Evil Clippy Helping PenTesters Figure Out How to Secure MS Office
- Clippy is back and meaner than ever, but this time, it wasn’t unleashed by Microsoft.
- The document macro pusher has the capacity to trick AV products and maldoc analysis tools.
- Microsoft needs to share more about how macros work in MS Office so that AV vendors get to offer more reliable detection tools.
For those of you old enough to remember, Clippy was Microsoft’s virtual assistant for MS Office, popping up and offering you its help with writing a business letter or typing a special character, or anything that it thought was relevant to what you were doing. Almost no one liked the somewhat intrusive ways of the little virtual paperclip, so Microsoft decided to pull out the feature after two versions. The “Evil Clippy” that was presented during the most recent “BlackHat Asia” is not some kind of a “vengeance-seeking” version of the old-school assistant, but a pen-testing tool that was explicitly developed by researchers to help them determine what works against MS Office and what doesn’t.
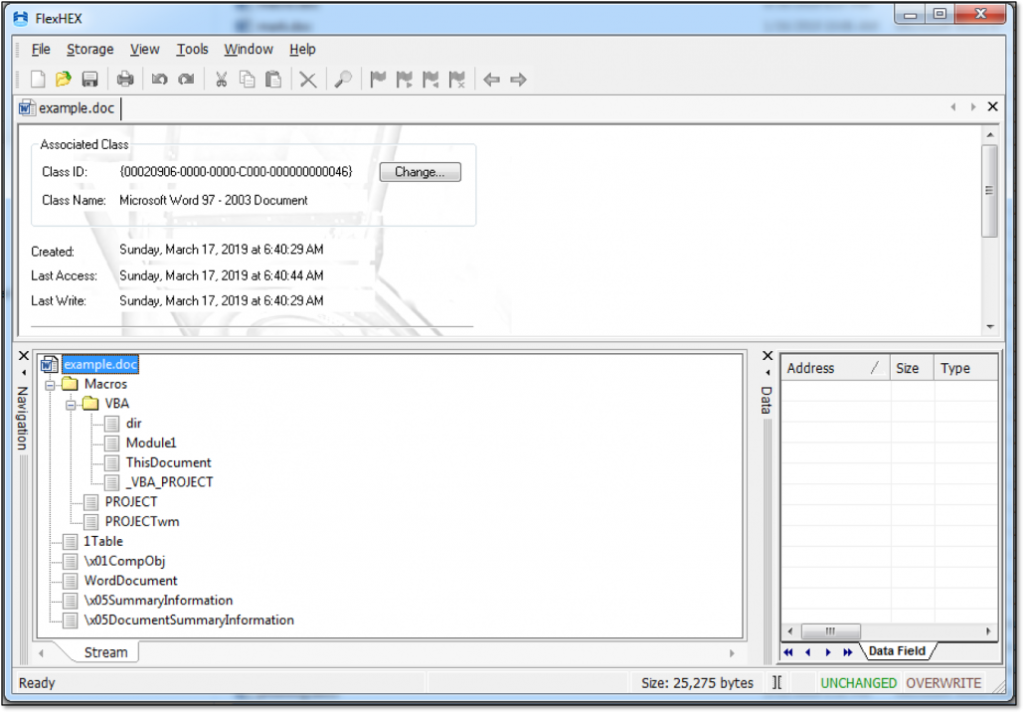
More specifically, the Evil Clippy can hide VBA macros, stomp VBA code (via p-code) and confuse popular macro analysis tool. Evil Clippy helps researchers abuse undocumented features such as the pseudo-code of each module in the VBA engine. It can work on all three major operating systems, serving stomped templates via HTTP, and even hide the malicious macros from analysis tools that incorporate GUI editors (by modifying the PROJECT stream). The Evil Clippy supports the “CFBF” (Compound File Binary Format), including .doc and .xls files of the ‘97 and 03’ versions, as well as .docm and .xlsm of the ‘07 version.
image source: outflank.nl
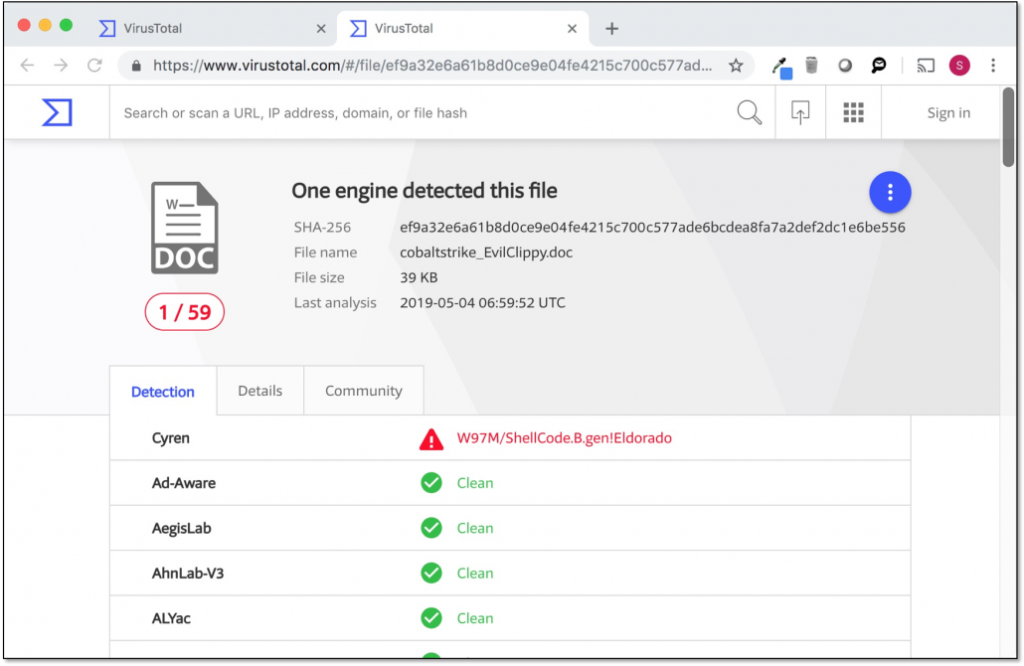
According to its creators, Outflank, the macros that are pushed via Evil Clippy can bypass all current security measures, and no AV product or maldoc analysis tool is able to catch it. By employing high levels of ambiguity and complexity of the MS-OVBA specification, and by setting a random ASCII module name, the team discovered that most analysis tools are getting confused and often crash.
image source: outflank.nl
Now, the point of developing these tools and freely sharing them with the community is to help Microsoft and all stakeholders to take preventive action. Evil Clippy is a demonstration of what can be done by exploiting undocumented MS Office macros features, and according to its creators, it only scratches the surface really. Microsoft needs to adopt a more “openly-sharing” approach on things that have the potential to affect the users of its products with such a profoundly negative impact, especially when pen-testing groups prove that AV tools are unable to play a preventive and protective role on that part. Until that happens, be careful with what document you download from the internet, and disable the macros functionality on your suite if you don’t really need it.
Care to share any thoughts on the above? Feel free to do so in the comments down below, or on our socials, on Facebook and Twitter.