‘FlyTrap’ Trojan Spreads Across 144 Countries Through Fake Android Apps
- A new Android Trojan called ‘FlyTrap’ is spreading quickly through fake coupon apps.
- The actors are promoting the malicious APKs on social media through compromised Facebook accounts.
- The database where the exfiltrated information is stored isn’t protected from free public access.
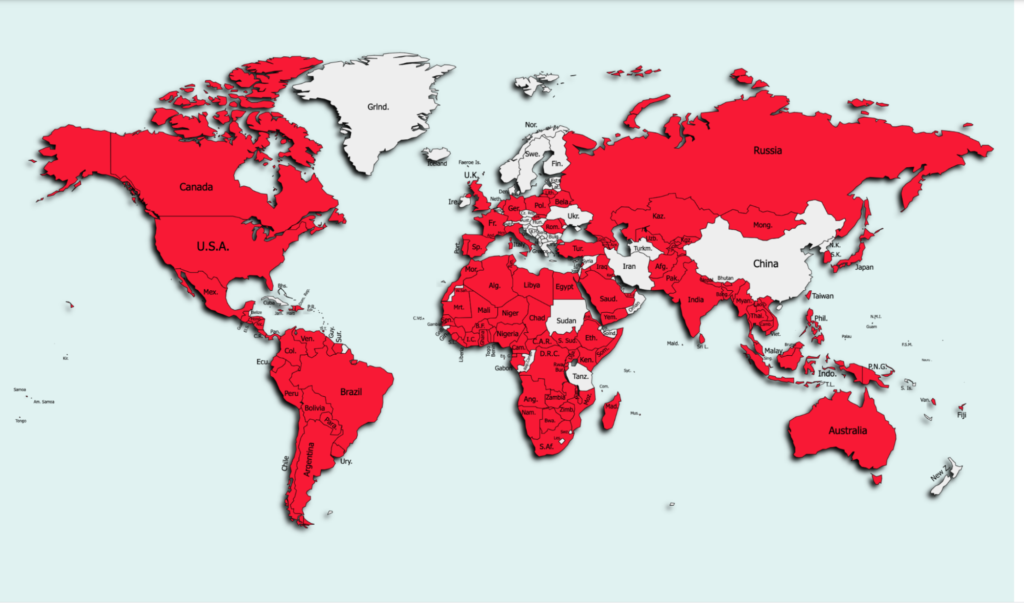
There’s a new Trojan-spreading operation going on out there, and it has already infected thousands of Android devices across 144 countries. The victims were tricked into downloading the malware themselves through social media posts that link to third-party app stores or shady websites that deliver the APKs.
The trojan is named ‘FlyTrap,’ and according to researchers of Zimperium’s zLabs who discovered and analyzed it, it is a novel piece of software. The campaign has been going on since March 2021, and it’s still underway.
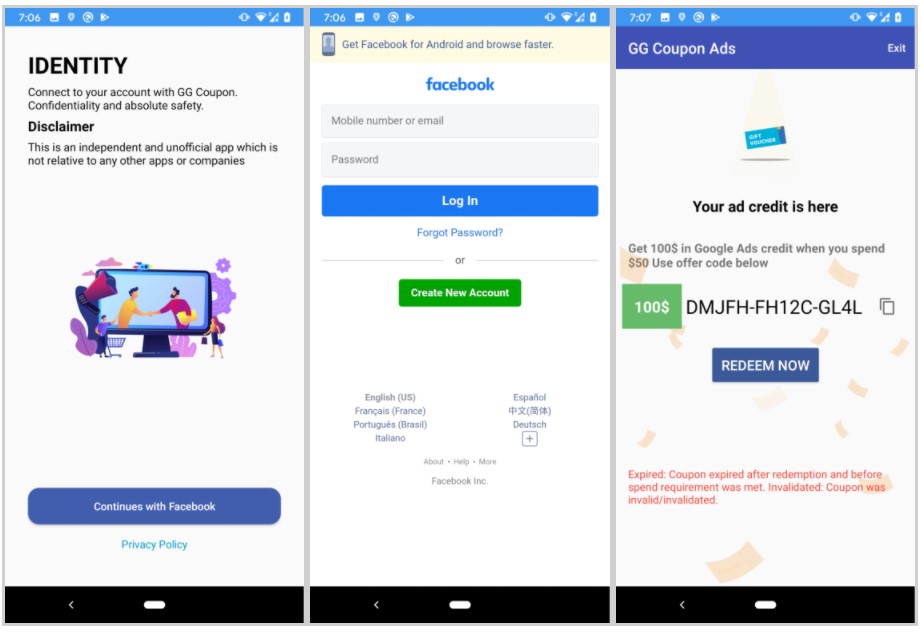
‘FlyTrap’ can steal the victim’s Facebook ID, which is then used to post the promotional links and convince friends of that users to download the malware. Other information collected from the compromised devices includes the location, email address, IP address, and the web browser cookies and tokens required to steal the Facebook or other accounts. It’s all done via JavaScript injection, extracting everything through a legit URL inside a custom WebView.
