Hackers Group “Outlaw” Back to Business with Updated Kit
- Outlaw is back to targeting enterprises, and this time they’re using new and more powerful toolkits.
- The new strains are detecting, killing, and replacing older crypto miners with new ones.
- The target systems are IoTs and servers running Linux and Unix-based systems like BSD.
The “Outlaw” hacking group has emerged out of the shadows again, and according to the analysis of Trend Micro researchers, they are using updated exploitation kits. As it becomes evident now, the cybercriminals had paused their activity in order to work on their toolkits, which is crucially important when trying to launch successful attacks. The updates bring better target scanning capabilities, improved evasion techniques, looped file execution via error messages, and detection and removal of previous versions of miners used by the same actors. Right now, the group is tentatively testing their new tools in the wild by targeting new and old targets in the United States and Europe.
Source: Trend Micro blog
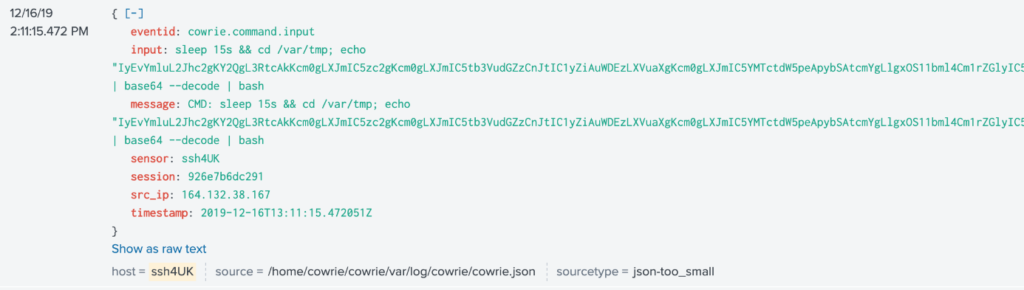
Trend Micro has collected various samples and up to 456 distinct IPs, noting that these new samples target Linux and Unix-based systems. This includes servers and IoT devices that are vulnerable to the CVE-2016-8655, CVE-2016-5195, and the Dirty COW exploit. There are even APKs targeting Android-based TVs that are infected by new crypto miners. “Outlaw” isn’t doing any social engineering or phishing, but instead rely on large-scale IP-range scanning methods. The attacks are launched from behind a VPN, and once the target is infected, the C2 sends over a whole kit of binary files to it in the form of a “.tgz” archive.
Source: Trend Micro blog
The researchers have noticed different variants being used right now, possibly in an effort of the hackers to figure out which ones work best in each case. Some wait for 20 minutes before they run the wrapper script on the compromised system, while others activate immediately and gather information about the host. Usually, whatever system information is collected by the group’s malware is stored locally on the device, and Outlaw only retrieves it to their C2 server after some time. In the case that files from a previous attack of the same group are found in the host, they are removed by the new scripts. For example, Outlaw has used crypto miners back in 2018, so they are killing them now if found to keep a low profile and evade detection.
In conclusion, we can say that enterprises that have patched their system have nothing to fear from these malicious toolkits, even these most updated versions. The Outlaw group is clearly going after “bigger fishes”, which brings them more money too. However, they are not doing it randomly. Instead, they target specific entities during very particular time periods, and which are based in certain geographical regions. This is due to law prosecution implications that underpin each action in specific areas, and also to maximize their gains by exerting the minimal possible effort.