Emotet Now has a Way to Spread Over Wi-Fi Networks
- Emotet can enumerate nearby Wi-Fi networks and attempt to propagate there like a worm.
- The trojan is using a specialized executable that can brute-force default and weak passwords.
- A good way to stay protected is to use strong passwords of Wi-Fi routers and IoT devices.
It’s been six years since Emotet made its first appearance as a banking trojan that was stealing people’s credentials, and the malware is still going strong. Last year, it was considered one of the most prevalent threats, and 2020 is starting with all the boxes ticked for it to continue playing its malicious role. As reported by Binary Defense, recent Emotet samples show the capacity to exploit the wlanAPI interface to enumerate all Wi-Fi networks in the area. From there, they try to spread to these networks and to infect whatever devices are connected to them.
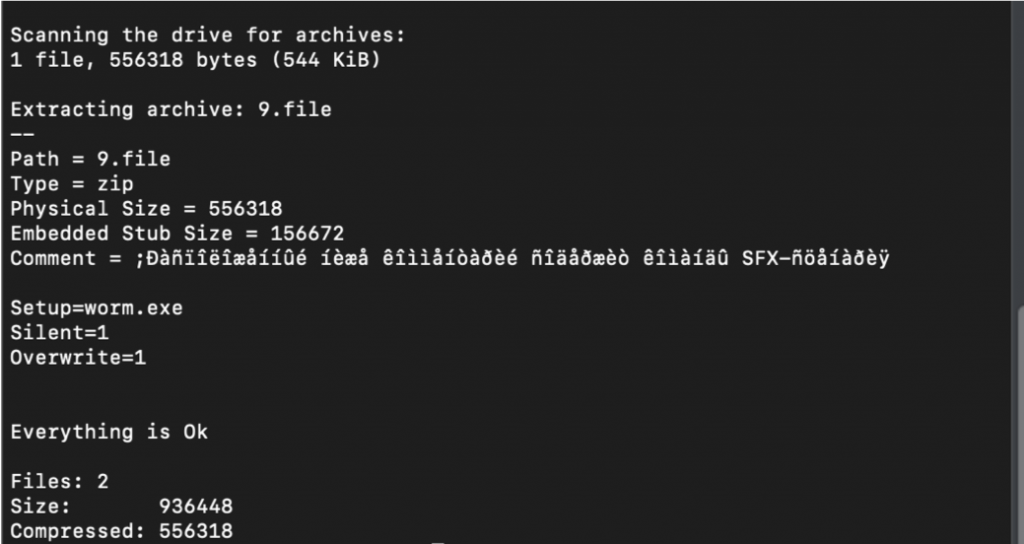
The authors of the notorious trojan have implemented this new capability by basing their communication protocol on Google’s Protobufs. The payload that is fetched by the server for this purpose is a self-extracting RAR file which contains two binary files (worm.exe and service.exe) that are used for the spreading of Emotet through Wi-Fi. The “service.exe” is responsible for the communication with the C2 and the connection requests, as well as the dropping and execution of the Emotet binary. The “worm.exe” is responsible for the propagation, which is the tricky part.
Source: Binary Defense
That binary is profiling the wireless network through wlanAPI.dll to figure out what the potential targets/destinations are. By deploying a system based on the communication protocol described above, it fetches information about the Wi-Fi devices, the description of the hardware, encryption details (AES, WEP), security details (WPA, WPA2, WEP, etc.), signal strength, and even the device’s GUID (globally unique identifier). From there, the only way in is by brute-forcing user passwords. This is another important reminder of why we need to change the default credentials that our modems, routers, and IoT devices come with out of the box, and to use strong passwords instead.
Source: Binary Defense
The researchers point out that the timestamp of the “worm.exe” file dates back to 2018, which can only mean that this Wi-Fi network spreading ability is actually two years old, but we just got to learn about it. Maybe it was underused or simply managed to fly under the radar. Whatever the case, the best practice is to use strong passwords on all devices, implement endpoint monitoring systems, review network logs on a regular basis, and use a network monitoring solution. Emotet’s communications remain unencrypted, so they are recognizable and detectable. Finally, both executables have been in the VirusTotal database for over two years now, so a solid network security suite should catch them immediately.