Enhanced StealC Version 2.0 Targets Crypto Wallets, VPNs, Gaming Apps, Browsers
- StealC introduces advanced functionality with the March Version 2.0, focusing on enhanced data collection.
- Critical advancements include advanced payload delivery and RC4 encryption integration.
- It targets cryptocurrency wallets, VPNs, instant messengers, gaming apps, and browsers
StealC is a dangerous information-stealing malware that has seen significant advancements since its debut in 2023. The introduction of StealC V2 in March 2025 added upgrades to its payload delivery system, encryption mechanisms, and control panel functionality.
Cybersecurity experts at Zscaler's ThreatLabz have released an extensive analysis of StealC V2, revealing that it can deploy Microsoft Software Installer (MSI) packages and PowerShell scripts, in addition to executable files.
Newer variants now incorporate robust RC4 encryption for protecting network communications and data exfiltration processes.
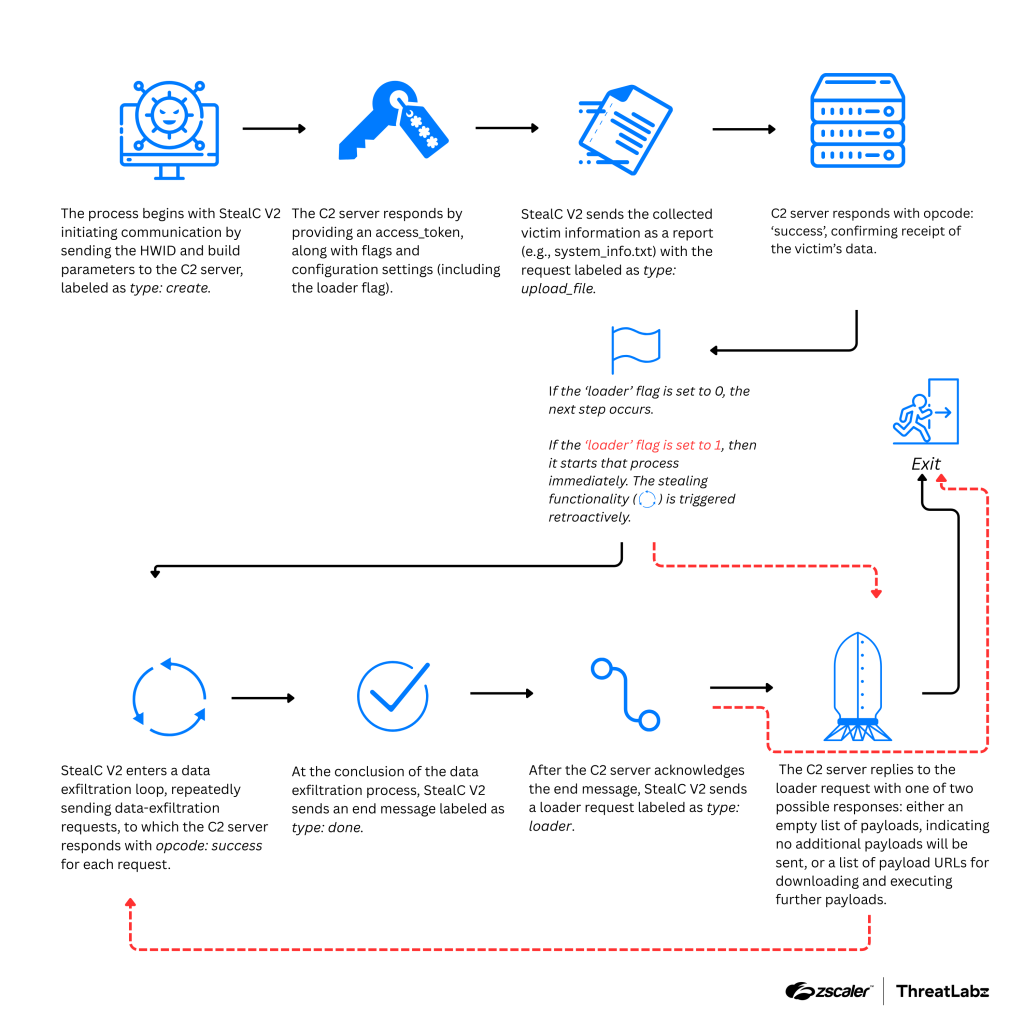
The malware is configured via its command-and-control (C2) server, which dictates operational parameters such as file-grabbing targets (e.g., cryptocurrency wallets or Steam files). The inclusion of RC4 encryption and unique flags in C2 server communications ensures malicious activities are hidden from static signature detections.
