First-Ever Confirmed Case of UIA Abuse: Coyote Malware Exploits Microsoft UI Automation
- What happened: Cybersecurity researchers have confirmed the first-ever case of UIA abuse in the wild.
- Why it matters: Behind the exploit is a novel Coyote variant of the malware that was discovered in 2024.
- Malware targets: It uses UIA to steal bank and cryptocurrency exchange credentials from Brazilian users.
A new variant of the Coyote malware has been detected, marking the first confirmed case of UI Automation abuse in the wild. This dangerous evolution amplifies the malware’s ability to target banking institutions and cryptocurrency exchanges, posing a significant cybersecurity threat in 2025.
How Coyote Malware Abuses UI Automation
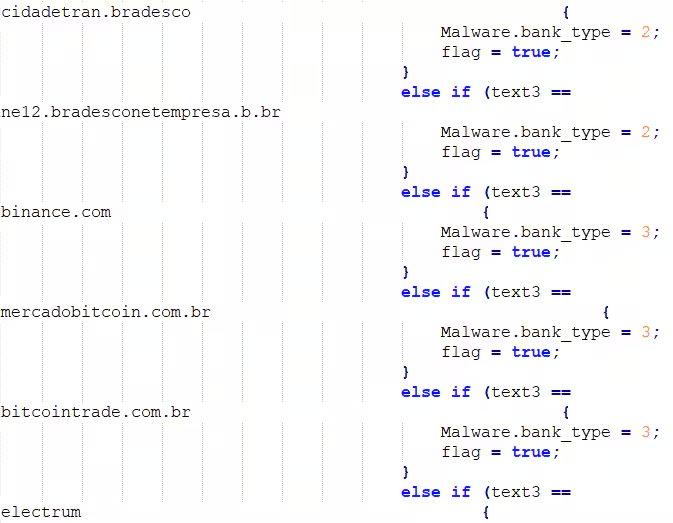
Coyote leverages Microsoft’s UI Automation (UIA) framework to extract sensitive financial information.
The latest report from cybersecurity company Akamai states that the process begins by analyzing active application windows using the GetForegroundWindow() API to identify potential targets.
The API is leveraged to obtain a handle to the currently active window. If it doesn’t match one of the attackers’ hardcoded web addresses of banks and crypto exchanges, Coyote employs UIA to explore the UI elements of the application, such as browser tabs or address bars.
Once a match is found, the malware retrieves information linked to financial services, banking credentials, or cryptocurrency account details. A PoC of UIA abuse for social engineering or extracting sensitive information is also available in the report.
This innovative abuse of UIA removes the need for more complex development strategies, enabling malware creators to parse sub-elements of software applications with minimal effort.
Targets and Impact
The banking trojan primarily focuses on Brazilian users but has the potential to expand globally. It targets over 75 financial institutions, including major banks like Santander and cryptocurrency platforms like Binance, Electrum, Bitcoin, Foxbit, and others:
- Banco do Brasil
- CaixaBank
- Banco Bradesco
- Cryptocurrency (Binance, Electrum, Bitcoin, Foxbit, and others)
- Santander
- Router-app
- Original bank
- Sicredi
- Banco do Nordeste
- Expanse apps
In June 2024, ShinyHunters claimed a Santander Bank breach that affected 30 million customers and employees.
By exploiting UIA, Coyote enhances its data exfiltration precision, increasing the risks of financial theft and broader corporate espionage.
Implications for Cybersecurity
The emergence of UI Automation abuse exemplifies the rapid adaptation of malicious actors in adopting novel attack vectors.
Akamai security experts warn that this evolution in malware tactics necessitates heightened vigilance. Organizations are urged to monitor abnormal UIAutomationCore.dll activity and implement robust endpoint detection measures.
This revelation underscores the importance of proactive defenses against emerging threats like Coyote malware, as attackers continue to find new ways to exploit existing frameworks and compromise sensitive assets.