A Hacker Has Published a List with 515k Passwords for IoT Devices
- A DDoS service provider has published a large list of Telnet credentials for anyone to use.
- The list is three months old, so some devices have been secured or have changed credentials already.
- IoT device owners need to take certain security precautions in order to stay safe from the possibility of falling victims.
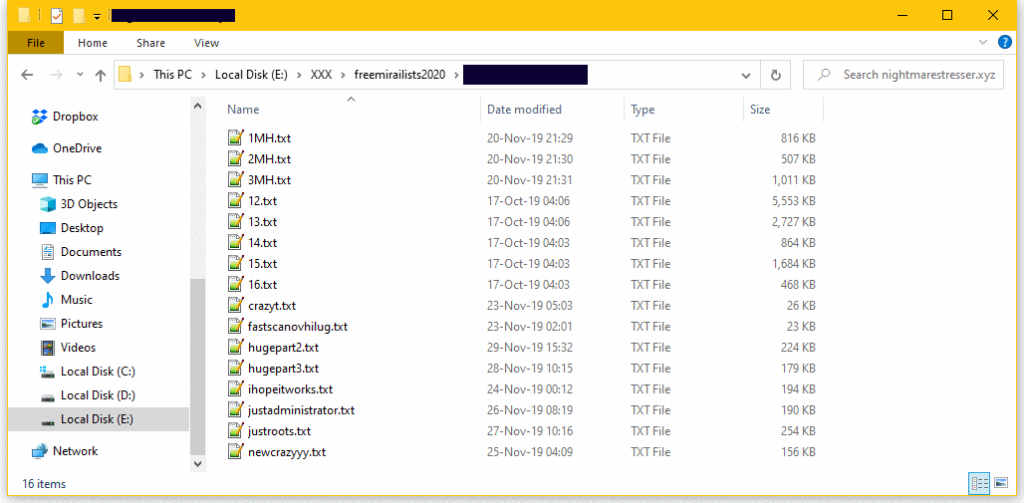
Someone has decided to publish a humongous list on a hacking forum, containing the Telnet credentials required to access 515000 IoT (Internet of Things) devices, routers, servers, and various smart dongles. This is probably the biggest leak of its kind ever, putting quite a lot of people and networks at risk right now. According to reports by ZDNet, the particular information was leaked by a DDoS (Distributed Denial of Service) operator who decided to upgrade his service from using IoT botnets to renting high-output servers from cloud service providers.
Source: ZDNet
This means that the actor had meticulously gathered these credentials previously in order to gain access and control the IoT devices through Telnet. The actor then used them to launch DDoS attacks against the entities that other people paid him/her to target. While the lists concern credentials that are about three months old, many devices are bound to still use the same IP address and/or login credentials. This means that part of this list is valuable in the hands of other hackers, although it would take a bit of effort to locate vulnerable targets.
This is a great reminder for owners of IoT devices that their tools need some basic security maintenance every now and then. First, don’t use the manufacturer’s “default credentials” if your device came with such. Secondly, don’t use them when you don’t need them, and try to set up a separate and isolated home network that will be solely used by these devices. Thirdly, turn off the UPnP (Universal Plug and Play) and use a different strong password for each device. Finally, apply any OTA firmware upgrades as soon as they are made available by the vendor of your device.
As for the signs of falling victim of a hijack attack, if your IoT is part of DDoS operations, it will overheat, get unresponsive, serve error messages, crash frequently, take longer to start-up or shut down, and generally act like “a zombie”. With the new list out there, the chances of falling victim to a device takeover attack have now multiplied, so you should take action against the possibility and follow all of the precautionary measures mentioned above. Of course, there is always a bot list circulating the net, and many actors are using these privately, but this particular list was a pretty big one.