Hackers Keep on Bashing West African Financial Institutions
- Hackers use off land remote admin tools and popular malware tools to carry out multiple attacks against West African banks.
- Symantec observes and monitors the activity closely, making correlations with the help of their AI tools.
- A new cybercrime trend emerges from the story, rendering hacking groups harder to identify and track on the expense of effectiveness.
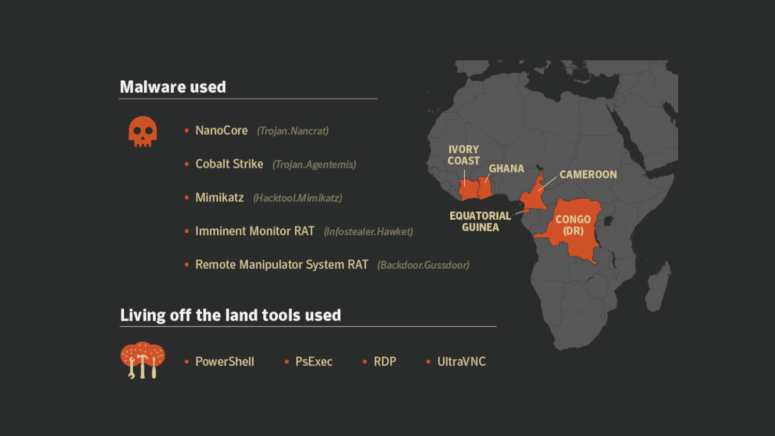
Symantec has issued a detailed report that analyzes how and why a series of attacks that targeted banks and financial institutions in Ivory Coast, Ghana, Equatorial Guinea, Cameroon, and Congo, all seem to derive from the same hackers. By utilizing their “Targeted Attack Analytics” tool, Symantec researchers have analyzed telemetry data and identified common patterns among the attacks that span from the summer of 2017 until today. The security firm cannot clarify whether the threat actors belong to a single or several groups, but it is apparent that they employ similar tactics.
Symantec has been observing the attacks ever since the first wave hit Ivory Coast and Equatorial Guinea in the summer of 2017, using the NanoCore malware and the Microsoft Sysinternals tool to run malicious code on systems of banks in the countries. The second wave hit various banks in Ivory Coast, Ghana, Congo, and Cameroon, with attackers employing PowerShell scripts and perform credential-stealing through the Mimikatz tool. The third attack focused on a financial institution in Ivory Coast again, by utilizing backdoor identifiers and RDP tools to steal credentials and establish remote connections to the infected systems. The fourth attack wave that was first observed in December 2018 focused on Ivory Coast organizations, with the attackers using the Imminent Monitor RAT information-stealing malware.
The fact that all of the above attacks use some kind of off-the-shelf malware indicates that the same people are possibly behind all data-stealing efforts. Moreover, making use of remote administration tools like PowerShell, UltraVNC, and PRP, suggests that the origin of the attacks is situated off the land, signifying the rise of a cybercrime globalization trend. While the hackers used readily available malware tools that are not as powerful or protected from backtracking as custom attack tools are, it still is effective when going against weakly defended or anemic security infrastructures like these employed in West Africa.
Symantec gives a full list of the indicators of compromise for all four attack waves in their report so that the concerned people can perform the relevant checks. The security research firm states that this type of remote attacks using off-shelve malware tools was rarely observed in the past, but is now becoming a common ground of action for hacking groups. One advantage that stems from using non-tailored attack tools is the fact that hackers are less identifiable, and attacking activities become less correlated.
Do you have an opinion on the above? Share it with us in the comments section or with our socials community on Facebook and Twitter.