‘Heaven’s Gate’ Loader Increasingly Deployed in Malware Campaigns
- Malicious actors are picking up the easily deployable and versatile “Heaven’s Gate” loader.
- The particular loader hides the malware inside it and runs it via low-level system calls.
- It also enables 32-bit code to run on 64-bit operating systems, tricking anti-virus solutions.
According to a detailed analysis report published by Cisco Talos, there’s a growing number of malware campaigns that use the “Heaven’s Gate” loader to run 32-bit malware on 64-bit operating systems while hiding the associated API calls. The researchers have taken note of campaigns that deliver HawkEye Reborn malware, various Remcos samples, and a collection of cryptocurrency mining trojans. That said, “Heaven’s Gate” is currently a key link of the chain, enabling malicious actors to load their nasty stuff on systems while minimizing the chances of getting detected or even analyzed.
The particular loader allows the malware to nest inside it, which is beneficial even if the malware features its own obfuscation. Without writing anything to the disk, AV tools fail to detect the presence of malicious tools. Moreover, the loader is obfuscating its API calls by using direct syscalls via the sysenter instruction on 32-bit systems. The loader also enables 32-bit malware to run on 64-bit systems, and do so without provoking the AV tools that are running on the system, as the latter usually ignore the associated calls and don’t expect malicious activity to stem from 32-bit apps.
image source: blog.talosintelligence.com
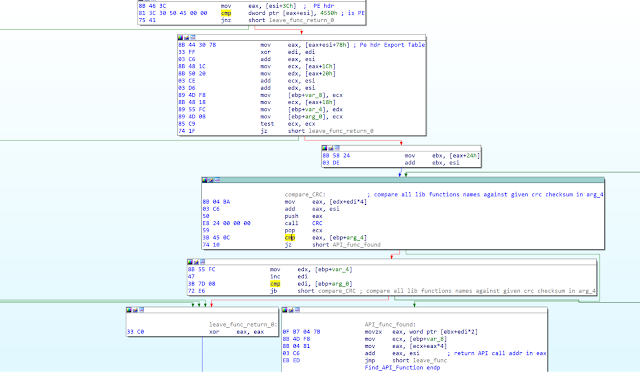
During their static analysis, the Talos researchers noticed multiple methods that Heaven’s Gate uses to make that process a lot harder. The malware is decrypted at runtime and is loaded onto the memory, so the hard drive is left out of the equation. The loader is decoding the malware code via low-level system calls, employs old shellcode tricks, and scrambles things around by storing the characters of its strings in local variables and keeping track of where is what through the generated checksums. Even the API functions that are called are hidden from the analysts, and the Talos researchers had to write a custom IDA Python script to keep track of what happens.
image source: blog.talosintelligence.com
The malware samples that are disseminated via Heaven’s Gate are mostly distributed via email, hitting targets with HawkEye Reborn, Remcos, Agent Tesla, and other types of malware. Usually, the topics of the emails are financially-themed, posing as invoices or banking statements. The documents that are attached to these emails are MS Word or Excel files, which leverage the CVE-2017-11882 vulnerability. Upon the opening of the malicious document, the malware is downloaded from the C2 server, and the infection chain begins. The Talos researchers warn that there are many campaigns of this kind that are currently underway, and the actors are renewing the binaries, emails, and documents on a regular basis.
Have you received a document that could be from one of these campaigns? Share the details with us in the comments down below, or help us spread the word of warning by sharing this post through our socials, on Facebook and Twitter.