Features such as an integrated builder allow operators to customize malware payloads based on geolocation, hardware IDs (HWIDs), and installed software. It allows for credential harvesting, targeting systems like email clients and browsers.
Unified file-grabbing capabilities target cryptocurrency wallets, VPNs, instant messengers, gaming apps, and browsers. Additionally, a multi-monitor screenshot feature enhances surveillance capabilities.
StealC V2 introduces a range of technical improvements that differentiate it from its predecessor, such as improved obfuscation techniques and streamlined C2 communication.
The malware encrypts key string data using Base64 and RC4, with a two-stage deobfuscation process. Migration to a JSON-based network communication protocol ensures data is harder to intercept. Unique response mechanisms, such as randomized parameters, make detection more challenging.
StealC V2 also displays new execution methods, such as MSI packages executed using msiexec.exe with silent installation parameters and remote PowerShell file execution using downloadable scripts.
Notably, V2 has dropped anti-VM functionalities present in Version 1, reshaping its behavioral footprint and eluding some traditional detection approaches.
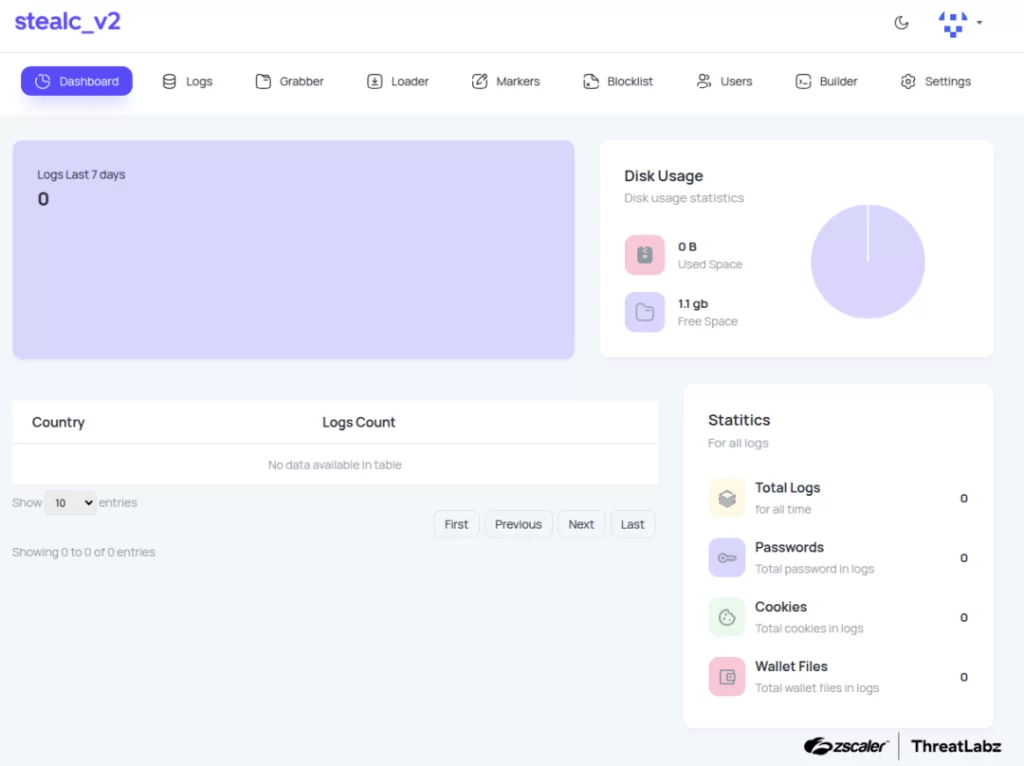
Via the revamped control panel, payload delivery can now be customized by factors such as geolocation or detected installed software on the victim's system, and operators receive updates via Telegram bots, seamlessly monitoring infected systems.
Reportedly deployed through the Amadey botnet, StealC V2 either serves as a payload itself or is used to distribute other malware families. Its adaptability and constant updates reinforce its position as a high-priority threat.
Despite its sophistication, ThreatLabz's rigorous analysis ensures enterprises under Zscaler's protection remain safeguarded. With robust detection mechanisms for variants like Win32/Win64.PWS.Stealc, coverage ensures minimal exposure to this evolving malware.