GoBruteforcer Botnet Evolves with AI-Driven Tactics, Targets Linux Servers
Key Takeaways
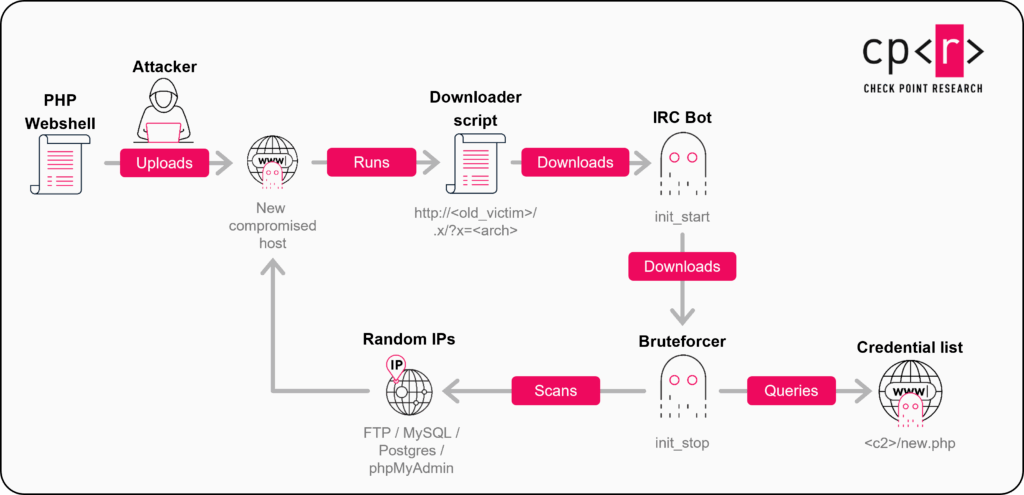
- Modular Architecture: GoBruteforcer botnet targets Linux servers via FTP, MySQL, PostgreSQL, and phpMyAdmin services using IRC bots and bruteforcers.
- AI-Driven Expansion: The latest campaigns exploit the widespread use of AI-generated deployment scripts that propagate common default usernames.
- Financial Motivation: Attacks target blockchain projects, utilizing specialized scanners to identify and drain cryptocurrency wallets on the TRON and BSC networks.
A highly evolved variant of the GoBruteforcer botnet has been identified. It features a completely rewritten IRC bot developed in Go that employs heavy obfuscation and advanced persistence mechanisms. The malware targets internet-exposed Linux servers, systematically compromising services such as FTP, MySQL, PostgreSQL, and phpMyAdmin.
Once infected, these servers are conscripted into the botnet to conduct further scanning operations, creating a self-propagating cycle of compromise.
Exploiting AI-Generated Server Defaults
A critical driver behind the current wave of infections is the increasing reliance on AI-generated server defaults. CheckPoint Research analysis indicates that administrators frequently utilize Large Language Models (LLMs) to generate deployment configurations.
These AI models often output scripts containing standard, predictable usernames like appuser, myuser, or operator. GoBruteforcer (also called GoBrut) actively leverages weak password exploitation against these specific identifiers.
Additionally, the botnet targets legacy web stacks, such as XAMPP, which often deploy with exposed FTP interfaces and default credentials. Current estimates suggest that over 50,000 internet-facing servers may be vulnerable to these specific intrusion vectors.
Crypto-Focused Cyberattacks and Mitigation
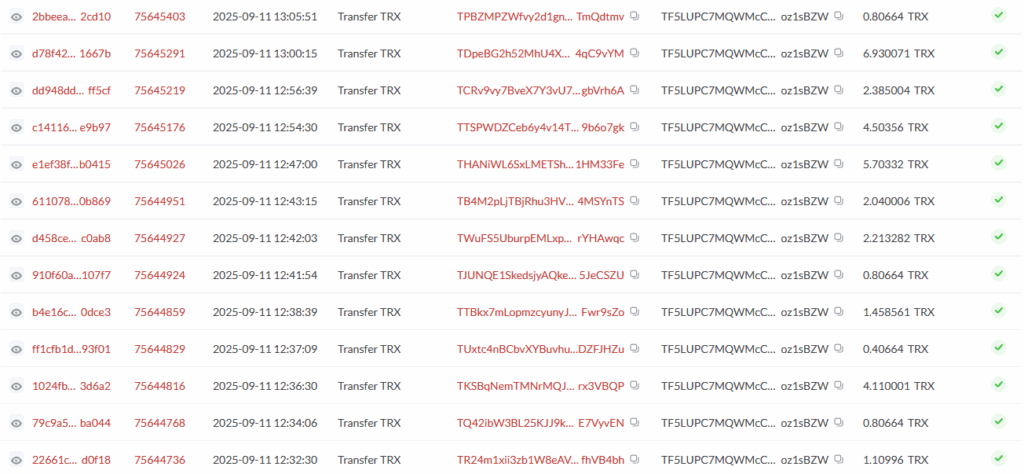
Beyond resource hijacking, the botnet, first documented in 2023, is executing cyberattacks focused on cryptocurrency wallets. Analysis of compromised hosts revealed specialized utilities designed to scan and sweep tokens from the TRON and Binance Smart Chain (BSC) networks.
The attackers used credential lists tailored to blockchain-specific terminology to breach databases containing digital assets, placing additional modules that matched the group’s tooling profile.
To defend against these threats, organizations must audit their internet-facing services and implement robust authentication protocols that go beyond standard username-password combinations.
In November, the DanaBot banking trojan resurfaced, focusing on cryptocurrency theft following its Operation Endgame takedown, and a new Mirai variant, ShadowV2, targeted vulnerable IoT devices to create a botnet for DDoS attacks.