Gustuff Banking Trojan Actively Used Against Financial Institutions in Australia
- An SMS campaign pushing the Gustuff banking trojan is now active in Australia.
- The malicious actors target large financial institutions and people who are working for them.
- The campaign uses versatile and resilient tools, able to fool anyone without leaving a trace.
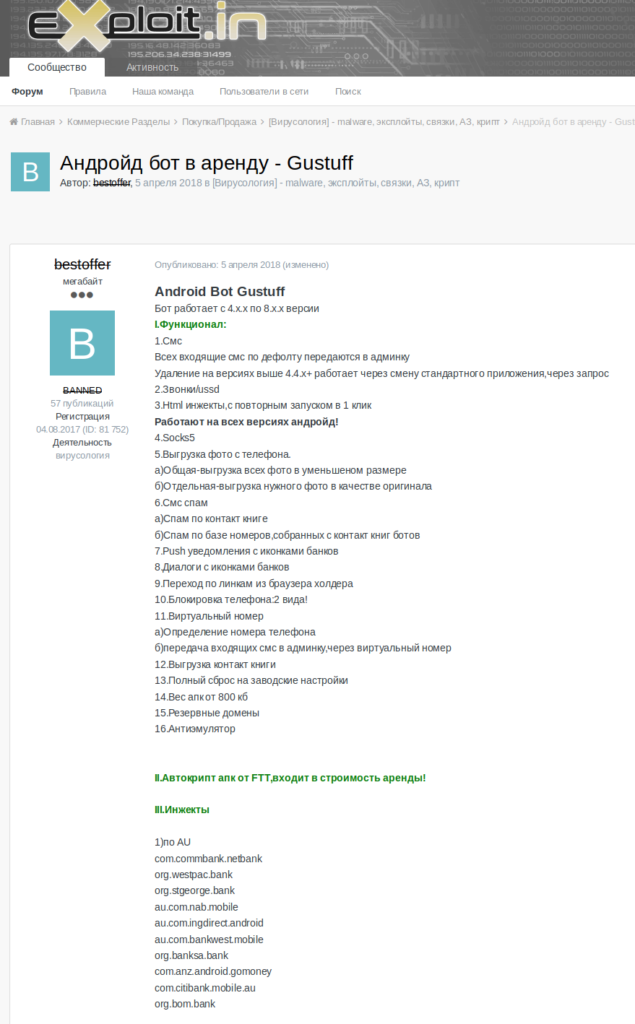
Financial institutions in the down under are in trouble, as a new “ChristinaMorrow” SMS campaign is active again in the country. According to an analytical report published by the Cisco Talos team, the campaign is highly targeted, looking to steal banking credentials, phone numbers of key people, and even files and photos found in their mobile devices. The trojan used in this campaign is Gustuff, a particularly nasty botnet that features high levels of automation, support for multiple banking apps, and powerful trace wiping capabilities. For more details on how Gustuff works, check out our previous post on the Android trojan.
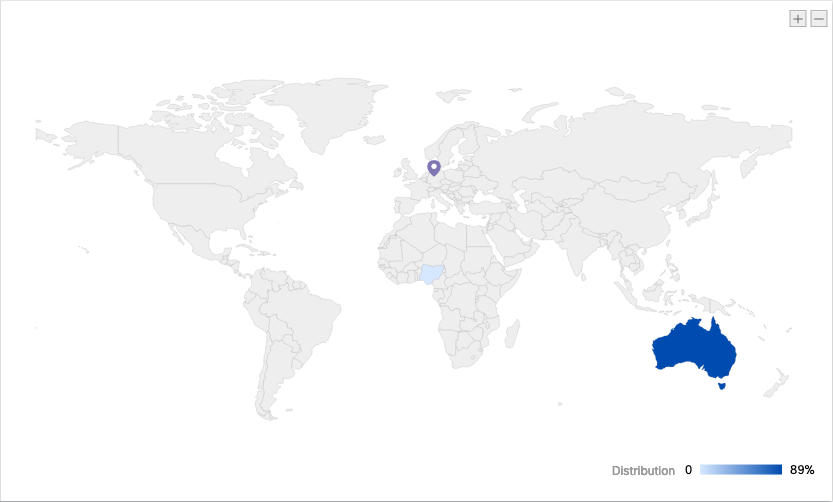
The actors exfiltrate the victim’s address book and then spread the malware by sending SMS messages to groups of 4-5 victims. These messages contain the payload-downloading URL, and since they come from one of their contacts, many people trust the link and click on it. Many of the targets work in prominent financial institutions in Australia, so the actors are directing their efforts towards the harvesting of crucial data, rather than immediate exploitation. By gathering data from the infected devices for some time, the malicious actors can pass through two-factor authentication layers, login in corporate networks, and propagate the infection further.
image source: blog.talosintelligence.com
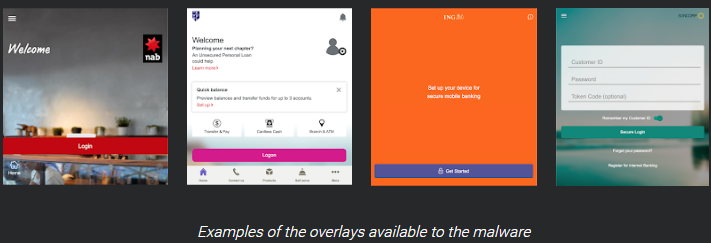
The command and control server that has been set up for this campaign checks the eligibility of the device and decides whether to proceed with the infection or not. One of the decisive factors is the geographic region, with Australia being accepted. Upon further investigation, the Cisco Talos team has located the seller of the particular Gustuff malware tool that is used in this campaign and figured that the tool was pre-set to target Australian organizations. Gustuff’s galore of functionality includes the familiar app-spoofing, banking credential stealing, and fake login overlays that the user is tricked into using.
image source: blog.talosintelligence.com
Besides the usual obfuscation and versatility that Gustuff is already known for, this version also comes with an additional resilience-boosting feature. More specifically, when the C2 is down, the actors may still control the malware and send commands to it via SMS, so the whole C2 infrastructure is optional really. This is possible thanks to the fact that the payload that is downloaded on the device contains all of the HTML, CSS, and even the PNG files that are required for the creation of the overlays.
image source: blog.talosintelligence.com
Have something to say on the above? Feel free to share your thoughts in the comments section below, and also on our socials, on Facebook and Twitter.