“GootKit” Banking Trojan Turning Into a Scourge in Germany
- German internet users are getting tricked into downloading ZIP files on mimicked forum sites.
- The actors are pushing the GootKit banking trojan and the REvil ransomware strain right now.
- At least 600 people have been infected, while the laced sites that distribute the malicious ZIPs remain online.
The “GootKit” banking trojan, one of the less popular of its kind, is apparently returning to notoriety in Germany. Malwarebytes warns the public of the resurgence of the infections, which in several cases include the REvil ransomware too.
The signs of a German campaign for GootKit became evident at the start of November, but the situation hasn’t changed much to this day. Thus, internet users in Germany are advised to remain vigilant.
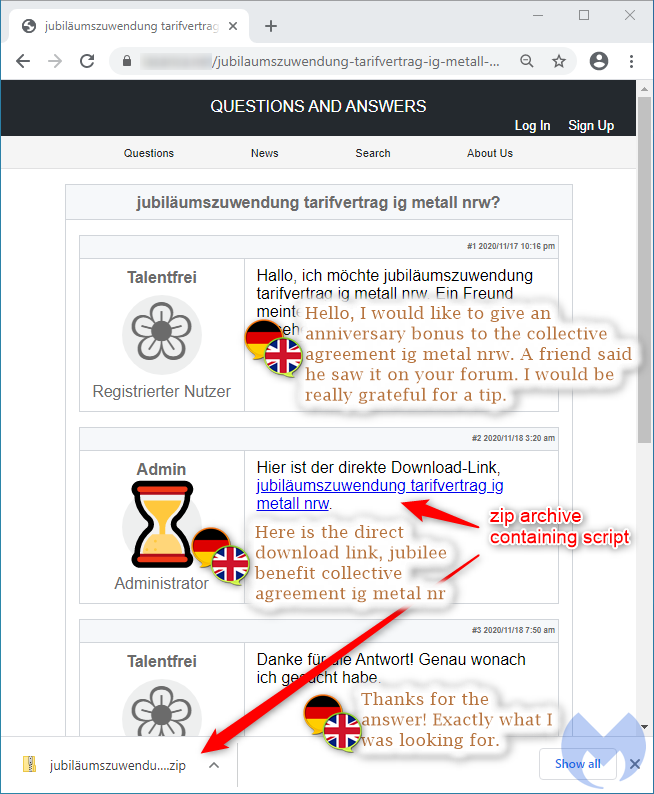
According to Malwarebytes, at least 600 unique machines have been compromised by GootKit, while the initial loader is being dissipated via hacked websites. The hackers are using a tricky technique that involves the customization of a fake template that ups its SEO rank.
The template resembles a forum page, and the trick is to provide the victims with the answer they are looking for. In all cases, the victims are urged to download a file that will solve their problem, and this is how GootKit is planted on their systems.
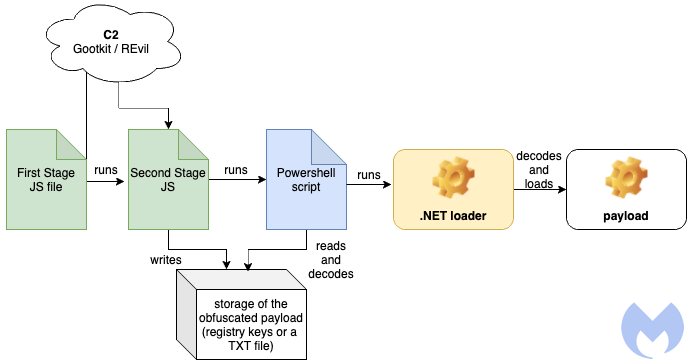
The ZIP archive contains an executable that the victim launches with hope, and it is initiating a five-stage procedure. It is important to clarify that the victim has to manually execute the malicious script, as there’s no automation to start the infection process.
Each script is obfuscated, and the one is decoding the next one until the final payload is reached. The first and second stages are fetched right from the C2, and so the actors may alter these payloads at any time. For now, they’re using GootKit and REvil.
Using this “matryoshka dolls” method with Base64 and hexadecimal strings is about rendering the security tools that could be running on the target machine worthless. Some may still catch the threat, but most will fail to do so.
The final payload is stored in the registry under a randomly-generated key name, so detecting and uprooting it is 100% heuristics. Of course, Malwarebytes - who reports on the campaign - will work as expected against the particular threat.
For now, these are the websites to avoid, and if you happen to land there, do not download or open anything that came from it.
- docs.anscommerce[.]com
- ellsweb[.]net
- entrepasteles[.]supercurro.net
- m-uhde[.]de
- games.usc[.]edu
- doedlinger-erdbau[.]at
- badminton-dillenburg[.]de
- alona[.]org[.]cy
- aperosaintmartin[.]com