Email Scam with Social Security Lure Ultimately Installs ScreenConnect RAT, Steals Banking Details
- Cybercriminals use phishing emails masquerading as official SSA notifications to deploy the ScreenConnect RAT.
- The email contains a link to a fake Social Security statement and uses legitimate-looking compromised WordPress domains to bypass email filters.
- The primary objective is financial fraud, as the attackers steal banking information, personal identification numbers, and confidential files.
A sophisticated phishing campaign impersonating the U.S. Social Security Administration (SSA) tricks unsuspecting individuals into installing a dangerous remote access tool (RAT), ScreenConnect.
This campaign, identified by the group name "Molatori," exploits victims' trust in government communication to gain complete control over their devices, according to a recent report from Malwarebytes.
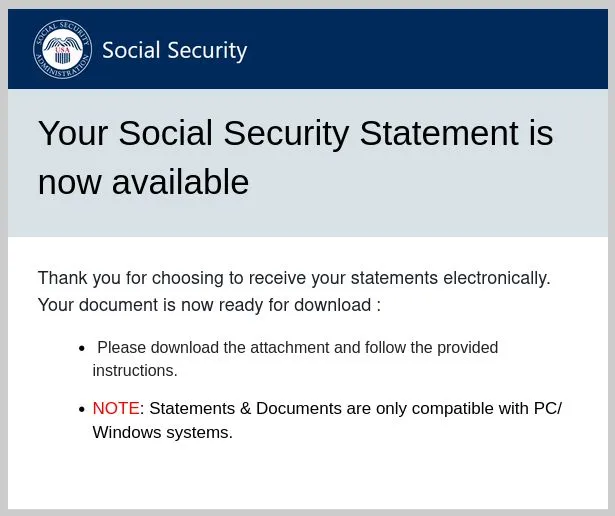
The scam begins with phishing emails masquerading as official SSA notifications. These emails claim that the recipient’s Social Security statement is ready for download and provide a link to access this document.
The email is particularly convincing, often embedding content as images and using legitimate-looking compromised WordPress domains to bypass email filters.
When recipients click on the provided link, they unknowingly download the ScreenConnect client under deceptive filenames, such as ReceiptApirl2025Pdfc.exe or SSAstatment11April.exe. Once installed, the client allows attackers to fully access the victim’s computer.
After obtaining remote access, attackers instantly initiate malicious activities, including the theft of sensitive data like banking information, personal identification numbers, and confidential files.
Malwarebytes researchers note that financial fraud is the primary objective of these scams. The stolen data is subsequently used for furthering identity theft, fraudulent monetary transactions, or unauthorized purchases.
In other news, scammers are creating fraudulent online profiles impersonating IC3 officials, targeting financial fraud victims with promises of lost funds recovery.