Evolving Phishing Campaigns Deliver HoldingHands Malware across China, Taiwan, Japan, and Malaysia
- Expanding operations: A threat actor has expanded its operations from China to Taiwan, Japan, and most recently, Malaysia, using evolving malware delivery tactics.
- Primary malware: The campaigns have distributed multiple malware families, including Winos 4.0 and the more recent HoldingHands backdoor.
- Advanced evasion: The latest HoldingHands variant utilizes the Windows Task Scheduler service as a trigger mechanism.
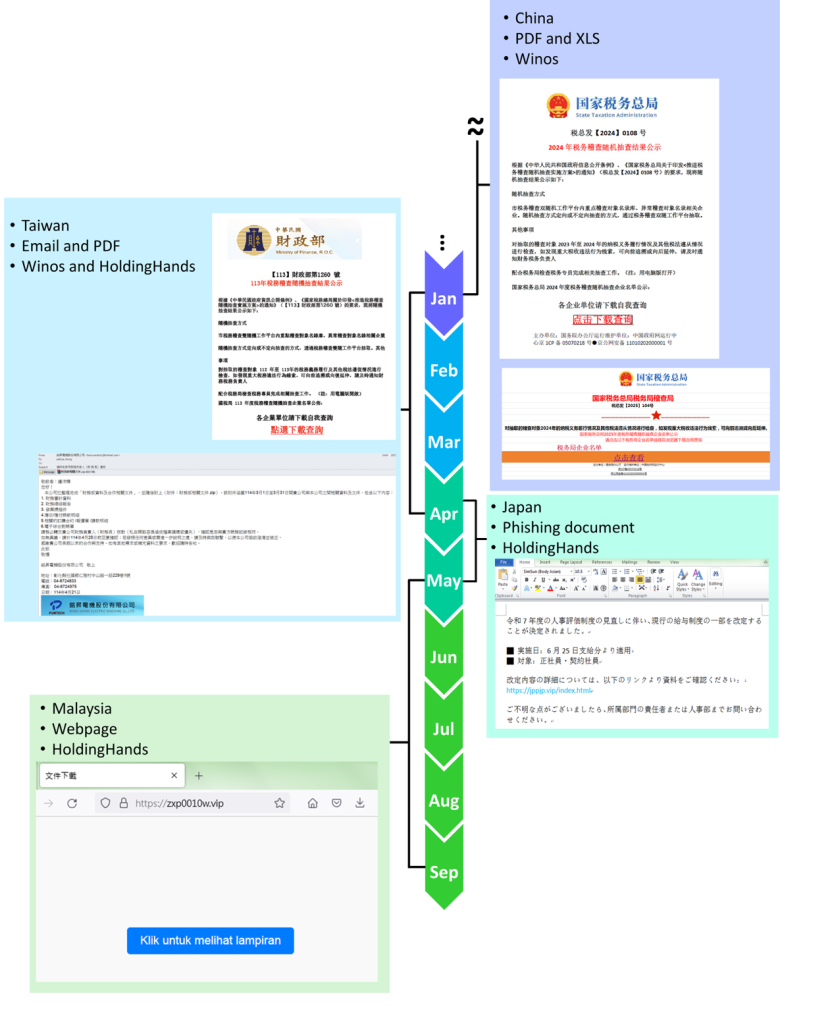
A sophisticated hacker group is expanding its attack campaigns across several Asian countries. FortiGuard Labs has connected a series of phishing attacks that initially targeted users in China and Taiwan before shifting focus to Japan and Malaysia to deliver the HoldingHands backdoor.
Analysis of Attack Methods and Infrastructure
The threat actor relies on phishing emails containing PDFs that masquerade as official government documents, such as those from the Ministry of Finance. These documents contain embedded malicious links that lead to the download of malware payloads.
The investigation connected the seemingly disparate Asian cyberattacks by analyzing shared infrastructure and code patterns.
Early campaigns utilized links to Tencent Cloud storage, enabling analysts to attribute multiple malicious files to the same operator using unique account IDs, apparently targeting China.
The primary payload identified in recent campaigns is the HoldingHands malware, a backdoor delivered through a complex, multi-stage infection process. The initial lure often involves a legitimate executable that is used to side-load a malicious DLL.
Later attacks utilized custom domains with regional naming patterns, such as including "tw" for Taiwan, to host the malware. A PDF that posed as a draft of a tax regulation for Taiwan redirected to a page in Japanese containing a HoldingHands payload ZIP.
Evolving Evasion and Detection Challenges
The latest variant of HoldingHands, observed in the campaign targeting Malaysia, demonstrates more advanced evasion techniques. Unlike earlier versions that left forensic artifacts by dropping files to disk, the new variant leverages the Windows Task Scheduler.
By terminating and allowing the service to restart, the malware triggers its next stage via the svchost.exe process, complicating detection by security tools.
The malware also performs anti-analysis checks, including verifying the process name and command-line arguments, to ensure it is running in its intended environment. This evolution highlights the threat actor's persistent efforts to refine its methods and evade security defenses.
“What concerns me most is the evolution from direct file-dropping to service recovery abuse, indicating they're actively adapting to your security controls through strong defensive feedback integration,” said Certis Foster, Senior Threat Hunter Lead at Deepwatch, recommending the deployment of registry monitoring for the HHClient and Task Scheduler service correlation.
Foster identified two high-confidence detection opportunities. He says HoldingHands creates a unique registry key at HKEY_CURRENT_USER\SOFTWARE\HHClient with value name "AdrrStrChar" storing C2 server addresses 100% unique to this threat, with zero expected false positives, and recommends implementing registry monitoring using your existing endpoint detection platform, SIEM correlation rules, or Windows event logging.
Second, they exploit service recovery by stopping the Windows Task Scheduler. “Within 120 seconds, svchost.exe restarts with the command line svchost.exe -k netsvcs -p -s Schedule, highly anomalous with extremely low false favorable rates.” He suggests correlating service state changes with process creation events using your existing security monitoring stack.
In other recent news, Taiwan reported a surge in Chinese cyberattacks. Earlier this month, TechNadu reported on a Phantom Taurus APT and NET-STAR malware Espionage Campaign targeting government and telecom entities.