“Hello” Ransomware Now Targets SharePoint Flaw for Entrance
- The “Hello” ransomware is exploiting a two-year-old vulnerability to find its way into unpatched systems.
- The malware uses strong encryption and performs several checks to ensure maximum damage on the first attempt.
- Patching remains the best proactive approach to deal with the particular threat.
Even though the “CVE-2019-0604” was listed in a "2020 most exploited vulnerabilities to patch" report compiled by CISA, and although Microsoft fixed this via a Tuesday Patch a long time ago, the authors of the “Hello” (WickrMe) ransomware have added it on their tool, and it is reportedly working well. As the Trend Micro threat analyst Janus Agcaoili reports, there are apparently enough unpatched SharePoint systems out there that make it worth using a modified version of the China Chopper web shell.
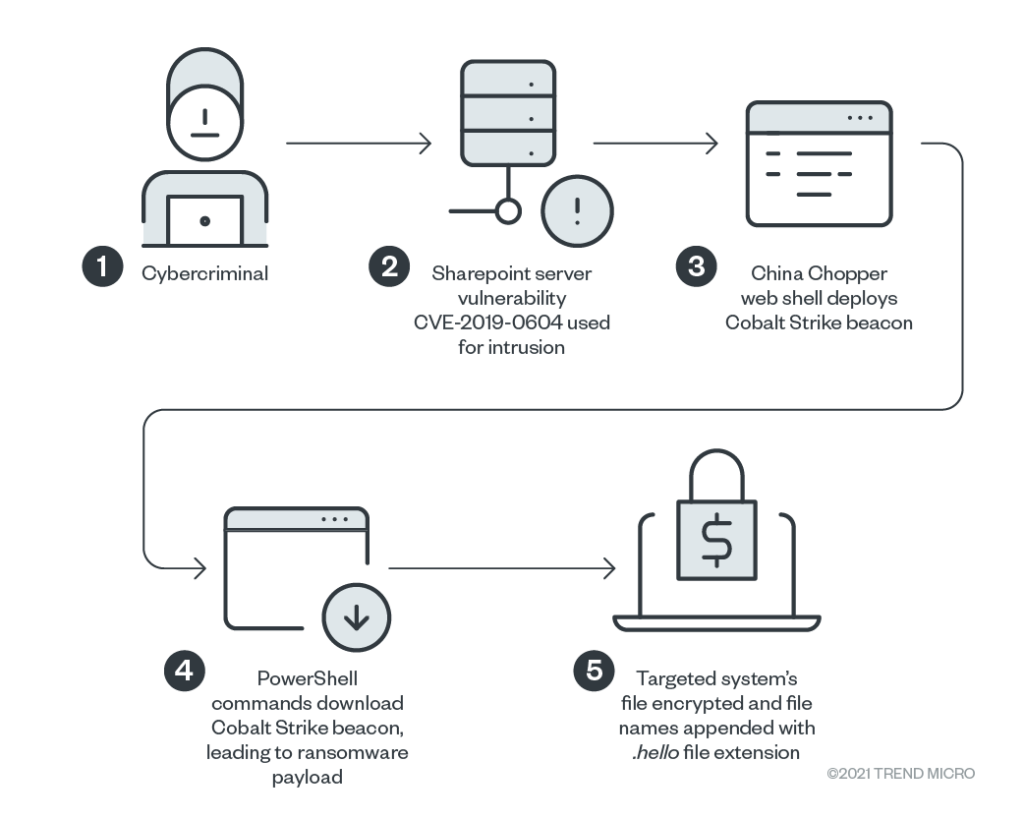
The exploitation of the aforementioned flaw opens the door for the actors, whose next step is to plant Cobalt Strike. Then, and after a short round of reconnaissance to ensure maximum effectiveness, the actual ransomware is launched, and the file encryption process begins. Thus, the particular flaw sets the stage for initial access, which is a very important part of a successful cyber-attack. The following diagram shows how the attack unfolds, step by step.
The malware performs some checks before the encryption routine is started to avoid a failure that would blow its cover for no good reason. The three conditions to be met with the argument “{Malware file path}\{Malware Name}.exe e {UUID} {BTC}” are the following:
- "E" is a hard-coded checking capability, which is needed as the first argument.
- UUID should be a file with an XML formatted RSA public key existing in the system. Otherwise, it will not proceed with its intended encryption routine.
- BTC is the amount to be paid, as displayed in the ransom note.
In addition to these checks, the ransomware searches for the allowlisted directories to avoid encrypting them. Also, some folders that affect the malware execution are excluded too. The encrypted file types include txt, doc, xls, zip, csv, pdf, ppt, rar, gz, 7zip, sql, so the damage will be significant.
If any database apps are found to be running, the associated services are terminated prior to the encryption. The encryption standard used is AES, while the key is encrypted with RSA. Eventually, all backup drives and shadow copies are wiped to hinder restoration without paying the ransom.
The best way to protect your systems against the dangers of “Hello” is to finally apply the patch that Microsoft released two years ago. Ideally, you should apply the latest patches or at least the available mitigations. If your systems are still offering CVE-2019-0604 on the plate, then this must be just one of the countless vulnerabilities you’ll have to deal with urgently.