The lures include free Netflix coupon apps, football player voting apps, Google AdWords voucher apps, etc. Zimperium gives a list of these apps on its blog post, but the actors may very easily replace the entries with different ones, so it’s good to keep that in mind.
In all cases, the user is made to believe they’re one step away from getting a free coupon - until they are eventually served a Facebook account login page that is supposedly used to verify their identity. The actors even provide the promised coupon code, even though it’s totally bogus.
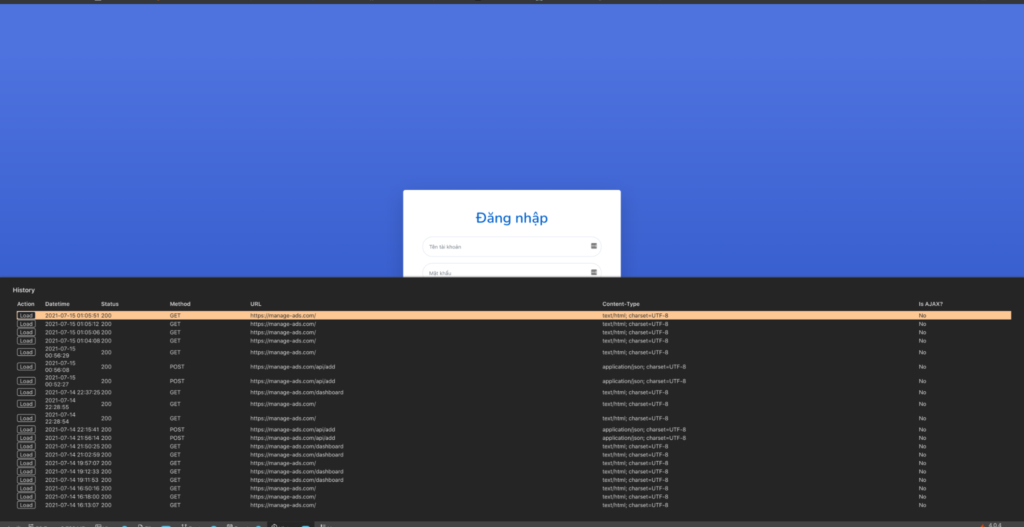
By digging deeper, Zimperium researchers found out that the C2 server used by the actors isn’t properly secured, so anyone can access the exfiltrated data stored in the database, which makes the case even worse for the victims. Operational mistakes of this type aren’t rare in the cybercrime world, as hackers don’t care much about protecting the stolen data from outsiders.
NTT’s vice president, Setu Kulkarni, tells us:
The takeaway here is that you can’t (and shouldn’t) trust anyone blindly, not even your friends on Facebook, as someone else could be hiding behind a direct message from their accounts. If you are urged to download an APK from outside the Play Store, it is most probably malware, and you should not give in to curiosity. If you insist on downloading and installing such an app, make sure that you review the requested permissions carefully before you grant approval and use an up-to-date mobile security solution that could help you catch threats before it’s too late.