Fake Zoom Call Phishing Campaign Steals User Credentials Backed by Interactive Meeting Participants
- What happened: Attackers exploit user trust in legitimate brands like Zoom to obtain workplace login credentials.
- How it works: Phishing emails that create a sense of urgency include Zoom meeting links leading to pages that appear authentic.
- Data stolen: Zoom workplace credentials, IP address, country, and region are exfiltrated.
A new phishing campaign leveraging malicious Zoom invitations is targeting workplace credentials via deceptive hyperlinking or URL masking and fake interactive call pages, ultimately prompting users to ‘rejoin’ after a fake connection issue.
The campaign posing substantial risks to individuals and organizations alike was detailed in the Cofense Phishing Defense Center's latest security report.
Phishing Campaign Tactics
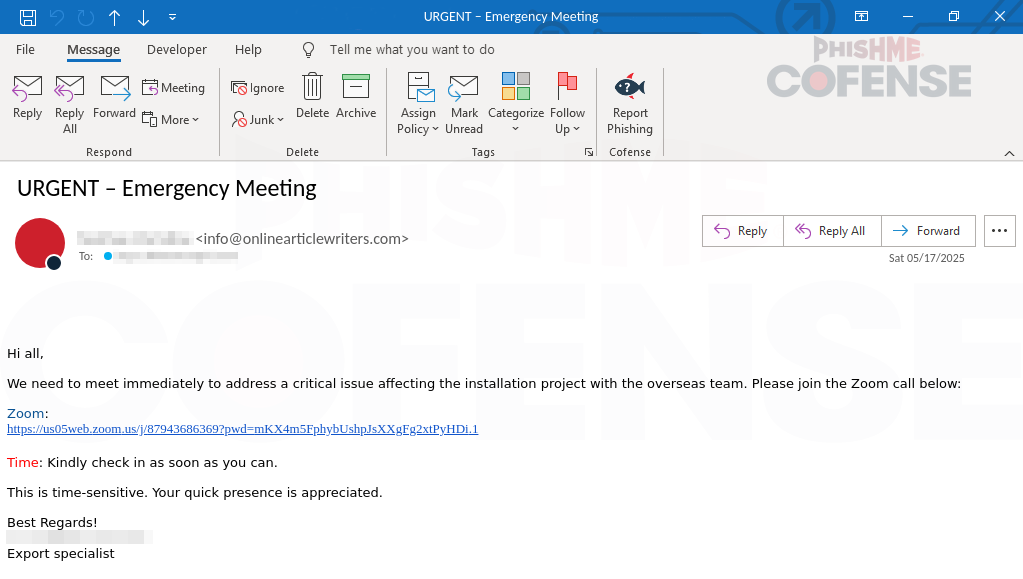
This campaign manipulates recipients into urgency-based actions, as email subjects such as "URGENT - Emergency Meeting" are crafted to trigger immediate responses.
They contain links to fake Zoom meeting interfaces designed to appear authentic, which is known as deceptive hyperlinking or URL masking, complete with realistic visuals..
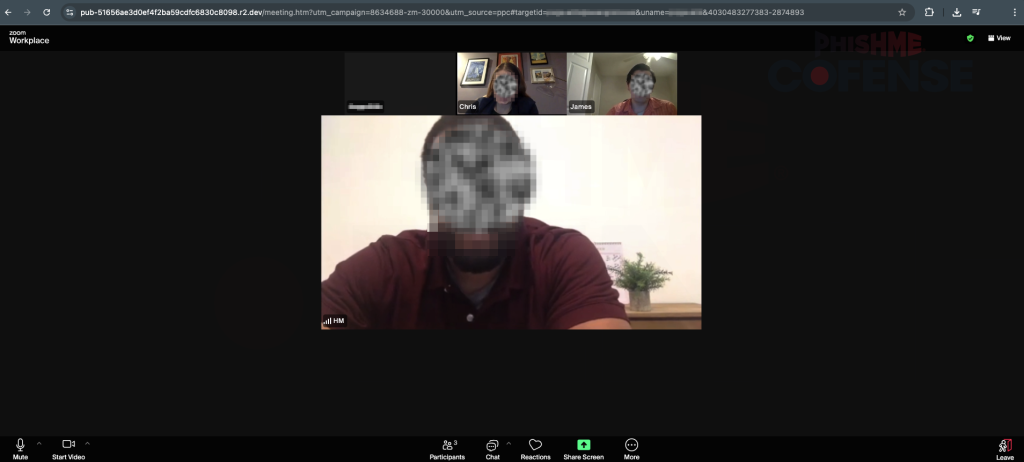
In this campaign, the landing page URL is visibly different from the legitimate one and even features interactive meeting participants.
However, a dialog box invoking a connection timeout appears shortly, redirecting users to malicious landing pages that mimic Zoom's login interface, sometimes complete with pre-filled email fields, allegedly allowing them to rejoin the session.
Once credentials are entered, these and the IP address, country, and region are sent through secure channels, such as Telegram, to the attackers.
Risks of Zoom Credential Theft
Compromised credentials allow attackers to infiltrate enterprise systems, enabling lateral movement, data theft, and Advanced Persistent Threats (APTs). These attacks can jeopardize organizational security, leading to significant financial and reputational damage.
How to Stay Protected
Abu Qureshi, Threat Research and Mitigation Lead at BforeAI, provided TechNadu with essential phishing prevention tips, stating that identifying phishing platforms “is technically possible, but it requires awareness and vigilance.”
To safeguard against these Zoom phishing attempts, consider these online security tips:
- Verify URLs: Legitimate Zoom links will end with “zoom.us.”
- Avoid Email Links: Access meetings directly through the Zoom app or a trusted bookmark.
- Inspect for Legitimacy: Verify HTTPS encryption and valid certificates before entering your credentials.
- Enable Multi-Factor Authentication (MFA): Add an extra layer of security to your Zoom account.
- Employee Training: Equip employees with the knowledge to recognize phishing campaigns through regular security awareness programs.
This fake Zoom call phishing attack highlights the importance of vigilance and robust cybersecurity practices to prevent Zoom credential theft and protect sensitive organizational assets.