Hackers Are Massively Hijacking SIP Servers for Profit
- A group of persistent hackers is targeting vulnerable SIP servers around the globe, looking resell IPRN services on social media.
- In many cases, the actors care to eavesdrop, move laterally, and even to plant crypto-miners.
- This has been going on since at least the beginning of 2020, targeting mostly large companies.
According to a report by CheckPoint researchers, there’s a massive wave of hacks against SIP (Session Initiation Protocol) servers affecting entities globally, and the whole thing is happening systematically and diligently. The researchers call the operation “INJ3CTOR3” and warn about the wide spectrum of abuse and the extensive coverage of the exploited vulnerability (CVE-2019-19006). In the most recent campaign attacks, the system that’s actively targeted is the ‘Sangoma FreePBX,’ a widely used web GUI for Asterisk VoIP management.
The targeting starts with scanning, which reveals any exploitable systems. The used vulnerability used is a critical authentication bypass flaw that has been around for almost a year now.
Still, a noteworthy number of Fortune 500 systems continue to use an old and unpatched Sangoma FreePBX version (115.0.16.26 and below, 14.0.13.11 and below, 13.0.197.13 and below). The hackers exploit this flaw remotely by sending specially crafted packets to the target server, gaining authorization, and accessing information.
Related: These Were the Most Imitated Brands in Phishing Campaigns During Q3 2020
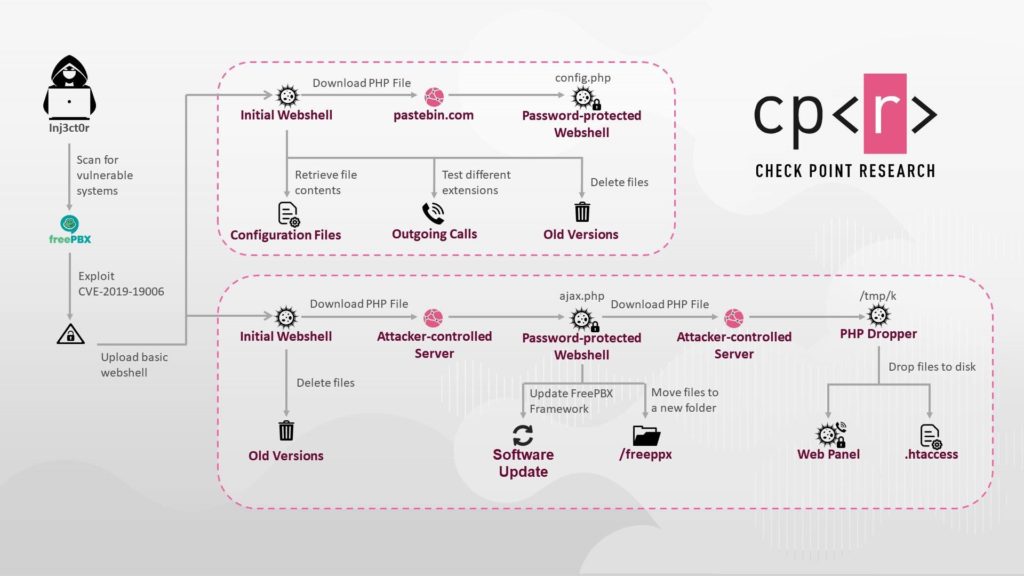
There are two possible ways the attack may unfold, as shown in the following diagram. The way the flow will unfold is up to the hackers, as the entrance method remains the same.
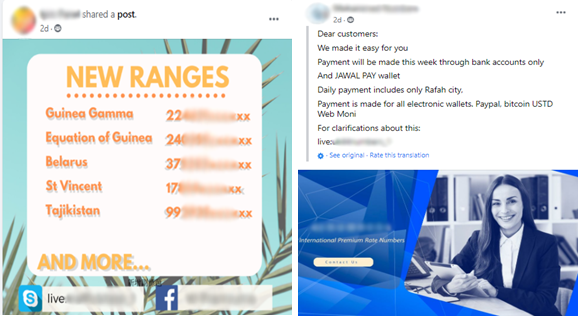
Once the attackers gain control of the server, they can make calls to International Premium Rate Numbers (IPRN) and have the victim pay the cost for it. So, what the hackers do is to resell these services to others and make profits.
CheckPoint has found this to be taking place even on Facebook, where call plans, phone numbers, and live access to VoIP services are offered for purchase.
In other cases, the attackers are interested in eavesdropping on the calls of the compromised company’s employees, attempt to plant cryptominers, move laterally, or use the systems as launching pads for new attacks.
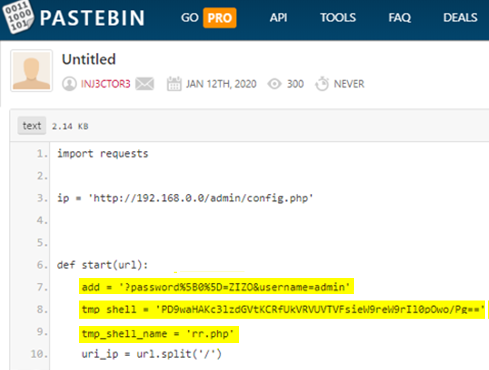
As for who hides behind this operation, there are no clear indications, but CheckPoint managed to find someone using the username “INJ3CTOR” who pasted a script that can exploit CVE-2019-19006 on Pastebin. The same username appears in the public sources of an old SIP Remote Code Execution vulnerability (CVE-2014-7235), so this could be a person or a group sincerely interested in exploiting SIP servers.