Echelon Fitness Leaks PII of Customers Through Severely Insecure API
- Echelon had a leaky API that exposed very sensitive data about all of its customers.
- The data security investigation also exposed COPPA violations, as Echelon stored children's details without parental consent.
- The company has reportedly ignored the existence of the privacy flaw for months.
Researchers of the PenTestPartners team led by Ken Munro have discovered serious security problems with the API used by Echelon Fitness, a home indoor exercise bike and smart fitness equipment maker. According to the relevant report, Echelon was exposing the sensitive details of its customers, allowing anyone to access it through simple API requests. To make matters worse, the researchers report that these issues were discovered all the way back in January, but Echelon fixed them only last week.
This is very unfortunate when considering how many people relied on exercise machines of this kind during the pandemic and the associated lock-downs that forced people to remain indoors for extended periods of time. Here is what could be harvested from the leaky Echelon API:
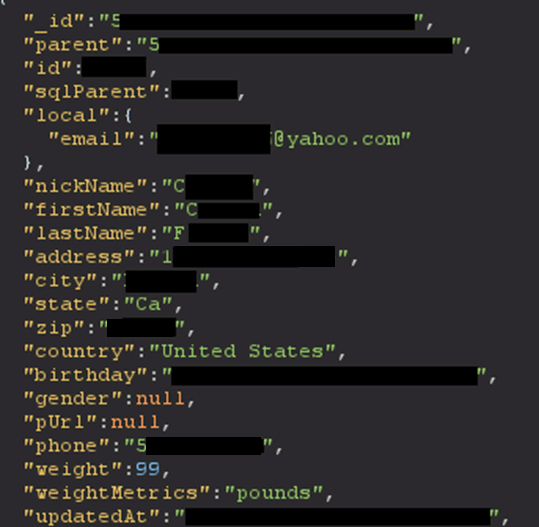
- User IDs
- Locations (address, zip code, city, state. All of which are populated from your payment info.)
- Names
- Email addresses
- Telephone numbers
- Stripe IDS
- Age, Sex, Weight, Birthday
- Equipment serial numbers
- Retailer purchased from
- Subscription dates
- Badges, workout stats, workout history
About ten days ago, we covered a very similar story about Peloton, who is actually a competitor of Echelon. The discovery of Peloton’s security problems came from the same team, and technically, an insecure API was to blame there too. However, the type of data that Echelon exposed was a lot more severe, and the consequences for the customers are now way more troublous.
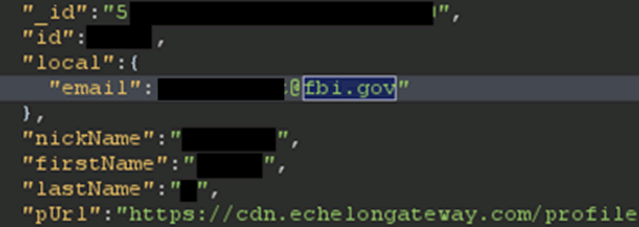
In the process of finding out exactly how bad the flaws were, the researchers abused the user search functionality, finding several “interesting” users in Echolon’s database.
In addition to that, the team found details about users under the age of 13, even though no relevant provisions were in place, so the platform was also violating the COPPA regulations. And on top of that, if a user uploaded a profile image without stripping the metadata first, someone could see their GPS location details, time tags, the device used, etc.
When the PenTestPartners researchers notified Echelon about their findings on January 20, 2021, the company just informed them that the report had been forwarded to the correct department. This was followed by two months of silence despite the researchers' repeated efforts to get an update on the fixing of the issues. Eventually, the team contacted journalist Zack Whittaker, who “convinced” Echelon to finally do something about their leaky API.
The firm answered by claiming that the issue had been fixed on January 21, 2021 (in 24 hours), and their contracted expert could no longer replicate any problems. The researchers, however, maintain that they could still confirm the existence of the issues until May 7, 2021, so they refute Echelon’s claims.