Google Debunks Gmail Data Breach Reports That Said 183 Million User Account Credentials Leaked
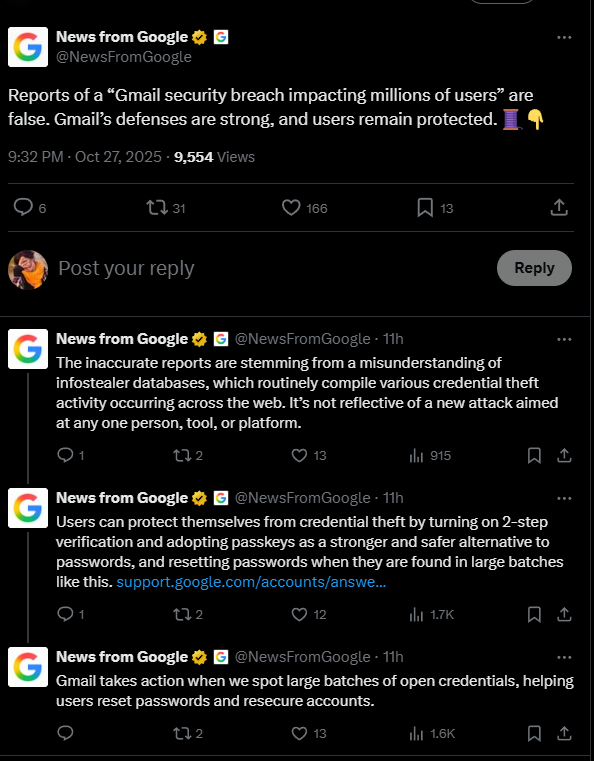
- No breach confirmed: Recent reports alleging a massive Gmail security breach have been officially declared false. Gmail's core systems were not compromised.
- Source of misunderstanding: The inaccurate reports originated from a misinterpretation of infostealer database compilations, not from a direct attack on Gmail.
- User action required: Gmail is actively working to re-secure accounts found in these credential dumps and advises all users to enable MFA.
Recent reports circulating online that claimed a widespread Gmail security breach affecting 183 million users have been formally refuted. The source of the alarmist reports appears to be a fundamental misunderstanding of how infostealer malware databases function.
Understanding Credential Theft and Protection
According to an official clarification, the platform's defenses remain robust and have not been compromised in a Gmail data breach, contrary to multiple reports linking it to the 183 million passwords recently added to Have I Been Pwned (HIBP).
However, cybersecurity analyst Troy Hunt says that 92% of the analyzed samples were not new, so “this steal leaves 8% that is new and fresh, or more than 14 million credentials if you extrapolate it,” cited by Forbes. “Actually, the final tally was 16.4 million previously unseen addresses in any data breach, not just stealer logs.”
Responding to the viral claims, Satnam Narang, Senior Staff Research Engineer at Tenable, explained, "Google itself has not been impacted by a breach. Instead, researchers aggregated threat data from a variety of sources, which included 183 million unique credentials tied to various websites, including Gmail."
Warning about the risks tied to stolen account credentials and origin, Narang said, "The source of this data is a combination of data leaked in other breaches, as well as data obtained from information stealers (infostealers). If a user logs into their Gmail account, financial institution, social media, and other accounts, this information will be captured in these stealer logs."
Infostealer databases are not the result of a singular, recent attack on a specific platform like Gmail. Instead, they are aggregated lists of credentials harvested over time from various unrelated compromises across the internet, such as phishing attacks or malware on user devices.
The compilation of stolen credentials into large databases is a routine activity for cybercriminals. When these large batches of exposed credentials are identified, Gmail initiates proactive measures to help users reset their passwords and re-secure their accounts.
This process is standard operational procedure and does not indicate a new, direct attack on Google's infrastructure. Effective credential theft protection remains a shared responsibility between the service provider and the end-user.
The most effective defense against the misuse of stolen credentials is to ensure they cannot be used by an unauthorized party, even if they are exposed.
Recommended Security Measures for Users
To mitigate risks associated with credential theft, users are strongly advised to enhance their account security. The single most impactful step is enabling 2-step verification (2SV), also known as multi-factor authentication (MFA).
This security layer requires a second form of verification in addition to a password, preventing unauthorized access. Furthermore, users should adopt passkeys for Gmail. Passkeys are a more secure and convenient alternative to traditional passwords, using cryptographic principles that are resistant to phishing attacks.
Regularly reviewing account activity and resetting passwords, especially when notified of potential exposure, are also critical security practices.
Narang highlighted the challenges posed by such incidents and urged users to secure their data, saying, "....if users have re-used those passwords on other websites, an attacker could try to conduct ‘credential-stuffing’ attacks, where they attempt to stuff a bunch of email address/password pairs onto websites to see which ones return a successful login. The safety measures that users can utilise are to start by not re-using passwords."
In June, cybersecurity researcher Jeremiah Fowler discovered an unprotected database containing more than 184 million plaintext passwords, reportedly from major platforms such as Google, Facebook, Apple, Microsoft, Instagram, and Snapchat.
TechNadu also reported on what may have been the largest password breach compilation to surface that month, combining 16 billion credentials from various companies, including Facebook, Google, and Apple.
One month earlier, law enforcement provided Have I Been Pwned (HIBP) with 15.4 million victim email addresses and 43.8 million passwords.