Finolex Suffers Data Leak Following Conti Ransomware Attack
- The Conti ransomware group claims to have compromised ‘Finolex,’ India’s largest cable manufacturer.
- The actors have already leaked 10% of the stolen data as the extortion process is already underway.
- Finolex hasn’t made any announcements about a security incident yet, but the leaked data appear genuine.
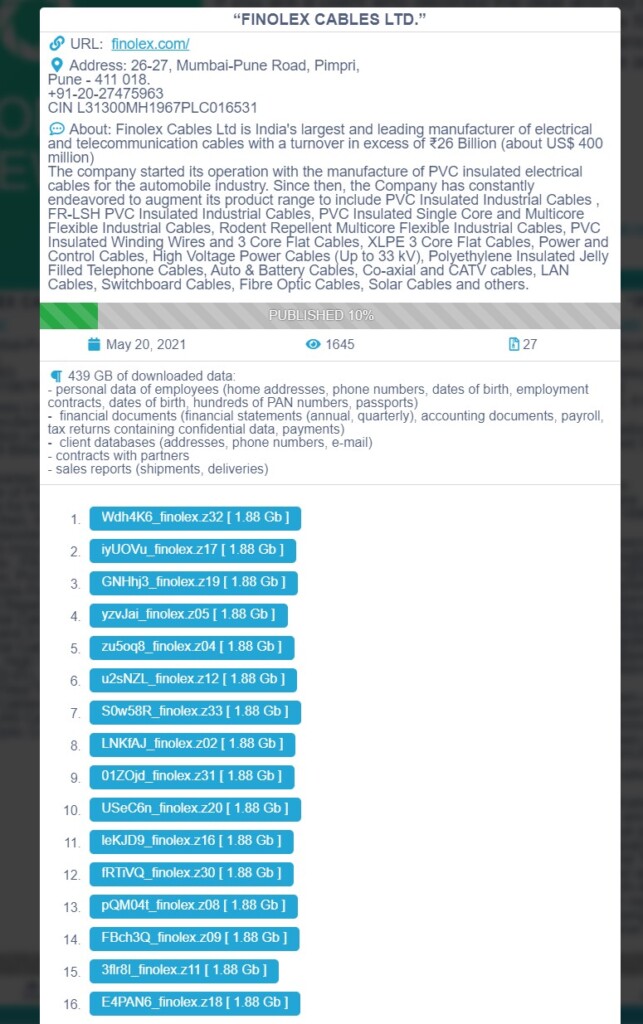
The Conti ransomware group, one of the few RaaS operations that remain alive and public after the Colonial Pipeline attack that shook the field, is now claiming to have compromised Finolex, India’s largest electrical and telecommunication cables manufacturer. Finolex has an annual revenue of around half a billion USD and operates three large ISO-9001-certified manufacturing plants in Pimpri, Urse, and Goa. As such, they are a lucrative target for Conti and any ransomware group for that matter.
The actors claim to have stolen 439 GB of data including the following:
- Personal details of employees (home addresses, phone numbers, dates of birth, employment contracts, PAN numbers, passport scans);
- Financial documents (annual statements, quarterly reports, accounting documents, payroll documents, tax returns containing confidential data, etc.);
- Client databases (shipping addresses, phone numbers, email addresses);
- Partner contracts;
- Sales reports (shipments, deliveries, etc.).
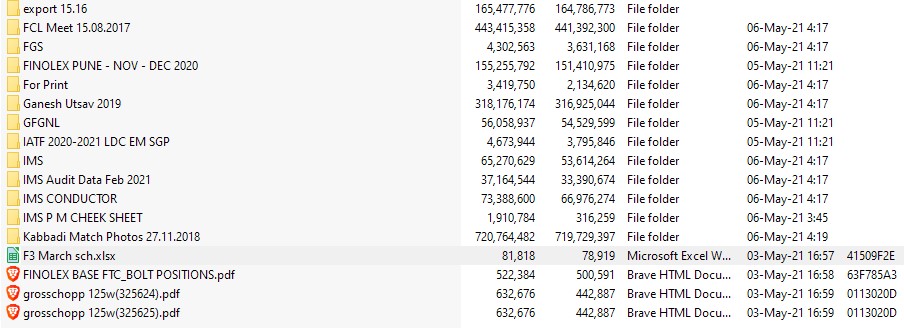
So far, Conti has leaked a 10% of the stolen documents to prove that they mean business and also to raise the heat of extortion. We have taken a look at the shared samples to confirm the validity of the data, and unfortunately, it looks authentic. Here is a sample of the stolen data accessed by TechNadu:
While this story was being written, the website of Finolex was up and running and then it went offline, so there appears to be an interruption on the front-facing services, a sign of network/machines encryption. As for the company’s three production units, we couldn't find any announcements declaring any kind of a problem, but it's too early for this to come out publicly. As always, we have contacted the alleged victim, and we will update this piece as soon as we hear back from them.
In the meantime, Conti is now leaking patient data it stole from the recent attack to the Irish Health Services (HSE) on the dark web, as the public entity isn’t willing to pay or even negotiate the requested ransom of $20 million. That exposure should be followed by the announcement of an investigation from the Irish Data Protection Commission, as the leak of patient data constitutes a violation of the GDPR.