Five Popular Password Managers Remain Vulnerable to Security Flaws
- Dashlane, LastPass, Keeper, 1Password, and RoboForm were subjected to multiple security tests.
- Some succumbed to brute forcing, others to clipboard stealing, and others were vulnerable to old and known flaws.
- Two of them even offered to fill out credentials on fake apps masqueraded to look like a Google app.
A team of researchers from the University of New York has decided to re-check how watertight five popular commercial password managers are, and their study is painting a dire picture. The IT scientists created a fake app meant to impersonate a Google app, which actually managed to "convince" two out of the five tested apps to give away their users' passwords. This means that the apps are using poor criteria to figure out whether an app is genuine, and this creates a whole host of security problems.
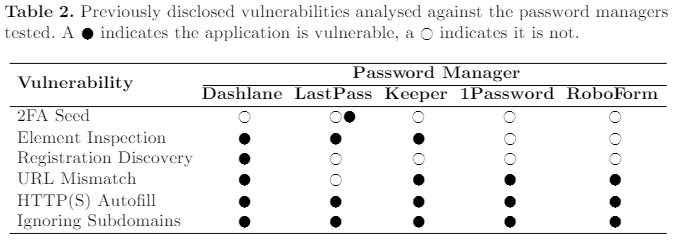
The password managers used in this study are Dashlane, LastPass, Keeper, 1Password, and RoboForm, and the reason for the selection of these particular apps was their massive popularity. The same team had tested the same products back in 2018, on the now-obsolete Windows 10 Enterprise (10.0.14393 build 14393), Chrome 59, and Android 7.0. The researchers re-tested everything against known and disclosed vulnerabilities that the developers of the apps had an ample amount of time to fix. Unfortunately, as seen in the following table, the apps still remain vulnerable to more than 50% of the flaws that were disclosed quite a while back.
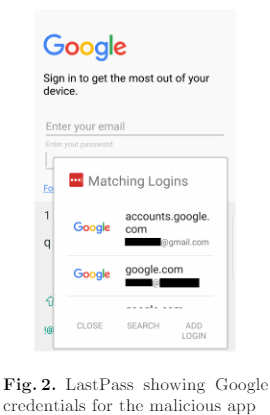
As the above concern older versions of the apps, we assume that most of these flaws have been fixed in the most recent releases. The next chapter in the study is the most interesting, involving the phishing attack through the means of a fake “com.google” app. The apps that failed this test were LastPass and 1Password for Android, both failing to identify that the app was a crafted and non-legitimate one. Since the app featured a login screen, the two password managers offered to autofill it with the user’s stored Google login credentials. The researchers attribute the weakness to the fact that the apps checked only the name of the package that is requesting the password, so exploiting the vulnerability is relatively easy.
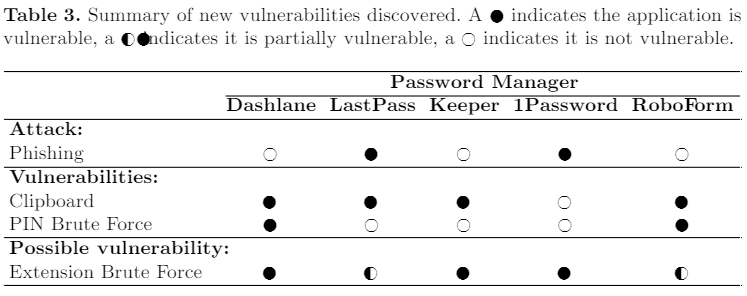
However, that’s not the end of the story. The researchers also tried out brute-forcing the user’s four-digit PIN, either by using a web-based extension or by hitting the app directly. If the apps don’t recognize multiple failed attempts against the user’s PIN, then an automated script would be able to try thousands of combinations in a couple of hours. As the following results indicate, all five password managers were vulnerable either to clipboard stealing attacks or brute-forcing. Some like Dashlane and RoboForm were vulnerable to multiple methods of exploitation.
The researchers have already informed the vendors of the flaws well before publishing this study. Some of the vendors have responded by fixing the issues, while others placed them in a low-priority category and their fate remains unclear right now. For example, 1Password fixed the brute force vulnerability, while Dashlane promised to add a persistent counter to prevent the exploit. This comes as a reminder that nothing can be blindly trusted, and nothing is 100% secure, no matter the marketing claims that surround it. Still, we would recommend using any of the above password managers as we still consider them adequately secure.