Fake WordPress Caching Plugin Steals Admin Credentials and User Capabilities
- A fake WordPress plugin exfiltrates administrator credentials from compromised websites.
- It masquerades as a runtime cache tool but lacks common functionality and transparency.
- Upon any administrator login attempt, the plugin collects the username, password, and user capabilities.
A recently observed sophisticated attack relies on a fake WordPress plugin disguised as a caching utility, "wp-runtime-cache," which is actively stealing administrator credentials from compromised websites.
Security analysts at Sucuri discovered and dissected the plugin, highlighting both its stealth tactics and targeted exploitation.
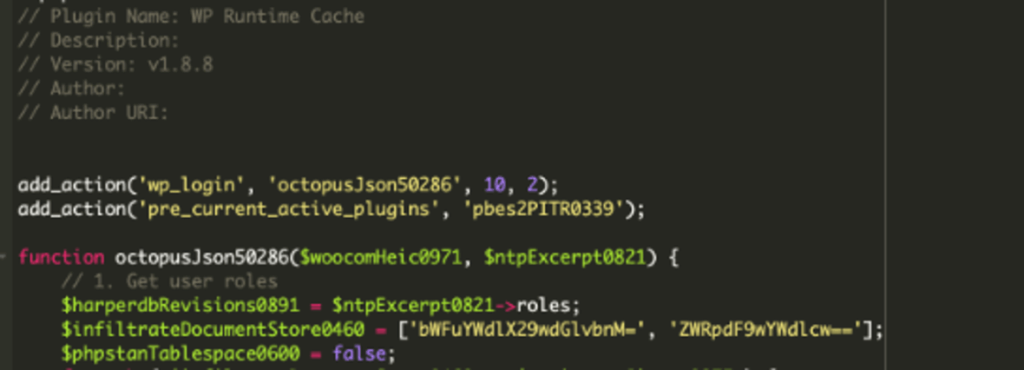
Threat actors are embedding the "wp-runtime-cache" plugin within the wp-content/plugins directory. Despite appearing harmless, this plugin entirely lacks the typical functionality or transparency of legitimate caching tools.
Notably, it is missing from the WordPress admin's installed plugin list, a common tactic attackers use to evade casual detection.
The malicious plugin operates with a single PHP file containing heavily obfuscated code, utilizing random variable names and base64 encoding to mask its behavior. Upon any administrator login attempt, the plugin collects the username, password, and user capabilities.
Targeting specifically users with "manageoptions" or "editpages" privileges, it then exfiltrates these credentials to an external server disguised via further base64 encoding.
The destination has been traced to a recently registered domain, "woocommerce-check[.]com," which exhibits inconsistencies in registration details, signaling attempts to obfuscate attribution and evade blacklist checks.
Additionally, the plugin contains logic to conceal itself from the plugins list entirely, unless accessed by the attacker, allowing persistent access without alerting site administrators.
This campaign highlights the growing sophistication of plugin-based malware targeting WordPress, emphasizing the critical need for ongoing plugin audits and monitoring of unauthorized file changes.
The attack demonstrates how easily a compromised plugin can bypass standard security checks, grant attackers privileged access, and facilitate lateral movement within site infrastructures.
The evolving nature of these attacks reinforces the necessity for strict security hygiene and proactive monitoring, particularly within widely used platforms like WordPress.