Evelyn Stealer Malware Targets Software Developers via Visual Studio Code Extensions
- Targeted Attack: The Evelyn Stealer campaign specifically targets software developers by distributing malware through malicious Visual Studio Code (VSC) extensions.
- Multi-Stage Payload: The attack utilizes a multi-stage delivery process, starting with a downloader disguised as a legitimate DLL, which deploys the Evelyn infostealer.
- Data Exfiltration: The primary goal is to exfiltrate sensitive data, including developer credentials, system information, and cryptocurrency wallet details, via FTP.
A sophisticated cyberattack, dubbed the Evelyn Stealer campaign, is actively targeting software developers by weaponizing the Visual Studio Code (VSC) extension ecosystem. Threat actors are luring developers into installing malicious extensions that serve as an entry point for a multi-stage information-stealing malware.
This campaign highlights a significant security risk within the software development lifecycle, as compromised developer environments can provide attackers with privileged access to broader organizational systems, source code repositories, and production infrastructure.
Technical Analysis of the Attack Chain
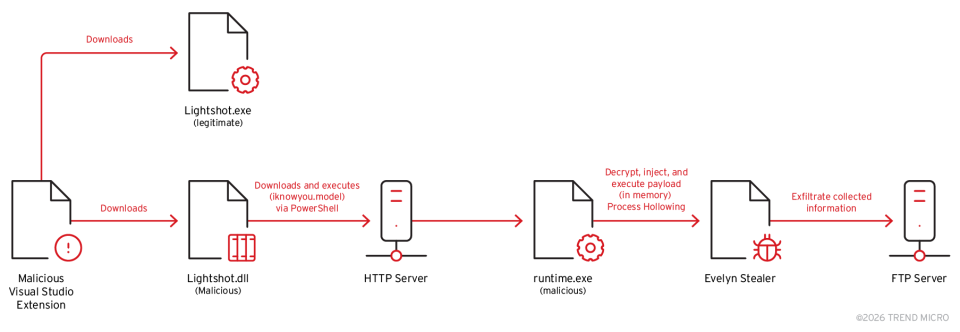
The attack begins when a developer installs a compromised VSC extension, the latest TrendMicro security report said, treating the developer environment itself as the delivery mechanism. This action triggers the execution of a downloader disguised as a legitimate Lightshot DLL component.
This first stage uses a hidden PowerShell command to fetch a second-stage payload, leading to the injection of the final payload, Evelyn Stealer, into a legitimate Windows process using a technique known as process hollowing.
“Evelyn Stealer dynamically resolves all Windows APIs needed for malware operations, including process injection, file operations, registry access, network communication, and clipboard access,” the report said.
The infostealer is equipped with advanced capabilities such as AES-256-CBC encryption and multiple anti-analysis and anti-sandbox capabilities to evade detection. It checks for virtual machines (VMs), debuggers, and analysis environments like Remote Desktop Protocol (RDP) sessions and Hyper-V.
Once active, it harvests a wide range of data, including browser credentials, Wi-Fi credentials, system information, clipboard contents, and cryptocurrency wallet files.
Cybersecurity for Developers and Mitigation
This infostealer campaign exploits trusted development tools like VSC, which demonstrates that no environment is entirely safe from developer-targeted cyberattacks.
Organizations are advised to implement strict vetting processes for all third-party extensions and tools, and developers should exercise caution and verify the authenticity of extensions before installing them.
Furthermore, employing endpoint detection and response (EDR) solutions and maintaining a zero-trust architecture can help detect anomalous behavior.
In October 2025, researchers discovered that the TigerJack malware infected over 17,000 developers, stealing code and mining crypto via malicious VSC extensions. Two campaigns targeted developers in March 2025: the Lazarus Group’s new wave of malicious npm packages and a fake hiring challenge disseminating the FogDoor backdoor.