GrayAlpha Deploys NetSupport RAT to Organizations via Fake Browser Updates, 7-Zip Downloaders
- The FIN7-connected GrayAlpha showcases new malware tactics and evolving infection methods.
- Threat actors use fake browser update pages and 7-Zip download sites to distribute custom PowerShell loaders.
- NetSupport RAT infections are the final step, enabling remote control over compromised systems.
GrayAlpha, a cybercriminal cluster linked to the notorious FIN7 group known for its sophisticated, financially driven campaigns, showcases advanced technical capabilities and operational persistence.
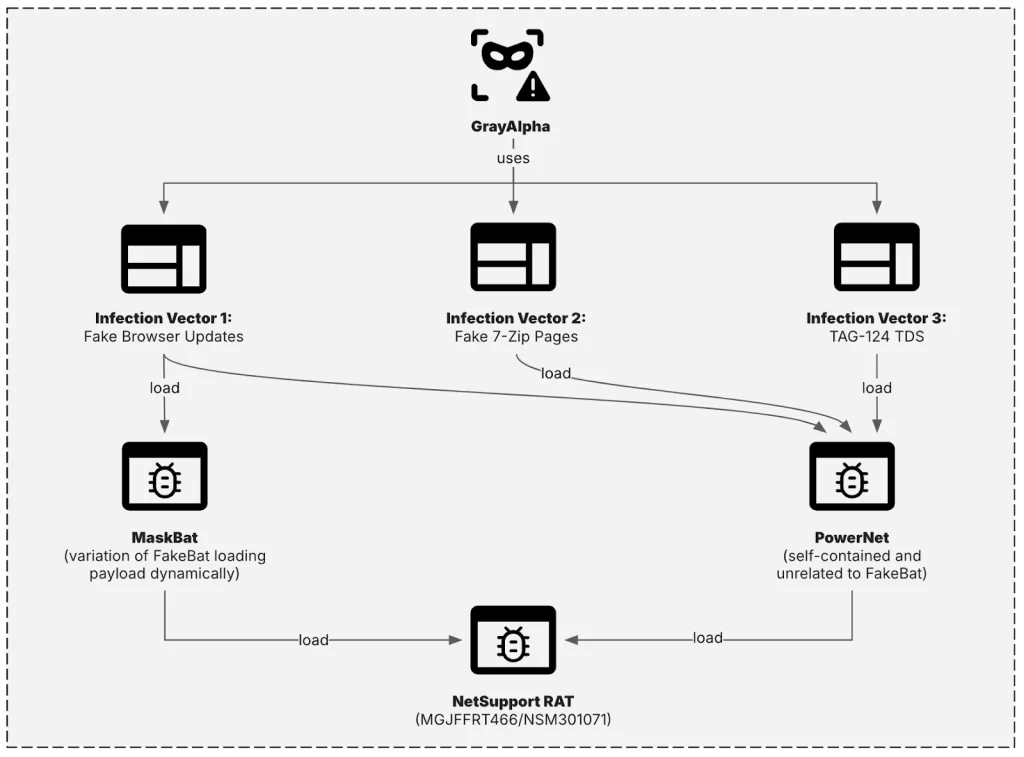
The group has established new infrastructure for distributing malware, including domains tied to payload delivery and custom PowerShell loaders such as PowerNet and MaskBat.
Leveraging diverse infection methods, GrayAlpha has employed fake browser update pages, fraudulent 7-Zip download sites, and its previously undocumented TAG-124 traffic distribution system (TDS).
Recent findings from Insikt Group say that currently, only the fake 7-Zip download sites remain active, with newly registered domains identified as recently as April 2025.
These deceptive vectors ultimately deploy the widely abused Remote Access Trojan (RAT) called NetSupport RAT, enabling remote control over infected systems.
GrayAlpha employs unique tools such as PowerNet and an obfuscated loader, MaskBat, exhibiting advanced sophistication.
Fake browser updates, TAG-124 TDS, and fraudulent software pages like Advanced IP Scanner–themed domains are used, illustrating innovation in attack strategies.
Domains tied to GrayAlpha’s activities remain active, signaling ongoing risks to organizations and individuals. Companies are urged to adopt proactive defense strategies to mitigate risks.
The most prominent RAT infection in recent days was a multi-stage AsyncRAT and Skuld Stealer campaign that leveraged hijacked Discord links.