FIN6 Distributes More_eggs Malware via Sophisticated Campaigns Leveraging Trusted Services
- The FIN6 threat actor was seen exploiting trust through social engineering in a new malware campaign.
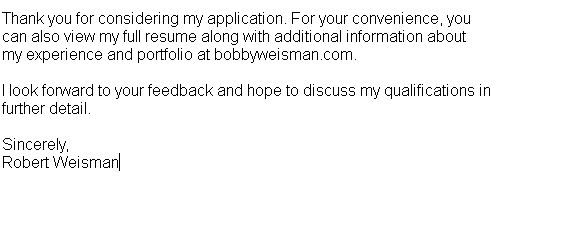
- Malicious emails promote fake resumes hosted on websites that are not hyperlinked to deliver the More_eggs malware.
- Attackers use IP reputation and geolocation, operating system and browser fingerprinting, and CAPTCHA verifications.
FIN6, also known as Skeleton Spider, is continuing to evolve its tactics as a financially motivated cybercrime group. Known originally for point-of-sale breaches and payment card theft, the group has recently shifted to more elaborate enterprise-focused attacks, including ransomware distribution.
Its latest operation leverages trusted cloud platforms like AWS, making detection and takedown efforts significantly more challenging for cybersecurity teams, according to the latest DomainTools Investigations (DTI) security report.
A key component of FIN6’s current strategy is impersonating job seekers to engage recruiters in professional conversations via LinkedIn and Indeed.
The group, also tracked as Camouflage Tempest, Gold Franklin, ITG08, Skeleton Spider, and TA4557, uses meticulously crafted phishing emails that include fake resume links that are non-clickable to bypass automated link detection due to forcing the recipient to manually type the URL into their browser.
These fake CVs are often hosted on domains created to mimic real applicants.
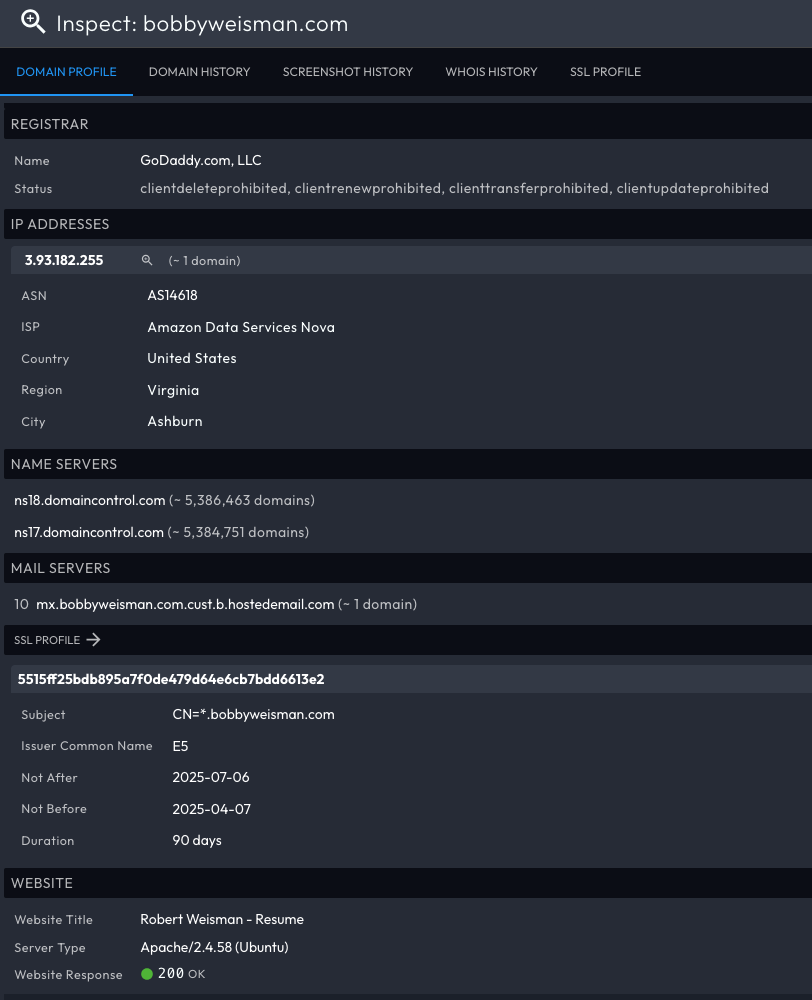
FIN6 further escalates trust by hosting these phishing sites on reputable cloud platforms like AWS. This creates landing pages that appear legitimate to victims, complete with resumes and CAPTCHA verifications, designed to filter and deliver malicious payloads exclusively to targeted users.
The group employs the More_eggs malware as its primary payload, a modular JavaScript-based backdoor capable of credential theft, system access, and follow-on attacks. This malware is often hidden within ZIP files containing disguised .LNK files, which execute scripts to deploy the backdoor.
To evade detection, FIN6 uses traffic-filtering techniques, CAPTCHAs, and environmental fingerprinting to ensure the malicious content only reaches legitimate targets.
Security researchers confirmed the following domains are hosted on AWS infrastructure:
- bobbyweisman[.]com
- emersonkelly[.]com
- davidlesnick[.]com
- kimberlykamara[.]com
- annalanyi[.]com
- bobbybradley[.]net
- malenebutler[.]com
- lorinash[.]com
- alanpower[.]net
- edwarddhall[.]com
By leveraging AWS services such as CloudFront and S3, FIN6 successfully obscures its infrastructure and creates an environment resistant to detection and blocking. Using trusted platforms provides inherent credibility, enabling attackers to bypass both enterprise filters and automated threat detection systems.
The scalable and cost-effective nature of cloud computing also allows attackers to set up disposable infrastructure quickly, increasing the sophistication of their campaigns.
Offering the right platform to report and curb further abuse, an AWS spokesperson shared the following with TechNadu:
“AWS has clear terms that require our customers to use our services in compliance with applicable laws. When we receive reports of potential violations of our terms, we act quickly to review and take steps to disable prohibited content. We value collaboration with the security research community and encourage researchers to report suspected abuse to AWS Trust & Safety through our dedicated abuse reporting process.”
This story has been updated with a comment from an AWS spokesperson in the public interest.