Decryptor for GetCrypt Ransomware is now Available
- Emsisoft has released a decryptor for GetCrypt, which works even without the decryption key.
- GetCrypt is differentiated from other ransomware samples by trying to brute force user network credentials.
- The ransomware decrypts the files with the Salsa20 and RSA-4096 algorithms, while the prefix is random.
The GetCrypt ransomware that was circulated recently through various malvertising campaigns has finally met its match in the form of a decryptor that was made available on the website of Emsisoft, free of charge as always. The only thing required for the utility to work is to provide it with two samples of the same file, one encrypted and one not. There’s no need for a decryption key, as the decrypter can brute force it on its own. If you can’t imagine where that “unencrypted” file could be, check your offline backup. If you don’t have one, you are busted, but at least it’ll be a good lesson for the future.
The malicious actors are deploying the RIG exploit kit in their malvertising campaigns, directing victims to websites that execute scripts that eventually lead to the downloading and installation of the GetCrypt encryptor. Excluding Ukrainians, Russians, Belarusians, and Kazakhs, GetCrypt is scanning the infected PC and gets a list of the files that are available for encryption. The algorithms used for this job are Salsa20 and RSA-4096, while the extension of the resulting files is not characteristic but instead based on the CPUID of the infected system.
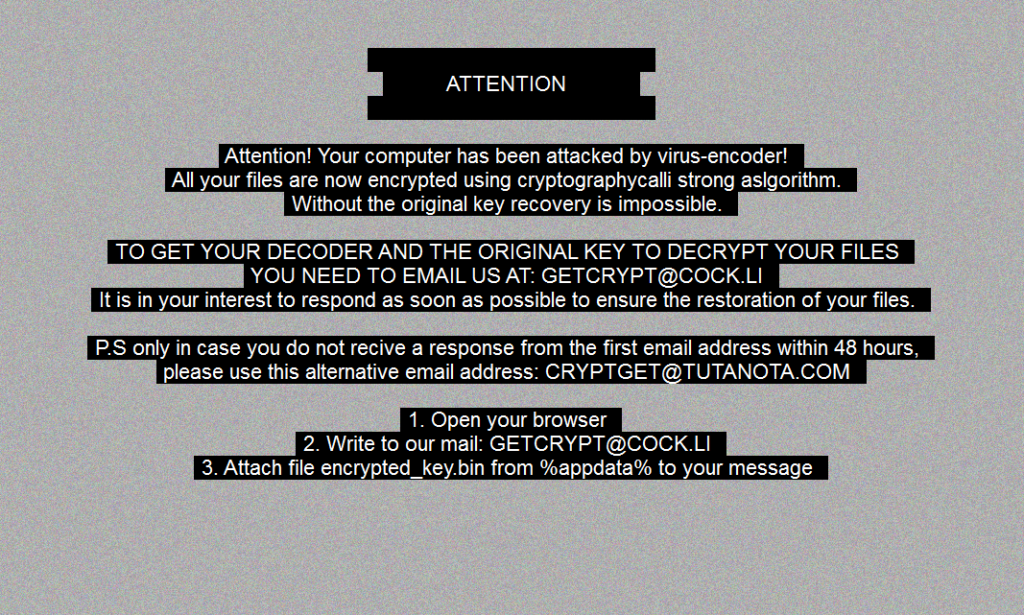
The ransom note that is created by GetCrypt is to be found in each folder, and also on the desktop, urging the victim to email to “[email protected]” to get the payment instructions. The victims are forced to send the first message to the malicious actors within 48 hours, while an alternative email address is provided in the case that the recipient of the first address is too busy drinking cocktails in the Caribbean with the victims’ money to respond. To make sure that even the completely incompetent won’t miss the text file, the GetCrypt is changing the wallpaper of the infected system to the following:
image source: bleepingcomputer.com
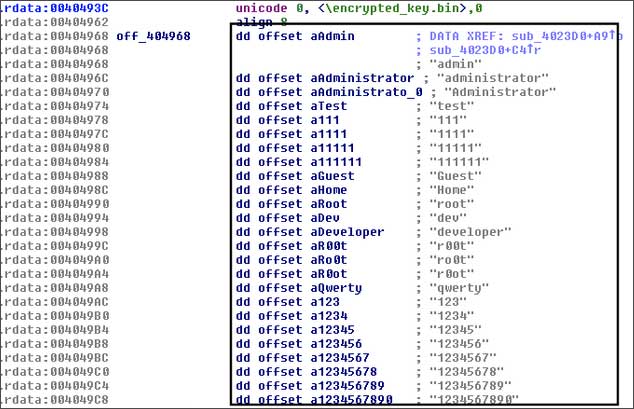
GetCrypt isn’t only encrypting files in the infected device, but is also trying to generate a list of available network shares and then brute force the user credentials and connect to them directly from the compromised system.
image source: bleepingcomputer.com
Have you fallen victim of the GetCrypt ransomware? Let us know of your experience and whether the decryptor worked for you in the comments below. Also, help us spread the word by sharing this post through our socials, on Facebook and Twitter.