Fake ‘Booking.com’ Sites Lure Victims Into AsyncRAT Infection
- Cybercriminals disseminate the AsyncRAT backdoor Trojan via websites impersonating legitimate booking services.
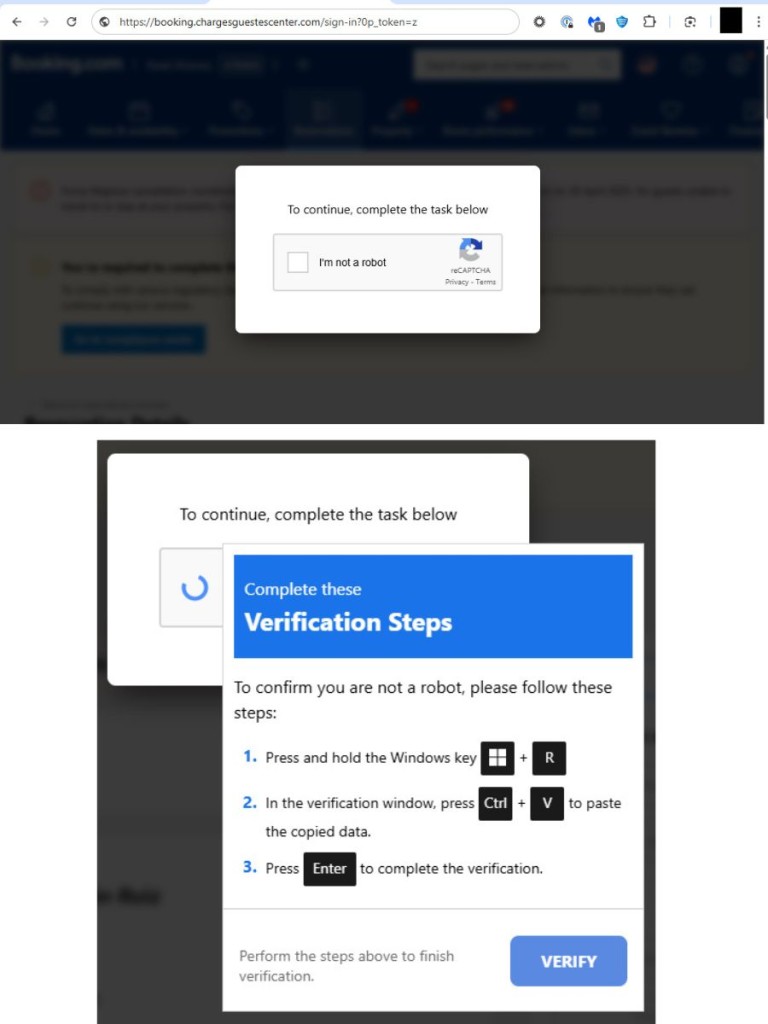
- Fake ‘Booking.com’ platforms leverage fake CAPTCHA to convince users into running malicious commands.
- Attackers can steal sensitive credentials, harvest financial information, and even orchestrate identity theft.
A sophisticated new cybercriminal campaign is redirecting users from gaming sites, social media, and sponsored ads to convincing fake versions of Booking.com, posing a significant risk for travelers booking accommodations online.
Security researchers at Malwarebytes identified this threat in mid-May, noting that as many as 40% of consumers book travel after a general online search, making them prime targets for ongoing redirection attacks.
The attackers employ a familiar but highly effective lure. Users who click these rogue links land on imitation Booking.com sites with deceptive CAPTCHA prompts. Unwitting users who interact with the fake CAPTCHA inadvertently grant the site permission to manipulate their clipboard.
The website then instructs visitors to paste copied, obfuscated PowerShell code into their system's Run dialog. If executed, this code downloads and runs a sequence of malicious executables, ultimately deploying the Backdoor.AsyncRAT malware.
AsyncRAT is a remote access trojan designed to covertly monitor and control infected systems. Once established, attackers can steal sensitive credentials, harvest financial information, and even orchestrate identity theft, severely compromising both individuals and organizations.
Indicators of compromise from this campaign include rapidly rotating domains such as chargesguestescenter.com, badgustrewivers.com, property-paids.com, and the primary downloader host, bkngnet.com. The malicious infrastructure is updated every few days to evade blacklisting.
Among the recommendations for mitigation are scrutinizing all travel booking URLs, especially those from search engines or ads, and never executing commands copied from web pages, particularly PowerShell commands.