put tails on a DVD or thumb drive, you'll have to tell the computer to boot from that media instead of the hard drive. Most modern computers will prompt you during bootup to press a key for the boot menu. Here you can choose which drive to boot from.
If not you need to head into the BIOS and change the boot order of drives to place your media of choice before the main boot drive.
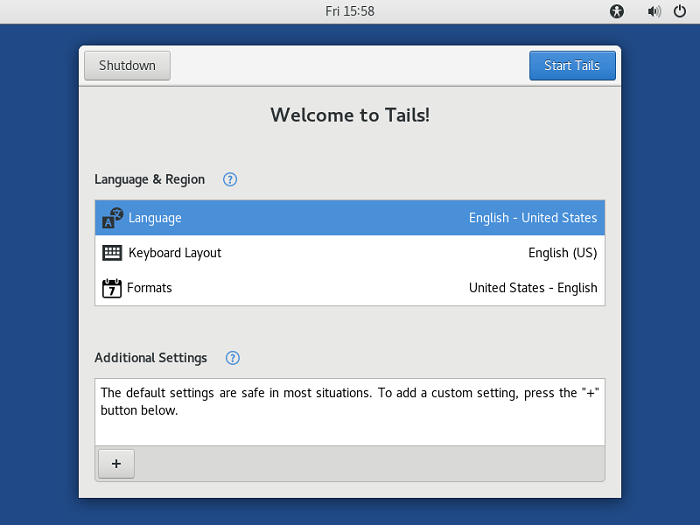
If you do it right, the computer will boot up with this start screen instead of the usual Windows, Mac or Linux OS.
Click "start tails" to get down to business and you're good to go.
From here you can start using the operating system for whatever you needed such high-level security and privacy. Once you've completed your business turn off the computer, remove the Tails media and restart it. It's like you were never there. Neither the computer nor the Tails media itself will have a record of what you did. As soon as the power to the RAM is cut off it all disappears.
Try Before You Buy
While I used Tails as an example here, you should really experiment with various privacy-focused Live OS options. That is, until you find one that you really like. Using a virtual machine package such as VirtualBox is an easy way to try many different systems. Without the tedium of creating flash drives all the time.
Even if you never need it, it's just good sense to have a live OS flash drive. Stored close by and ready to use.