The Gamaredon APT Group is Reportedly Intensifying its Activity
- Gamaredon has refreshed their malware and attack toolset, and are attacking Ukrainian targets again.
- Russia and Ukraine are still going through a long and rough period of political and military tensions.
- Cyberwarfare is cheaper and safer to conduct sometimes, and this period is ideal for it.
According to a report by Sentinel Labs, the Russian cyber spy group known as “Gamaredon” is ramping up its efforts in targeting Ukrainian NatSec entities. Apparently, the notorious hacking group has evolved over the last couple of months, deploying new tools and getting more offensive. Reportedly, they are engaging in social engineering, narrow targeting, and advanced cyber-espionage against the Hetman Petro Sahaidachnyi National Ground Forces Academy and other public institutions. By stealing crucial information through the planting of malware, Gamaredon can potentially help pro-Russian groups like the “Donbas” prepare themselves better.
Source: labs.sentinelone.com
The political tensions between Russia and Ukraine are still pretty stretched and have been unstable since the 2014 unrest. Since then, Russian hacking groups have repeatedly tried to infiltrate Ukrainian systems and steal valuable information, and they had partial success in doing that. Last month, Ukraine’s Security Service stated that in 2019 alone, they detected and prevented 482 cyberattacks against critical infrastructure in the country. This means that there was at least one hacking attempt against one of their crucial agencies every single day of the year. If we also account for those that went undetected, you get the idea of the scale of the cyberwarfare that’s underway.
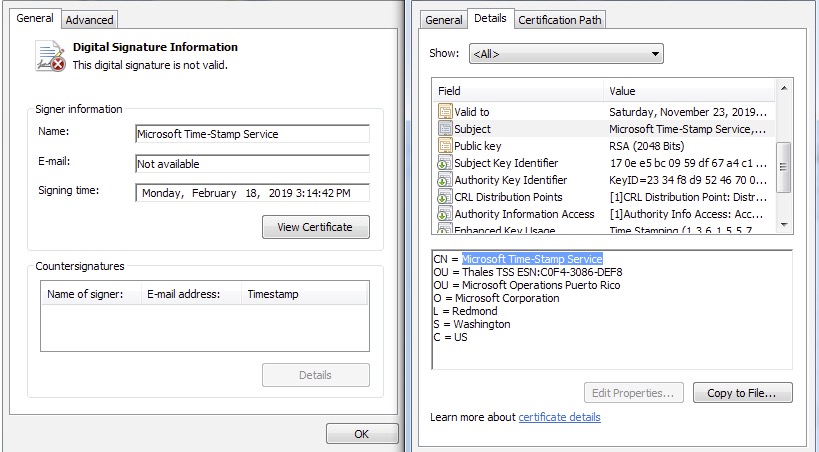
Going on the technical side of the attacks, Gamaredon is using a self-extracting zip archive (.SFX) which contains a batch script, a binary processor, the .NET component, and the macro payloads. Their new malware strain is capable of collecting system data and sending it to C2 servers which can send back additional commands as required. The group is also utilizing a set of server-side forwarders that enable them to process the network traffic that comes and goes on the compromised machine. For versatility and reliability, this system often relies on dynamic DNS providers. Finally, to ensure that there will be no AV triggering, the malware is using a fake Microsoft digital certificate as shown below.
Source: labs.sentinelone.com
The Sentinel Labs researchers attribute the intensification of the Gamaredon activity on the fact that right now, other means of conducting war with Ukraine are either too costly, too risky, or both. As they comment: “From a military perspective, Gamaredon offers a cost-efficiency balance in which attempts to advance on the battlefield do not immediately lead to escalation and retaliation. It is a sophisticated way to opt-out of the traditional zero-sum game of any military operation by achieving offensive advantage without losing a political stance in a peace process.”