ELPACO-Team Ransomware Targets Confluence Servers Through Flaw CVE-2023-22527
- Hackers exploited a template injection vulnerability affecting Atlassian Confluence.
- Security researchers attributed the abuse to a threat actor named ELPACO-Team Ransomware.
- The unpatched flaw allowed remote code execution, resulting in infostealer installation and more.
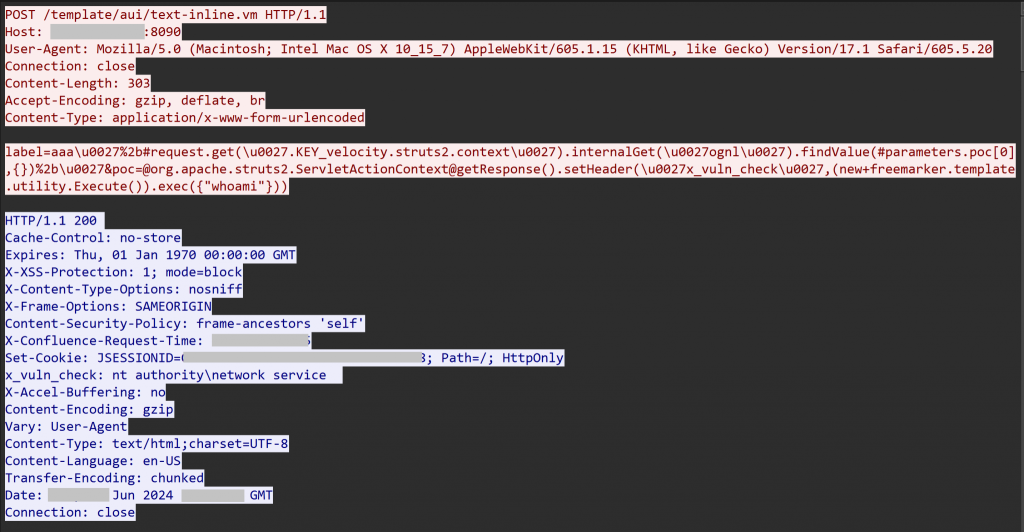
A sophisticated ransomware intrusion exploited an unpatched Atlassian Confluence server. The attackers gained entry to the organization’s network in June 2024 by leveraging CVE-2023-22527, a template injection vulnerability affecting Confluence.
Tools and techniques observed in an in-depth incident analysis published by The DFIR Report are:
- Initial foothold: CVE-2023-22527 exploit chain (Confluence RCE)
- Command and control: Meterpreter via Metasploit, AnyDesk with direct connections
- Credential theft: Mimikatz, ProcessHacker, Impacket Secretsdump
- Lateral movement: Impacket wmiexec, RDP
- Discovery and persistence: NetScan, custom scripts, registry modifications, creation of shadow admin accounts
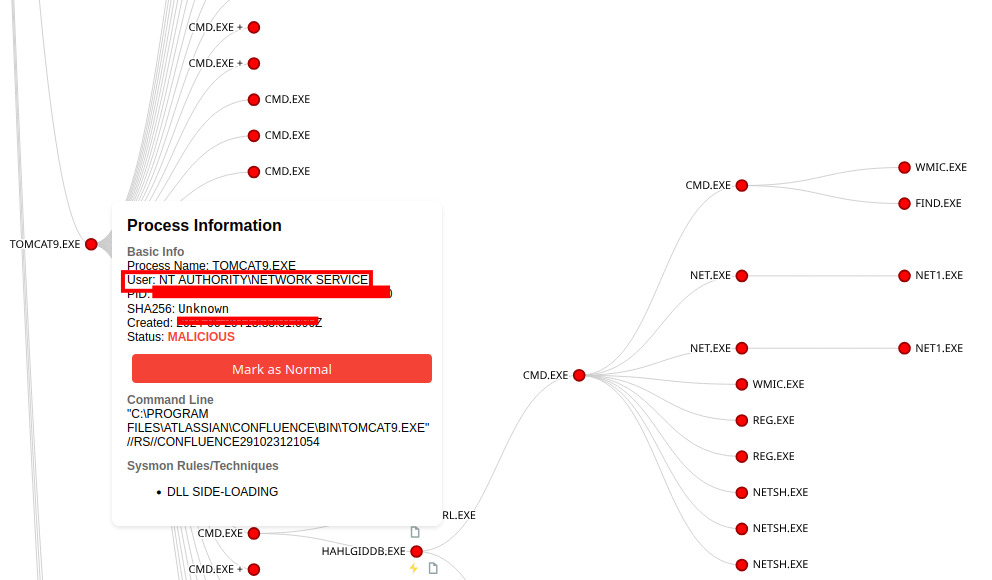
After identifying the exposed server, the threat group executed a series of remote code execution attempts, eventually dropping and launching a Metasploit-based payload to establish a foothold.
The attackers repeatedly installed AnyDesk, created persistent local admin accounts, and enabled RDP access for reliable remote control. Evidence suggests the actions were largely automated, executed through pre-defined scripts.
Multiple tools, such as Mimikatz, ProcessHacker, and Impacket’s Secretsdump, were transferred and staged on the compromised systems to facilitate credential theft.
Exploitation attempts shifted to privilege escalation, including various named pipe impersonation and token duplication techniques. Success was achieved using the RPCSS variant of named pipe impersonation, granting SYSTEM-level access.
Compromised domain administrator credentials enabled the attackers to traverse the network, targeting additional systems via RDP and Impacket-wmiexec.
To maintain stealth, the attackers disabled Windows Defender using registry modifications and installed multiple instances of AnyDesk with preset unattended passwords. Security logs, including event histories, were selectively wiped to impede forensic analysis.
Shortly after achieving broad access, the ELPACO-team ransomware, which has been described as a Mimic variant, was deployed to file and backup servers through direct RDP sessions.
The payload, delivered as a self-extracting 7-Zip archive, encrypted data, and appended a .ELPACO-team file extension.
Notably, while minor data movement over AnyDesk was observed, there was no substantial data exfiltration prior to encryption.