ErrTraffic ClickFix Tool Industrializes Social Engineering Malware, Delivers Fake Website Glitches
- Commoditized Cybercrime: An ErrTraffic v2 panel is lowering the entry barrier for social engineering campaigns.
- Efficacy: Conversion rates approach 60%, achieved through highly deceptive "fake glitch" visual overlays.
- Cross-Platform: The architecture intelligently fingerprints victim operating systems to deliver tailored payloads across Windows, macOS, Android, and Linux environments.
Researchers at Hudson Rock noticed the emergence of the ErrTraffic ClickFix tool. This service-based malware suite represents the industrialization of "ClickFix" tactics: deceptive overlays that trick users into manually executing malicious code.
This development marks a transition from bespoke intrusion methods to accessible, high-volume infection services that leverage legitimate SaaS-like dashboards to track infection metrics.
Technical Mechanics of the ClickFix Lure
Marketed by a threat actor known as "LenAI" on Russian-language forums, ErrTraffic v2 creates a streamlined pipeline for deploying high-yield social engineering malware. Infostealers by Hudson Rock reported that ErrTraffic differentiates itself through advanced visual deception and technical evasion.
The tool injects malicious JavaScript into compromised websites to generate "fake glitches," such as corrupted text or rendering errors, creating a false sense of urgency.
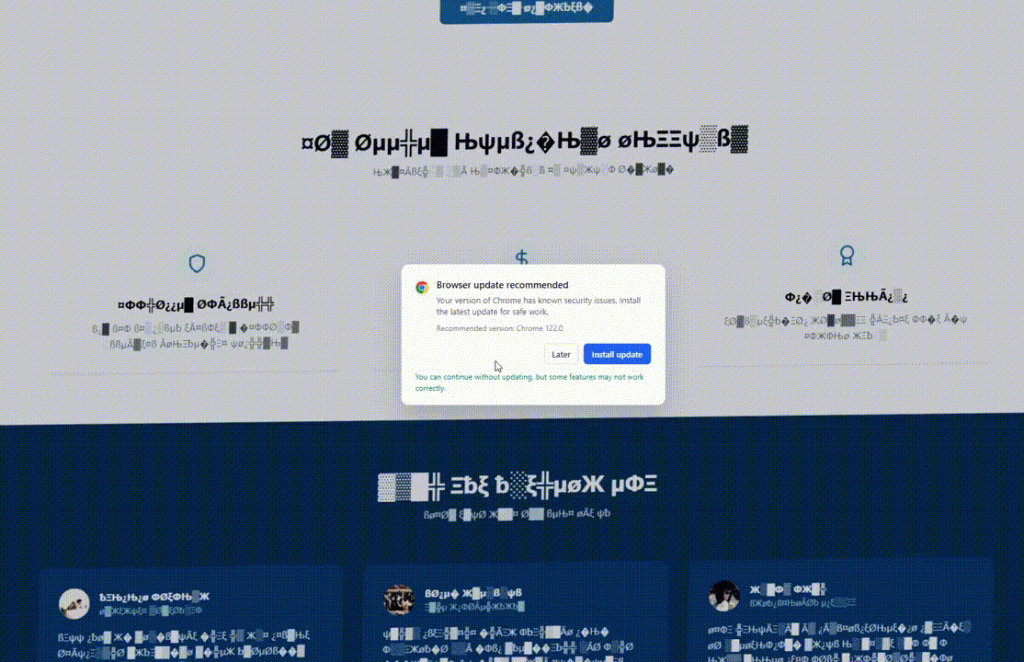
To "fix" the issue, users are prompted to copy and paste a verification code into the Windows Run dialog or PowerShell.
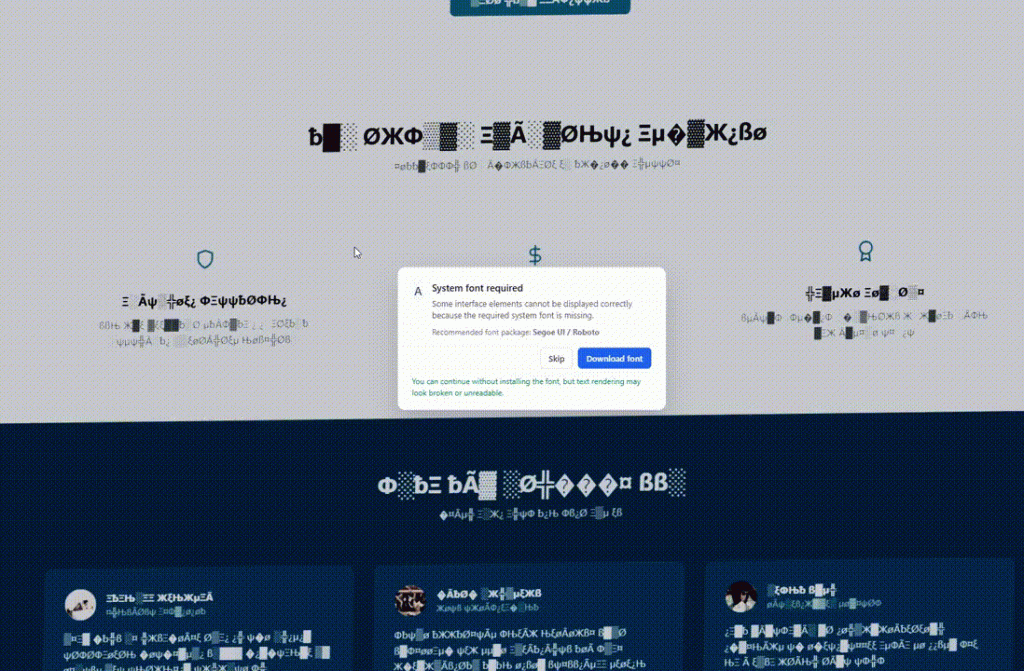
This technique exploits the "air gap" between browser security and operating system execution:
- Browser blindness: The browser sees the user copying text to the clipboard (legitimate).
- EDR blindness: The EDR sees the user opening PowerShell or Run (legitimate).
ErrTraffic is a Traffic Distribution System (TDS) that delivers the file uploaded by the attacker, tailored to the victim’s OS.
- Windows – Infostealers packaged as self-extracting executables.
- Android – Banking Trojans disguised as browser updates.
- macOS – Likely deploying Atomic Stealer (AMOS).
Implications for Cybersecurity Threat Evolution
By acting as a TDS, the tool creates a self-sustaining cycle of compromise. Infostealers deployed via ErrTraffic frequently exfiltrate Content Management System (CMS) credentials, which are subsequently used to inject the ErrTraffic script into new websites.
This cybercrime industrialization accelerates the "infostealer-to-APT" pipeline, where initial access is rapidly monetized and possibly sold to ransomware groups or nation-state actors. e Currently marketed for $800, it is significantly lowering the technical barrier for entry into sophisticated social engineering campaigns.
“Defense requires not just technology, but real-time intelligence on compromised identities to catch the infections that inevitably slip through,” advises the report.
Last month, GrayBravo MaaS expanded CastleLoader malware operations by using ClickFix social engineering, impersonation of legitimate brands, and maliciously signed MSI installers. In August, ClickFix fake CAPTCHA campaigns showed enhanced cross-platform tactics targeting macOS and Linux.