Home Depot Halloween Phishing Scam Uses Fake Giveaway to Steal Personal and Financial Information
- Deceptive email: A new phishing campaign is impersonating Home Depot with a Halloween-themed giveaway.
- Advanced evasion tactics: The attack sends emails from a compromised high school domain, hidden Unicode characters, and reuses legitimate, historic email content.
- Multi-stage attack: The scam leads victims through a chain of redirects and, ultimately, payment details under the guise of a small "processing fee."
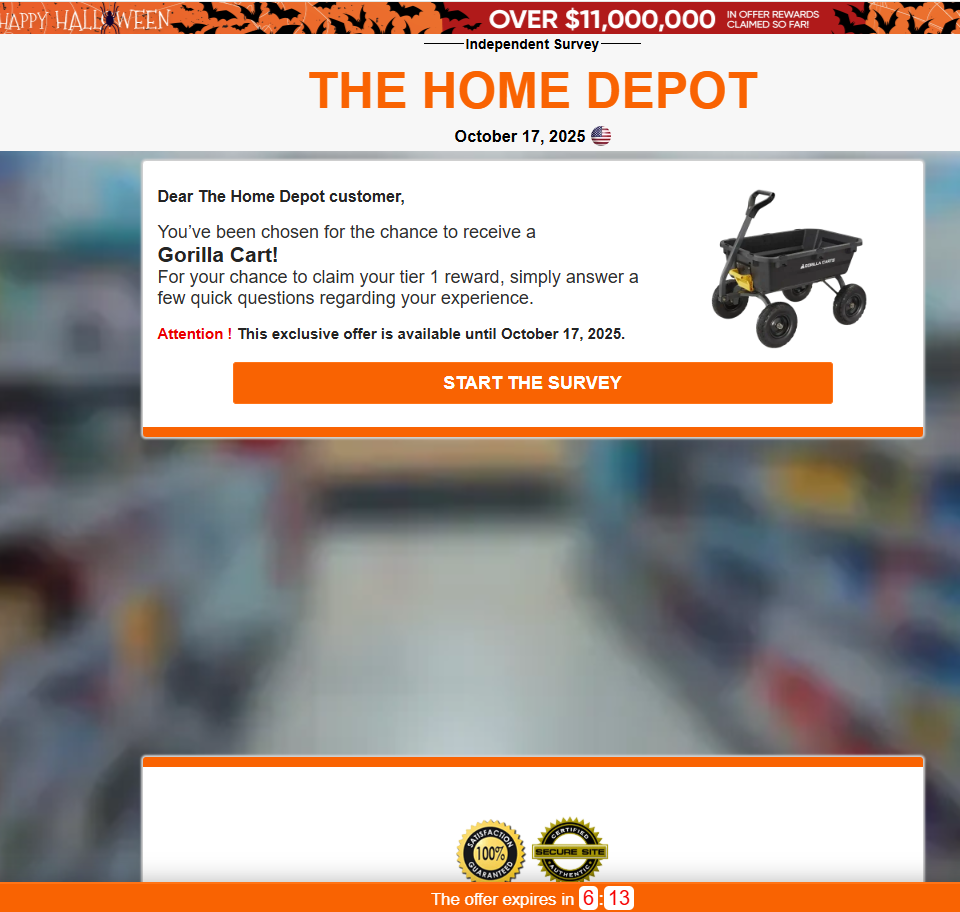
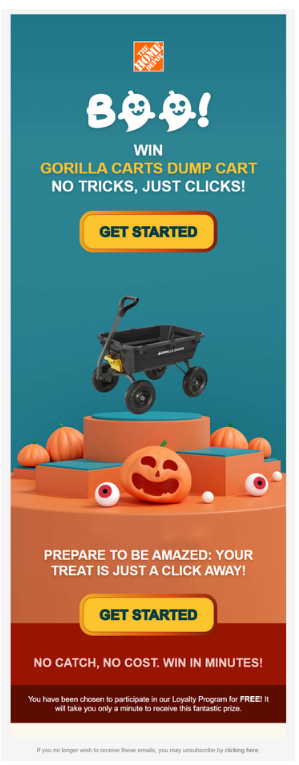
A timely and deceptive Home Depot phishing scam is making the rounds, attempting to trick users with a fake Halloween giveaway. The phishing emails, which claim the recipient has won a valuable "Gorilla Carts dump cart," are designed to appear legitimate but hide a multi-stage attack intended to steal personal and financial information.
