Dutch Police Arrested Members of the “Fraud Family” Phishing Scheme
- The Dutch Police have cuffed two key members of the “Fraud Family” phishing as a service platform.
- The two were developing and selling a sophisticated fork of U-Admin, a Ukrainian phishing kit.
- The hackers who bought access to the sold panels are counted in the several hundred.
The Dutch National Police have arrested two suspects, a 24-year-old software developer and a 15-year-old seller, who are believed to be linked to the “Fraud Family” scheme. The law enforcement authority reached the two fraudsters thanks to key tips provided by researchers of Group-IB, who have published a detailed report on the company’s blog.
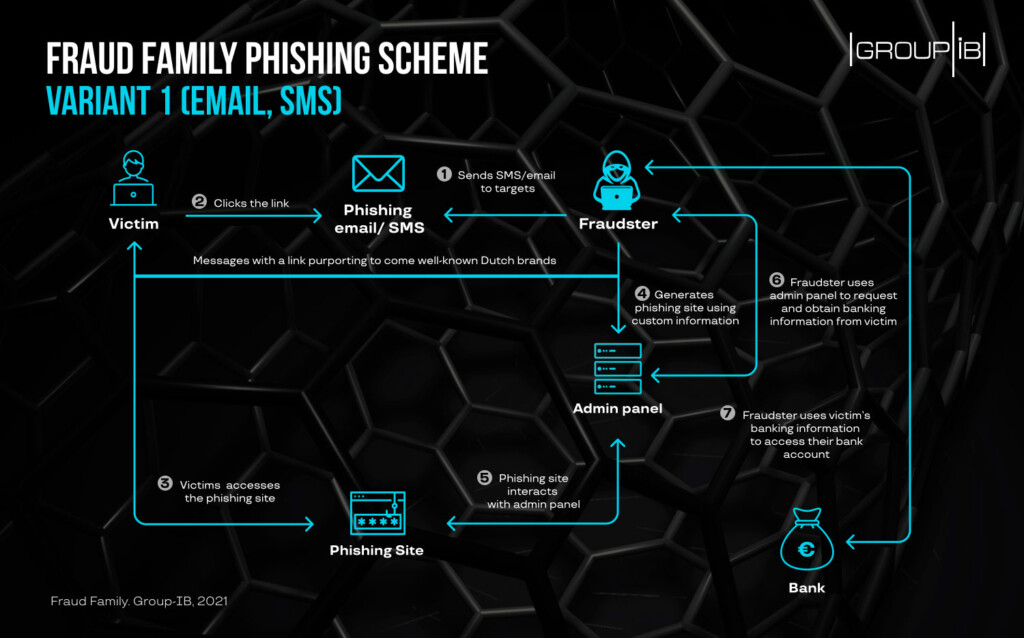
The “Fraud Family” moved as detailed in the following diagram, starting by sending an SMS or email message to the target, which impersonated a financial organization. If the recipient clicked on the embedded link, they were taken to a well-crafted phishing website where they were urged to enter their bank account credentials. The crooks received the username and password pairs right on a live-access panel and then used it to access these bank accounts directly.
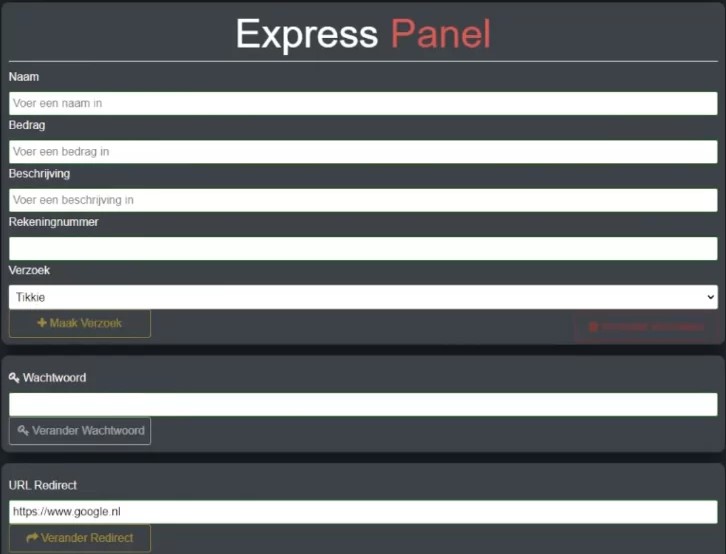
This complete phishing system, including the framework, backend, admin panel, and phishing site themes, was resold to numerous other cybercriminals who targeted mainly people in the Netherlands and Belgium. The cost for using this private phishing framework service was set to €200 per month for the “Express” and €250 per month for the “Reliable” panel option. The difference is that “Express” is simpler, lighter, optimized for use from a mobile phone, and less customizable than the “Reliable” tier.
Group-IB found eight different Telegram channels belonging to the “Fraud Family” gang, which were set up to help other hackers purchase access to the phishing service. In total, the whole network of channels counted 2,000 subscribers, with the most populous one having 640 users. This means the number of hackers using the phishing framework could be measured in the hundreds.
As Anton Ushakov, Deputy Head of the Group-IB’s High-Tech Crime Investigation Department, states:
Upon further investigation and analysis of the sold panels, Group-IB figured that the “Reliable” one is actually a fork of the ‘U-Admin,’ a Ukrainian phishing kit whose author was arrested in Australia last February. It is, however, free of the weaknesses that U-Admin carried, so some code-optimizing work has been put into it. Also, this means the source code for U-Admin has leaked, and more forks could pop up soon on the dark web.