Hijacked Discord Links Deliver Multi-Stage AsyncRAT and Skuld Stealer Campaign
- Attackers exploit a flaw in Discord’s invitation system to redirect users to phishing websites.
- They hijack inactive custom links for premium subscriptions to lead to fake “verification” processes.
- Legitimate services are leveraged in this campaign to deploy AsyncRAT and Skuld Stealer.
A significant vulnerability in Discord’s invitation system exposes users to sophisticated malware campaigns. Cybercriminals are exploiting expired and deleted Discord invite links, allowing attackers to redirect unsuspecting users to malicious servers.
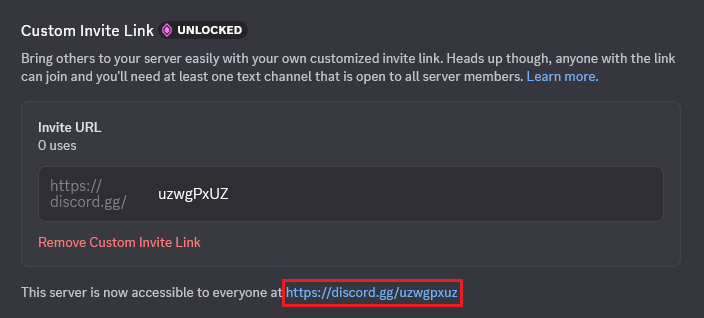
Attackers capitalize on Discord’s custom “vanity” links, a feature available for servers with premium subscriptions. Once these links expire or become inactive due to a server losing its premium status, attackers hijack the URLs and redirect users to fake servers.
Recent cybersecurity research by Check Point has uncovered that this campaign is characterized by its multi-stage infection chain, utilizing several evasion techniques to avoid detection by traditional antivirus software.
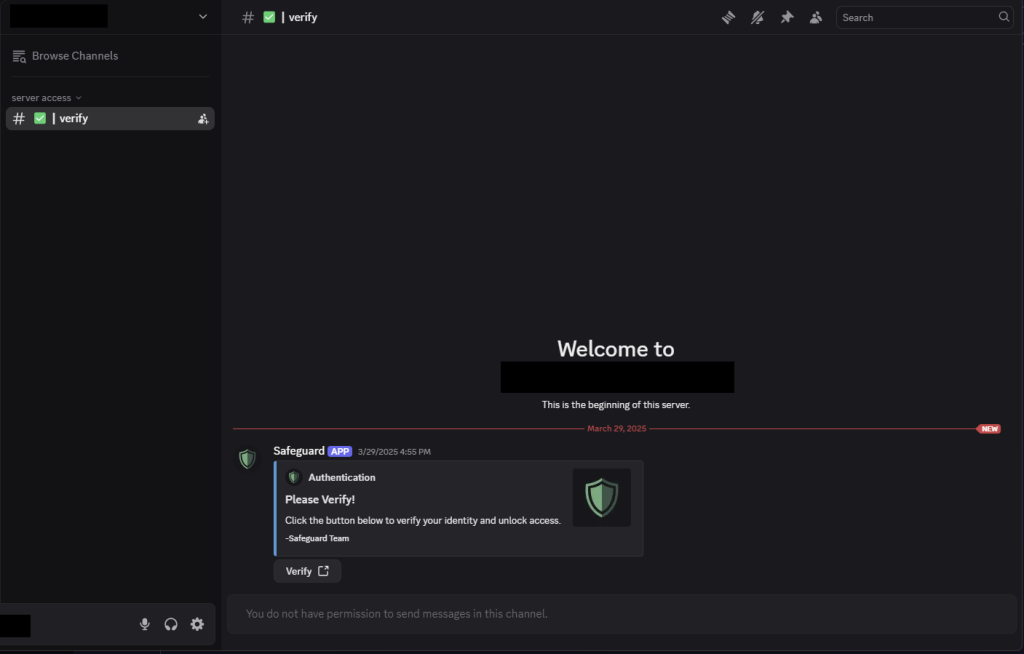
On these malicious servers, users often encounter seemingly legitimate channels with bots that prompt them to complete fake “verification” processes. These processes lead to phishing websites designed to trick users into executing malicious commands.
The campaign employs a blend of evasion tactics, including the ClickFix phishing technique, multi-stage loaders, and time-based mechanisms, to bypass security detection.
The primary payloads delivered are AsyncRAT, a remote access trojan (RAT), and a tailored version of the Skuld Stealer, which is specifically designed to exfiltrate sensitive data like cryptocurrency wallet credentials.
The malware achieves stealth by leveraging legitimate cloud services such as GitHub, Bitbucket, Pastebin, and Discord itself for payload delivery and data exfiltration, blending malicious activity into normal internet traffic.
Notably, the operation has evolved to bypass security features like Chrome’s App Bound Encryption (ABE). By adapting tools like ChromeKatz, attackers can steal browser cookies directly from updated Chromium-based browsers such as Chrome, Edge, and Brave.