The campaign demonstrates a notable level of sophistication, employing several tactics to evade detection and build a false sense of trust with the target.
Technical Breakdown of the Halloween Phishing Attack
Attackers are using several advanced techniques to bypass security filters. The phishing emails originate from a compromised, non-related domain belonging to a Los Angeles high school, a clear red flag, Malwarebytes warned in its latest report.
To evade automated spam detection, the email body contains hidden Unicode whitespace and control characters that break up text strings without being visible to the human eye.
Furthermore, the phishers have embedded a legitimate, but very old, order confirmation from a real vendor at the bottom of the email.
This tactic is designed to make the email appear as part of a valid, ongoing conversation, which can trick some filters into assigning it a higher trust score.
Clicking the link in the email initiates a complex chain of redirects, starting from a compromised WordPress site and passing through several domains to a final landing page. This landing page, designed to mimic Home Depot's branding, pressures the user with a sense of urgency before presenting a survey.
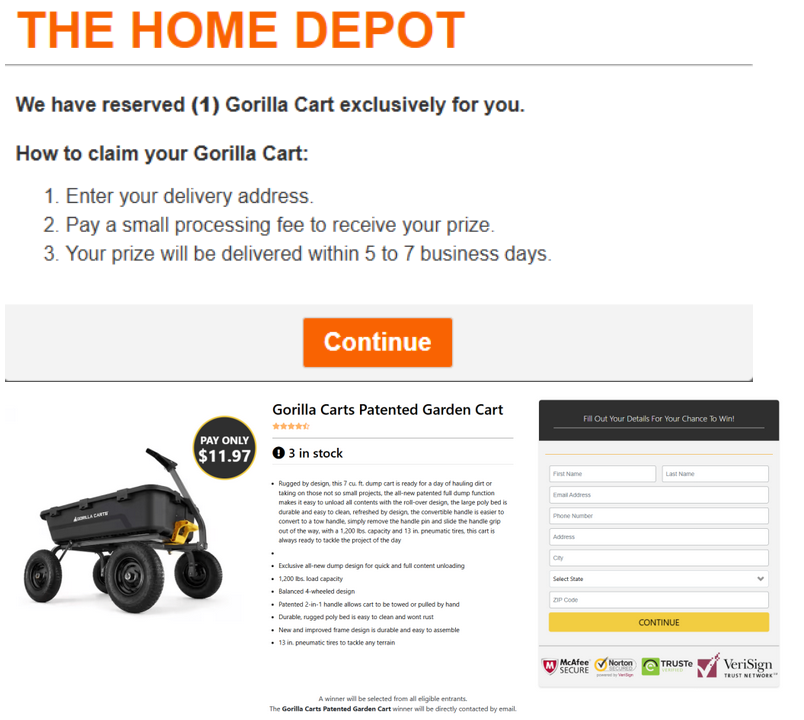
After completing the survey, the user is prompted to enter personal shipping details and then asked for an $11.97 "processing fee" to claim their non-existent prize.
The Path to Data Theft and Phishing Prevention Tips
For enhanced cybersecurity awareness, users should never click on links in unsolicited emails, always verify the sender's address, and avoid entering personal or payment information on unfamiliar sites. Using a real-time anti-malware solution with web protection is also a critical defense.
Last month, an SVG phishing campaign leveraging CountLoader to deliver Amatera Stealer and PureMiner targeted Ukraine.
Also, phishing emails with voicemail or purchase lures redirect to spoofed pages featuring the victim’s email and company logo in an August UpCrypter campaign that delivered DCRat, Babylon RAT, and PureHVNC.