How the FBI Identified a Dark Web Opioid Dealer in the U.S.
- A man from Florida was casually using his nearby postal service to push drugs across the U.S.
- The person attempted to use a false identity but couldn’t hide much otherwise.
- The FBI agents who ordered 12 times from him had rich data in their hands, so they could track him down.
People who sell drugs on the dark web hide behind VPNs to mask their true IP address and use an anonymous email account. Oftentimes, they also use a fully anonymized operating system like Tails, which passes all network activity and data through the Tor network, so essentially all tracks are lost in the bouncing process.
So, when someone is arrested, many wonder how the law enforcement authorities managed to figure out their real identity. Here’s a story coming from the U.S. Postal Inspection Service, detailing how they helped the FBI track down an opioid seller.
The investigation started from an account on the Empire Market using the nickname “chlsaint” and selling fentanyl, heroin, oxycodone, oxymorphone, and other opioids. The account was opened in August 2019, and it had a customer feedback rating of 98%, which is an indication that the 1,100 orders placed on the vendor were fulfilled. This convinced the FBI to investigate deeper, and so they placed an order and provided a shipping address in California.
When the package arrived, the authorities noticed a hand-written return address “Stephanie Smith 301 SW 7th Ave Delray Beach, FL 33444.” Also, they confirmed that the shipment was sent through USPS Self Service Kiosk (SSK) in Delray Beach, Florida. So, the feds had a crucial clue in their hands already and could continue the investigation in a more targeted fashion.
They requested video footage from the SSK store captured on the date of the drop-off, which was also known thanks to the postal service’s tracking system logs. Having the vendor’s face image, they then checked with the Florida Department of Motor Vehicles as well as Florida jails, and indeed, they’ve found numerous matches on both. The name was Chaloner Saintillus, a 32-year-old from Delray Breach.
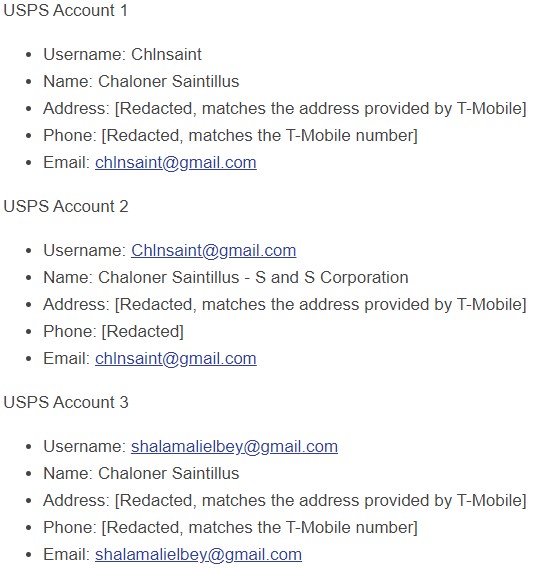
Next, the FBI searched for telecommunication service providers who had accounts associated with that name, and T-Mobile returned with something, although the name of the registrant was Shalam Ali. Having an address and a second name now, the feds checked with USPS and found three registered accounts with several similarities. They’ve also found associations between the email addresses, the declared names, and the mobile numbers.
The dots between Saintillus and ChInsaint were now connected, and after some more digging on social media profiles, the feds found that the man was using the same Shalam to introduce himself to other users. They also found that Saintillus was using Wickr and Telegram to sell stuff outside the dark web markets to avoid paying them their usual cut.
The feds ordered another 11 packages, monitored the USPS payments, identified a Wells Fargo debit card, the bank accounts associated with it, and learned about other SSK purchases. Then the physical surveillance started on the last known address, and soon, Saintillus was arrested and charged. The envelope he left on the SSK right before the moment of his arrest was opened with a warrant and found to contain seven grams of fentanyl.